A developer wants to develop a secure, external-facing web application. The developer is looking for an online community that produces tools, methodologies, articles, and documentation in the field of web-application security. Which of the following is the BEST option?
- A. ICANN
- B. PCI DSS
- C. OWASP
- D. CSA
- E. NIST
An administrator at a software development company would like to protect the integrity of the company’s applications with digital signatures. The developers report that the signing process keeps failing on all applications. The same key pair used for signing, however, is working properly on the website, is valid, and is issued by a trusted CA. Which of the following is MOST likely the cause of the signature failing?
- A. The NTP server is set incorrectly for the developers.
- B. The CA has included the certificate in its CRL.
- C. The certificate is set for the wrong key usage.
- D. Each application is missing a SAN or wildcard entry on the certificate.
A company created an external, PHP-based web application for its customers. A security researcher reports that the application has the Heartbleed vulnerability.
Which of the following would BEST resolve and mitigate the issue? (Choose two.)
- A. Deploying a WAF signature
- B. Fixing the PHP code
- C. Changing the web server from HTTPS to HTTP
- D. Using SSLv3
- E. Changing the code from PHP to ColdFusion
- F. Updating the OpenSSL library
A security engineer is reviewing a record of events after a recent data breach incident that involved the following:
– A hacker conducted reconnaissance and developed a footprint of the company’s Internet-facing web application assets.
– A vulnerability in a third-party library was exploited by the hacker, resulting in the compromise of a local account.
– The hacker took advantage of the account’s excessive privileges to access a data store and exfiltrate the data without detection.
Which of the following is the BEST solution to help prevent this type of attack from being successful in the future?
- A. Dynamic analysis
- B. Secure web gateway
- C. Software composition analysis
- D. User behavior analysis
- E. Web application firewall
Due to adverse events, a medium-sized corporation suffered a major operational disruption that caused its servers to crash and experience a major power outage. Which of the following should be created to prevent this type of issue in the future?
- A. SLA
- B. BIA
- C. BCM
- D. BCP
- E. RTO
An analyst has prepared several possible solutions to a successful attack on the company. The solutions need to be implemented with the LEAST amount of downtime. Which of the following should the analyst perform?
- A. Implement all the solutions at once in a virtual lab and then run the attack simulation. Collect the metrics and then choose the best solution based on the metrics.
- B. Implement every solution one at a time in a virtual lab, running a metric collection each time. After the collection, run the attack simulation, roll back each solution, and then implement the next. Choose the best solution based on the best metrics.
- C. Implement every solution one at a time in a virtual lab, running an attack simulation each time while collecting metrics. Roll back each solution and then implement the next. Choose the best solution based on the best metrics.
- D. Implement all the solutions at once in a virtual lab and then collect the metrics. After collection, run the attack simulation. Choose the best solution based on the best metrics.
An investigator is attempting to determine if recent data breaches may be due to issues with a company’s web server that offers news subscription services. The investigator has gathered the following data:
• Clients successfully establish TLS connections to web services provided by the server.
• After establishing the connections, most client connections are renegotiated.
• The renegotiated sessions use cipher suite TLS_RSA_WITH_NULL_SHA.
Which of the following is the MOST likely root cause?
- A. The clients disallow the use of modem cipher suites.
- B. The web server is misconfigured to support HTTP/1.1
- C. A ransomware payload dropper has been installed.
- D. An entity is performing downgrade attacks on path.
A security analyst discovered that a database administrator’s workstation was compromised by malware. After examining the logs, the compromised workstation was observed connecting to multiple databases through ODBC. The following query behavior was captured:
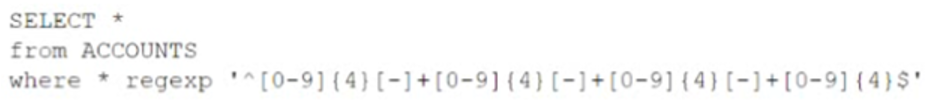
Assuming this query was used to acquire and exfiltrate data, which of the following types of data was compromised, and what steps should the incident response plan contain?
- A. Personal health information; Inform the human resources department of the breach and review the DLP logs.
- B. Account history; Inform the relationship managers of the breach and create new accounts for the affected users.
- C. Customer IDs; Inform the customer service department of the breach and work to change the account numbers.
- D. PAN; Inform the legal department of the breach and look for this data in dark web monitoring.
The Chief Information Officer (CIO) wants to implement enterprise mobility throughout the organization. The goal is to allow employees access to company resources. However, the CIO wants the ability to enforce configuration settings, manage data, and manage both company-owned and personal devices. Which of the following should the CIO implement to achieve this goal?
- A. BYOD
- B. CYOD
- C. COPE
- D. MDM
Which of the following is MOST commonly found in a network SLA contract?
- A. Price for extra services
- B. Performance metrics
- C. Service provider responsibility only
- D. Limitation of liability
- E. Confidentiality and non-disclosure
