A security analyst is evaluating the security of an online customer banking system. The analyst has a 12-character password for the test account. At the login screen, the analyst is asked to enter the third, eighth, and eleventh characters of the password. Which of the following describes why this request is a security concern? (Choose two.)
- A. The request is evidence that the password is more open to being captured via a keylogger.
- B. The request proves that salt has not been added to the password hash, thus making it vulnerable to rainbow tables.
- C. The request proves the password is encoded rather than encrypted and thus less secure as it can be easily reversed.
- D. The request proves a potential attacker only needs to be able to guess or brute force three characters rather than 12 characters of the password.
- E. The request proves the password is stored in a reversible format, making it readable by anyone at the bank who is given access.
- F. The request proves the password must be in cleartext during transit, making it open to on-path attacks.
A company launched a new service and created a landing page within its website network for users to access the service. Per company policy, all websites must utilize encryption for any authentication pages. A junior network administrator proceeded to use an outdated procedure to order new certificates. Afterward, customers are reporting the following error when accessing a new web page: NET:ERR_CERT_COMMON_NAME_INVALID. Which of the following BEST describes what the administrator should do NEXT?
- A. Request a new certificate with the correct subject alternative name that includes the new websites.
- B. Request a new certificate with the correct organizational unit for the company’s website.
- C. Request a new certificate with a stronger encryption strength and the latest cipher suite.
- D. Request a new certificate with the same information but including the old certificate on the CRL.
A large number of emails have been reported, and a security analyst is reviewing the following information from the emails:
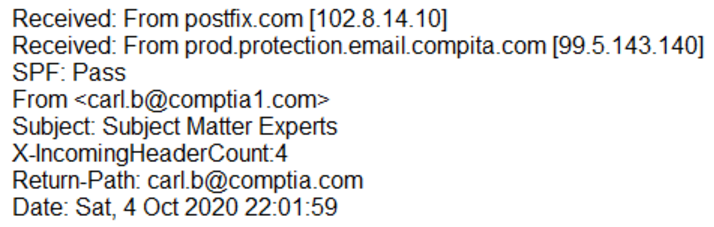
As part of the triage process, which of the following is the FIRST step the analyst should take?
- A. Block the email address carl.b@comptia1.com, as it is sending spam to subject matter experts.
- B. Validate the final ג€Receivedג€ header against the DNS entry of the domain.
- C. Compare the ג€Return-Pathג€ and ג€Receivedג€ fields.
- D. Ignore the emails, as SPF validation is successful, and it is a false positive.
Which of the following is the BEST disaster recovery solution when resources are running in a cloud environment?
- A. Remote provider BCDR
- B. Cloud provider BCDR
- C. Alternative provider BCDR
- D. Primary provider BCDR
An auditor is reviewing the logs from a web application to determine the source of an incident. The web application architecture includes an Internet-accessible application load balancer, a number of web servers in a private subnet, application servers, and one database server in a tiered configuration. The application load balancer cannot store the logs. The following are sample log snippets:
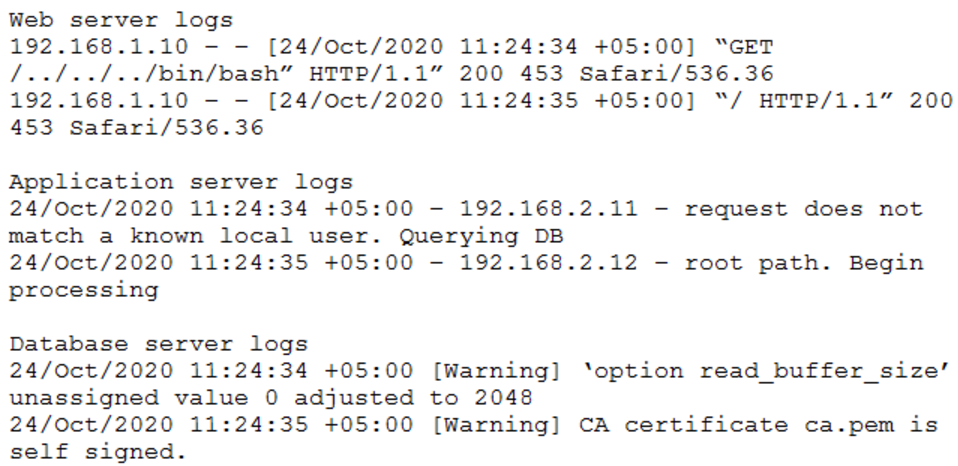
Which of the following should the auditor recommend to ensure future incidents can be traced back to the sources?
- A. Enable the X-Forwarded-For header at the load balancer.
- B. Install a software-based HIDS on the application servers.
- C. Install a certificate signed by a trusted CA.
- D. Use stored procedures on the database server.
- E. Store the value of the $_SERVER[‘REMOTE_ADDR’] received by the web servers.
A security analyst needs to recommend a remediation to the following threat:
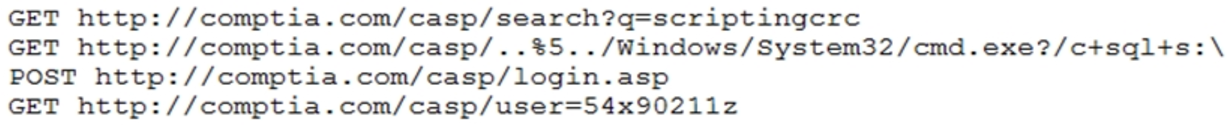
Which of the following actions should the security analyst propose to prevent this successful exploitation?
- A. Patch the system.
- B. Update the antivirus.
- C. Install a host-based firewall.
- D. Enable TLS 1.2.
An organization requires a legacy system to incorporate reference data into a new system. The organization anticipates the legacy system will remain in operation for the next 18 to 24 months. Additionally, the legacy system has multiple critical vulnerabilities with no patches available to resolve them. Which of the following is the BEST design option to optimize security?
- A. Limit access to the system using a jump box.
- B. Place the new system and legacy system on separate VLANs.
- C. Deploy the legacy application on an air-gapped system.
- D. Implement MFA to access the legacy system.
An attacker infiltrated an electricity-generation site and disabled the safety instrumented system. Ransomware was also deployed on the engineering workstation.
The environment has back-to-back firewalls separating the corporate and OT systems. Which of the following is the MOST likely security consequence of this attack?
- A. A turbine would overheat and cause physical harm.
- B. The engineers would need to go to the historian.
- C. The SCADA equipment could not be maintained.
- D. Data would be exfiltrated through the data diodes.
Which of the following is required for an organization to meet the ISO 27018 standard?
- A. All PII must be encrypted.
- B. All network traffic must be inspected.
- C. GDPR equivalent standards must be met.
- D. COBIT equivalent standards must be met.
A company invested a total of $10 million for a new storage solution installed across five on-site datacenters. Fifty percent of the cost of this investment was for solid-state storage. Due to the high rate of wear on this storage, the company is estimating that 5% will need to be replaced per year. Which of the following is the
ALE due to storage replacement?
- A. $50,000
- B. $125,000
- C. $250,000
- D. $500,000
- E. $1,000,000
