A security engineer has been informed by the firewall team that a specific Windows workstation is part of a command-and-control network. The only information the security engineer is receiving is that the traffic is occurring on a non-standard port (TCP 40322). Which of the following commands should the security engineer use FIRST to find the malicious process?
- A. tcpdump
- B. netstat
- C. tasklist
- D. traceroute
- E. ipconfig
In a shared responsibility model for PaaS, which of the following is a customer’s responsibility?
- A. Network security
- B. Physical security
- C. OS security
- D. Host infrastructure
A security engineer notices the company website allows users to select which country they reside in, such as the following example:
https://mycompany.com/main.php?Country=US
Which of the following vulnerabilities would MOST likely affect this site?
- A. SQL injection
- B. Remote file inclusion
- C. Directory traversal
- D. Unsecure references
A bank has multiple subsidiaries that have independent infrastructures. The bank’s support teams manage all these environments and want to use a single set of credentials. Which of the following is the BEST way to achieve this goal?
- A. SSO
- B. Federation
- C. Cross-domain
- D. Shared credentials
A SaaS startup is maturing its DevSecOps program and wants to identify weaknesses earlier in the development process in order to reduce the average time to identify serverless application vulnerabilities and the costs associated with remediation. The startup began its early security testing efforts with DAST to cover public-facing application components and recently implemented a bug bounty program. Which of the following will BEST accomplish the company’s objectives? (Choose two.)
- A. IAST
- B. RASP
- C. SAST
- D. SCA
- E. WAF
- F. CMS
Which of the following indicates when a company might not be viable after a disaster?
- A. Maximum tolerable downtime
- B. Recovery time objective
- C. Mean time to recovery
- D. Annual loss expectancy
During an incident, an employee’s web traffic was redirected to a malicious domain. The workstation was compromised, and the attacker was able to modify sensitive data from the company file server. Which of the following solutions would have BEST prevented the initial compromise from happening? (Choose two.)
- A. DNSSEC
- B. FIM
- C. Segmentation
- D. Firewall
- E. DLP
- F. Web proxy
A software company wants to build a platform by integrating with another company’s established product. Which of the following provisions would be MOST important to include when drafting an agreement between the two companies?
- A. Data sovereignty
- B. Shared responsibility
- C. Source code escrow
- D. Safe harbor considerations
A security administrator sees several hundred entries in a web server security log that are similar to the following:
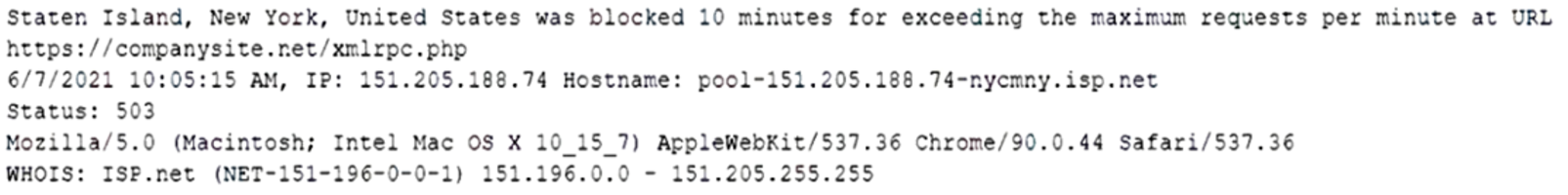
The network source varies, but the URL, status, and user agent are the same. Which of the following would BEST protect the web server without blocking legitimate traffic?
- A. Replace the file xmlrpc.php with a honeypot form to collect further IOCs.
- B. Automate the addition of bot IP addresses into a deny list for the web host.
- C. Script the daily collection of the WHOIS ranges to add to the WAF as a denied ACL.
- D. Block every subnet that is identified as having a bot that is a source of the traffic.
A new database application was added to a company’s hosted VM environment. Firewall ACLs were modified to allow database users to access the server remotely. The company’s cloud security broker then identified abnormal from a database user on-site. Upon further investigation, the security team noticed the user ran code on a VM that provided access to the hypervisor directly and access to other sensitive data.
Which of the following should the security team
do to help mitigate future attacks within the VM environment? (Choose two.)
- A. Install the appropriate patches.
- B. Install perimeter NGFW.
- C. Configure VM isolation.
- D. Deprovision database VM.
- E. Change the user’s access privileges.
- F. Update virus definitions on all endpoints.
