A software developer is working on a piece of code required by a new software package. The code should use a protocol to verify the validity of a remote identity. Which of the following should the developer implement in the code?
- A. RSA
- B. OCSP
- C. HSTS
- D. CRL
A server in a manufacturing environment is running an end-of-life operating system. The vulnerability management team is recommending that the server be upgraded to a supported operating system, but the ICS software running on the server is not compatible with modem operating systems. Which of the following compensating controls should be implemented to BEST protect the server?
- A. Application allow list
- B. Antivirus
- C. HIPS
- D. Host-based firewall
A firewall administrator needs to ensure all traffic across the company network is inspected. The administrator gathers data and finds the following information regarding the typical traffic in the network:
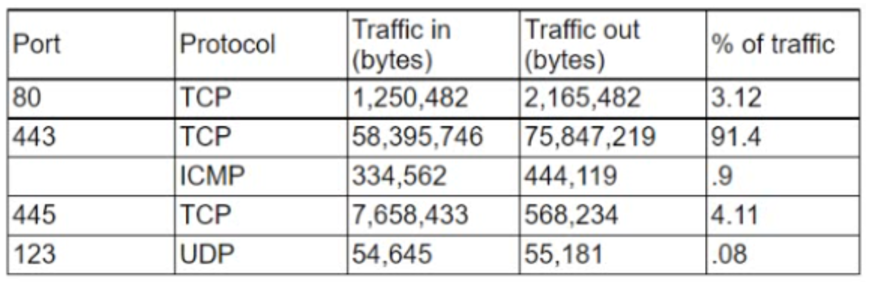
Which of the following is the BEST solution to ensure the administrator can complete the assigned task?
- A. A full-tunnel VPN
- B. Web content filtering
- C. An endpoint DLP solution
- D. SSL/TLS decryption
A city government’s IT director was notified by the city council that the following cybersecurity requirements must be met to be awarded a large federal grant:
• Logs for all critical devices must be retained for 365 days to enable monitoring and threat hunting.
• All privileged user access must be tightly controlled and tracked to mitigate compromised accounts.
• Ransomware threats and zero-day vulnerabilities must be quickly identified.
Which of the following technologies would BEST satisfy these requirements? (Choose three.)
- A. Endpoint protection
- B. Log aggregator
- C. Zero trust network access
- D. PAM
- E. Cloud sandbox
- F. SIEM
- G. NGFW
Company A acquired Company B. During an initial assessment, the companies discover they are using the same SSO system. To help users with the transition. Company A is requiring the following:
• Before the merger is complete, users from both companies should use a single set of usernames and passwords.
• Users in the same departments should have the same set of rights and privileges, but they should have different sets of rights and privileges if they have different IPs.
• Users from Company B should be able to access Company A’s available resources.
Which of the following are the BEST solutions? (Choose two.)
- A. Installing new Group Policy Object policies
- B. Establishing one-way trust from Company B to Company A
- C. Enabling SAML
- D. Implementing attribute-based access control
- E. Installing Company A’s Kerberos systems in Company B’s network
- F. Updating login scripts
Prior to a risk assessment inspection, the Chief Information Officer tasked the systems administrator with analyzing and reporting any configuration issues on the information systems, and then verifying existing security settings. Which of the following would be BEST to use?
- A. SCAP
- B. CVSS
- C. XCCDF
- D. CMDB
An organization is looking to establish more robust security measures by implementing PKI. Which of the following should the security analyst implement when considering mutual authentication?
- A. Perfect forward secrecy on both endpoints
- B. Shared secret for both endpoints
- C. Public keys on both endpoints
- D. A common public key on each endpoint
- E. A common private key on each endpoint
An organization’s senior security architect would like to develop cyber defensive strategies based on standardized adversary techniques, tactics, and procedures commonly observed. Which of the following would BEST support this objective?
- A. OSINT analysis
- B. The Diamond Model of Intrusion Analysis
- C. MITRE ATT&CK
- D. Deep fake generation
- E. Closed-source intelligence reporting
A developer wants to maintain integrity to each module of a program and ensure controls are in place to detect unauthorized code modification. Which of the following would be BEST for the developer to perform? (Choose two.)
- A. Utilize code signing by a trusted third party.
- B. Implement certificate-based authentication.
- C. Verify MD5 hashes.
- D. Compress the program with a password.
- E. Encrypt with 3DES.
- F. Make the DACL read-only.
A security solution uses a sandbox environment to execute zero-day software and collect indicators of compromise. Which of the following should the organization do to BEST take advantage of this solution?
- A. Develop an Nmap plug-in to detect the indicator of compromise.
- B. Update the organization’s group policy.
- C. Include the signature in the vulnerability scanning tool.
- D. Deliver an updated threat signature throughout the EDR system.
