A security operations center analyst is investigating anomalous activity between a database server and an unknown external IP address and gathered the following data:
• dbadmin last logged in at 7:30 a.m. and logged out at 8:05 a.m.
• A persistent TCP/6667 connection to the external address was established at 7:55 a.m. The connection is still active.
• Other than bytes transferred to keep the connection alive, only a few kilobytes of data transfer every hour since the start of the connection.
• A sample outbound request payload from PCAP showed the ASCII content: “JOIN #community”.
Which of the following is the MOST likely root cause?
- A. A SQL injection was used to exfiltrate data from the database server.
- B. The system has been hijacked for cryptocurrency mining.
- C. A botnet Trojan is installed on the database server.
- D. The dbadmin user is consulting the community for help via Internet Relay Chat.
Which of the following describes the system responsible for storing private encryption/decryption files with a third party to ensure these files are stored safely?
- A. Key escrow
- B. TPM
- C. Trust models
- D. Code signing
A security administrator has been tasked with hardening a domain controller against lateral movement attacks. Below is an output of running services:
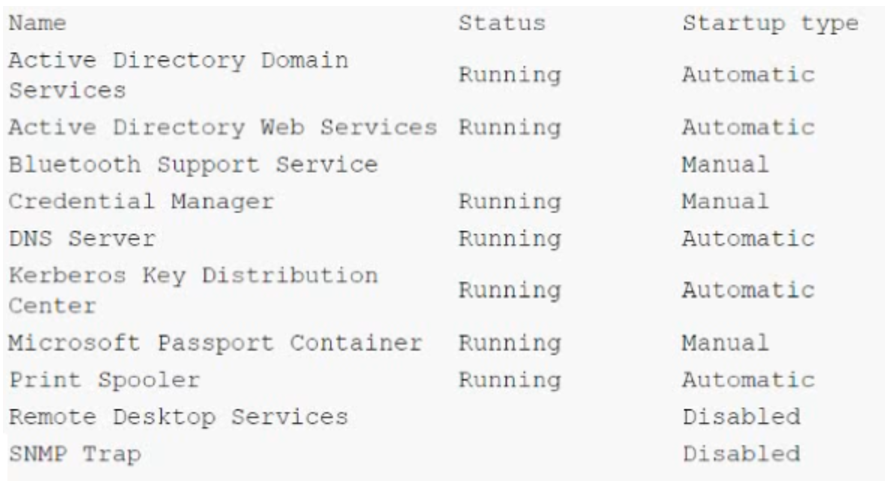
Which of the following configuration changes must be made to complete this task?
- A. Stop the Print Spooler service and set the startup type to disabled.
- B. Stop the DNS Server service and set the startup type to disabled.
- C. Stop the Active Directory Web Services service and set the startup type to disabled.
- D. Stop Credential Manager service and leave the startup type to disabled.
In comparison to other types of alternative processing sites that may be invoked as a part of disaster recovery, cold sites are different because they:
- A. have basic utility coverage, including power and water.
- B. provide workstations and read-only domain controllers.
- C. are generally the least costly to sustain.
- D. are the quickest way to restore business.
- E. are geographically separated from the company’s primary facilities.
A security architect works for a manufacturing organization that has many different branch offices. The architect is looking for a way to reduce traffic and ensure the branch offices receive the latest copy of revoked certificates issued by the CA at the organization’s headquarters location. The solution must also have the lowest power requirement on the CA.
Which of the following is the BEST solution?
- A. Deploy an RA on each branch office.
- B. Use Delta CRLs at the branches.
- C. Configure clients to use OCSP.
- D. Send the new CRLs by using scheduled jobs.
An enterprise is undergoing an audit to review change management activities when promoting code to production. The audit reveals the following:
• Some developers can directly publish code to the production environment.
• Static code reviews are performed adequately.
• Vulnerability scanning occurs on a regularly scheduled basis per policy.
Which of the following should be noted as a recommendation within the audit report?
- A. Implement short maintenance windows.
- B. Perform periodic account reviews.
- C. Implement job rotation.
- D. Improve separation of duties.
An executive has decided to move a company’s customer-facing application to the cloud after experiencing a lengthy power outage at a locally managed service provider’s data center. The executive would like a solution that can be implemented as soon as possible. Which of the following will BEST prevent similar issues when the service is running in the cloud? (Choose two.)
- A. Placing the application instances in different availability zones
- B. Restoring the snapshot and starting the new application instance from a different zone
- C. Enabling autoscaling based on application instance usage
- D. Having several application instances running in different VPCs
- E. Using the combination of block storage and multiple CDNs in each application instance
- F. Setting up application instances in multiple regions
A hospitality company experienced a data breach that included customer PII. The hacker used social engineering to convince an employee to grant a third-party application access to some company documents within a cloud file storage service Which of the following is the BEST solution to help prevent this type of attack in the future?
- A. NGFW for web traffic inspection and activity monitoring
- B. CSPM for application configuration control
- C. Targeted employee training and awareness exercises
- D. CASB for OAuth application permission control
A product manager at a new company needs to ensure the development team produces high-quality code on time. The manager has decided to implement an agile development approach instead of waterfall. Which of the following are reasons to choose an agile development approach? (Choose two.)
- A. The product manager gives the developers more autonomy to write quality code prior to deployment.
- B. An agile approach incorporates greater application security in the development process than a waterfall approach does.
- C. The scope of work is expected to evolve during the lifetime of project development.
- D. The product manager prefers to have code iteratively tested throughout development.
- E. The product manager would like to produce code in linear phases.
- F. Budgeting and creating a timeline for the entire project is often more straightforward using an agile approach rather than waterfall.
An auditor needs to scan documents at rest for sensitive text. These documents contain both text and images. Which of the following software functionalities must be enabled in the DLP solution for the auditor to be able to fully read these documents? (Choose two.)
- A. Document interpolation
- B. Regular expression pattern matching
- C. Optical character recognition functionality
- D. Baseline image matching
- E. Advanced rasterization
- F. Watermarking
