A security analyst has concerns about malware on an endpoint. The malware is unable to detonate by modifying the kernel response to various system calls. As a test, the analyst modifies a Windows server to respond to system calls as if it was a Linux server. In another test, the analyst modifies the operating system to prevent the malware from identifying target files. Which of the following techniques is the analyst MOST likely using?
- A. Honeypot
- B. Deception
- C. Simulators
- D. Sandboxing
Question 262
Users are claiming that a web server is not accessible. A security engineer is unable to view the Internet Services logs for the site. The engineer connects to the server and runs netstat – an and receives the following output:
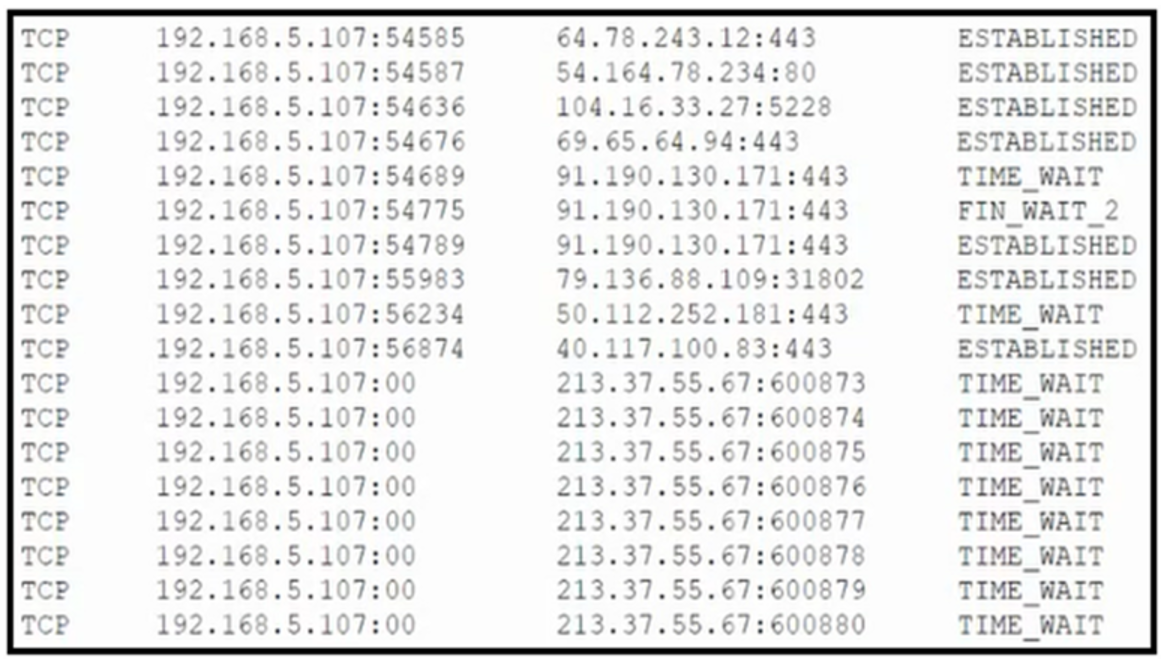
Which of the following is MOST likely happening to the server?
- A. Port scanning
- B. ARP spoofing
- C. Buffer overflow
- D. Denial of service
An architect is designing security scheme for an organization that is concerned about APTs. Any proposed architecture must meet the following requirements:
• Services must be able to be reconstituted quickly from a known-good state.
• Network services must be designed to ensure multiple diverse layers of redundancy.
• Defensive and responsive actions must be automated to reduce human operator demands.
Which of the following designs must be considered to ensure the architect meets these requirements? (Choose three.)
- A. Increased efficiency by embracing advanced caching capabilities
- B. Geographic distribution of critical data and services
- C. Hardened and verified container usage
- D. Emulated hardware architecture usage
- E. Establishment of warm and hot sites for continuity of operations
- F. Heterogeneous architecture
- G. Deployment of IPS services that can identify and block malicious traffic
- H. Implementation and configuration of a SOAR
A company is on a deadline to roll out an entire CRM platform to all users at one time. However, the company is behind schedule due to reliance on third-party vendors. Which of the following development approaches will allow the company to begin releases but also continue testing and development for future releases?
- A. Implement iterative software releases
- B. Revise the scope of the project to use a waterfall approach.
- C. Change the scope of the project to use the spiral development methodology.
- D. Perform continuous integration.
A third-party organization has implemented a system that allows it to analyze customers’ data and deliver analysis results without being able to see the raw data. Which of the following is the organization implementing?
- A. Asynchronous keys
- B. Homomorphic encryption
- C. Data lake
- D. Machine learning
Which of the following communication protocols is used to create PANs with small, low-power digital radios and supports a large number of nodes?
- A. Zigbee
- B. Wi-Fi
- C. CAN
- D. Modbus
- E. DNP3
A software development company is building a new mobile application for its social media platform. The company wants to gain its users’ trust by reducing the risk of on-path attacks between the mobile client and its servers and by implementing stronger digital trust. To support users’ trust, the company has released the following internal guidelines:
• Mobile clients should verity the identity of all social media servers locally.
• Social media servers should improve TLS performance of their certificate status.
• Social media servers should inform the client to only use HTTPS.
Given the above requirements, which of the following should the company implement? (Choose two.)
- A. Quick UDP internet connection
- B. OCSP stapling
- C. Private CA
- D. DNSSEC
- E. CRL
- F. HSTS
- G. Distributed object model
Due to budget constraints, an organization created a policy that only permits vulnerabilities rated high and critical according to CVSS to be fixed or mitigated. A security analyst notices that many vulnerabilities that were previously scored as medium are now breaching higher thresholds. Upon further investigation, the analyst notices certain ratings are not aligned with the approved system categorization.
Which of the following can the analyst do to get a better picture of the risk while adhering to the organization’s policy?
- A. Align the exploitability metrics to the predetermined system categorization.
- B. Align the remediation levels to the predetermined system categorization.
- C. Align the impact subscore requirements to the predetermined system categorization.
- D. Align the attack vectors to the predetermined system categorization.
A cloud engineer is tasked with improving the responsiveness and security of a company’s cloud-based web application. The company is concerned that international users will experience increased latency.
Which of the following is the BEST technology to mitigate this concern?
- A. Caching
- B. Containerization
- C. Content delivery network
- D. Clustering
An organization thinks that its network has active, malicious activity on it. Which of the following capabilities would BEST help to expose the adversary?
- A. Installing a honeypot and other decoys
- B. Expanding SOC functions to include hunting
- C. Enumerating asset configurations
- D. Performing a penetration test
An engineering team has deployed a new VPN service that requires client certificates to be used in order to successfully connect. On iOS devices, however, the following error occurs after importing the .p12 certificate file:
mbedTLS: ca certificate is undefined
Which of the following is the root cause of this issue?
- A. iOS devices have an empty root certificate chain by default.
- B. OpenSSL is not configured to support PKCS#12 certificate files.
- C. The VPN client configuration is missing the CA private key.
- D. The iOS keychain imported only the client public and private keys.
