A security analyst is performing a review of a web application. During testing as a standard user, the following error log appears:
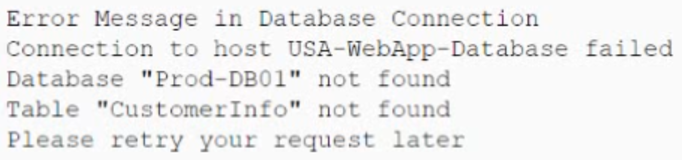
Which of the following BEST describes the analyst’s findings and a potential mitigation technique?
- A. The findings indicate unsecure references. All potential user input needs to be properly sanitized.
- B. The findings indicate unsecure protocols All cookies should be marked as HttpOnly.
- C. The findings indicate information disclosure. The displayed error message should be modified.
- D. The findings indicate a SQL injection. The database needs to be upgraded.
A local university that has a global footprint is undertaking a complete overhaul of its website and associated systems Some of the requirements are:
• Handle an increase in customer demand of resources
• Provide quick and easy access to information
• Provide high-quality streaming media
• Create a user-friendly interface
Which of the following actions should be taken FIRST?
- A. Deploy high-availability web servers.
- B. Enhance network access controls.
- C. Implement a content delivery network.
- D. Migrate to a virtualized environment.
In order to save money, a company has moved its data to the cloud with a low-cost provider. The company did not perform a security review prior to the move; however, the company requires all of its data to be stored within the country where the headquarters is located. A new employee on the security team has been asked to evaluate the current provider against the most important requirements. The current cloud provider that the company is using offers:
• Only multitenant cloud hosting
• Minimal physical security
• Few access controls
• No access to the data center
The following information has been uncovered:
• The company is located in a known floodplain. which flooded last year.
• Government regulations require data to be stored within the country.
Which of the following should be addressed FIRST?
- A. Update the disaster recovery plan to account for natural disasters.
- B. Establish a new memorandum of understanding with the cloud provider.
- C. Establish a new service-level agreement with the cloud provider.
- D. Provision services according to the appropriate legal requirements.
A security administrator needs to implement an X.509 solution for multiple sites within the human resources department. This solution would need to secure all subdomains associated with the domain name of the main human resources web server. Which of the following would need to be implemented to properly secure the sites and provide easier private key management?
- A. Certificate revocation list
- B. Digital signature
- C. Wildcard certificate
- D. Registration authority
- E. Certificate pinning
An organization’s threat team is creating a model based on a number of incidents in which systems in an air-gapped location are compromised. Physical access to the location and logical access to the systems are limited to administrators and select, approved, on-site company employees. Which of the following is the BEST strategy to reduce the risks of data exposure?
- A. NDAs
- B. Mandatory access control
- C. NIPS
- D. Security awareness training
An organization is establishing a new software assurance program to vet applications before they are introduced into the production environment. Unfortunately, many of the applications are provided only as compiled binaries. Which of the following should the organization use to analyze these applications? (Choose two.)
- A. Regression testing
- B. SAST
- C. Third-party dependency management
- D. IDE SAST
- E. Fuzz testing
- F. IAST
Which of the following agreements includes no penalties and can be signed by two entities that are working together toward the same goal?
- A. MOU
- B. NDA
- C. SLA
- D. ISA
Which of the following BEST describes a common use case for homomorphic encryption?
- A. Processing data on a server after decrypting in order to prevent unauthorized access in transit
- B. Maintaining the confidentiality of data both at rest and in transit to and from a CSP for processing
- C. Transmitting confidential data to a CSP for processing on a large number of resources without revealing information
- D. Storing proprietary data across multiple nodes in a private cloud to prevent access by unauthenticated users
A security analyst runs a vulnerability scan on a network administrator’s workstation. The network administrator has direct administrative access to the company’s SSO web portal. The vulnerability scan uncovers critical vulnerabilities with equally high CVSS scores for the user’s browser, OS, email client, and an offline password manager. Which of the following should the security analyst patch FIRST?
- A. Email client
- B. Password manager
- C. Browser
- D. OS
An organization is moving its intellectual property data from on premises to a CSP and wants to secure the data from theft. Which of the following can be used to mitigate this risk?
- A. An additional layer of encryption
- B. A third-party, data integrity monitoring solution
- C. A complete backup that is created before moving the data
- D. Additional application firewall rules specific to the migration
