A Chief Security Officer (CSO) is concerned about the number of successful ransomware attacks that have hit the company. The data indicates most of the attacks came through a fake email. The company has added training, and the CSO now wants to evaluate whether the training has been successful. Which of the following should the CSO implement?
- A. Simulating a spam campaign
- B. Conducting a sanctioned vishing attack
- C. Performing a risk assessment
- D. Executing a penetration test
A company hosts a large amount of data in blob storage for its customers. The company recently had a number of issues with this data being prematurely deleted before the scheduled backup processes could be completed. The management team has asked the security architect for a recommendation that allows blobs to be deleted occasionally, but only after a successful backup. Which of the following solutions will BEST meet this requirement?
- A. Mirror the blobs at a local data center.
- B. Enable fast recovery on the storage account.
- C. Implement soft delete for blobs.
- D. Make the blob immutable.
To save time, a company that is developing a new VPN solution has decided to use the OpenSSL library within its proprietary software. Which of the following should the company consider to maximize risk reduction from vulnerabilities introduced by OpenSSL?
- A. Include stable, long-term releases of third-party libraries instead of using newer versions.
- B. Ensure the third-party library implements the TLS and disable weak ciphers.
- C. Compile third-party libraries into the main code statically instead of using dynamic loading.
- D. Implement an ongoing, third-party software and library review and regression testing.
An organization recently completed a security controls assessment. The results highlighted the following vulnerabilities:
• Out-of-date definitions
• Misconfigured operating systems
• An inability to detect active attacks
• Unimpeded access to critical servers’ USB ports
Which of the following will most likely reduce the risks that were identified by the assessment team?
- A. Install EDR on endpoints, configure group policy, lock server room doors, and install a camera system with guards watching 24/7.
- B. Create an information security program that addresses user training, perform weekly audits of user workstations, and utilize a centralized configuration management program.
- C. Update antivirus definitions, install NGFW with logging enabled, use USB port lockers, and run SCAP scans weekly.
- D. Implement a vulnerability management program and a SIEM tool with alerting, install a badge system with zones, and restrict privileged access.
SIMULATION
–
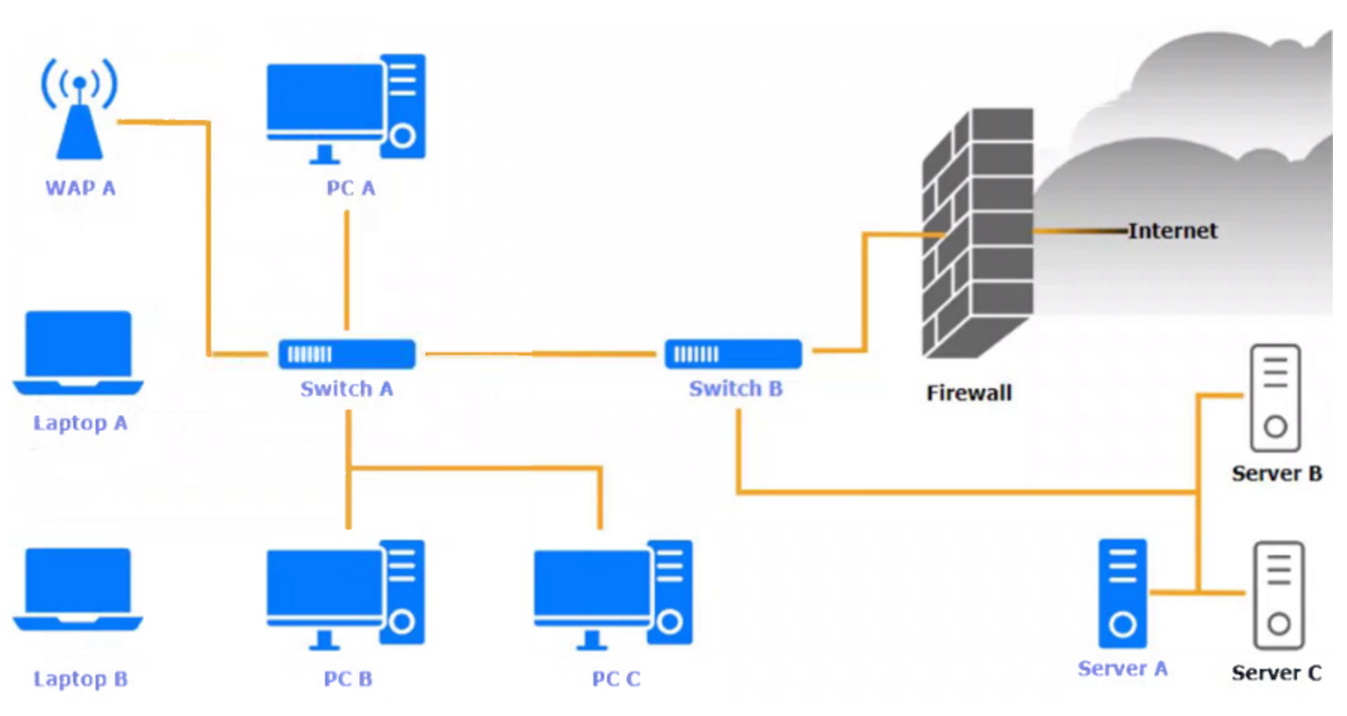
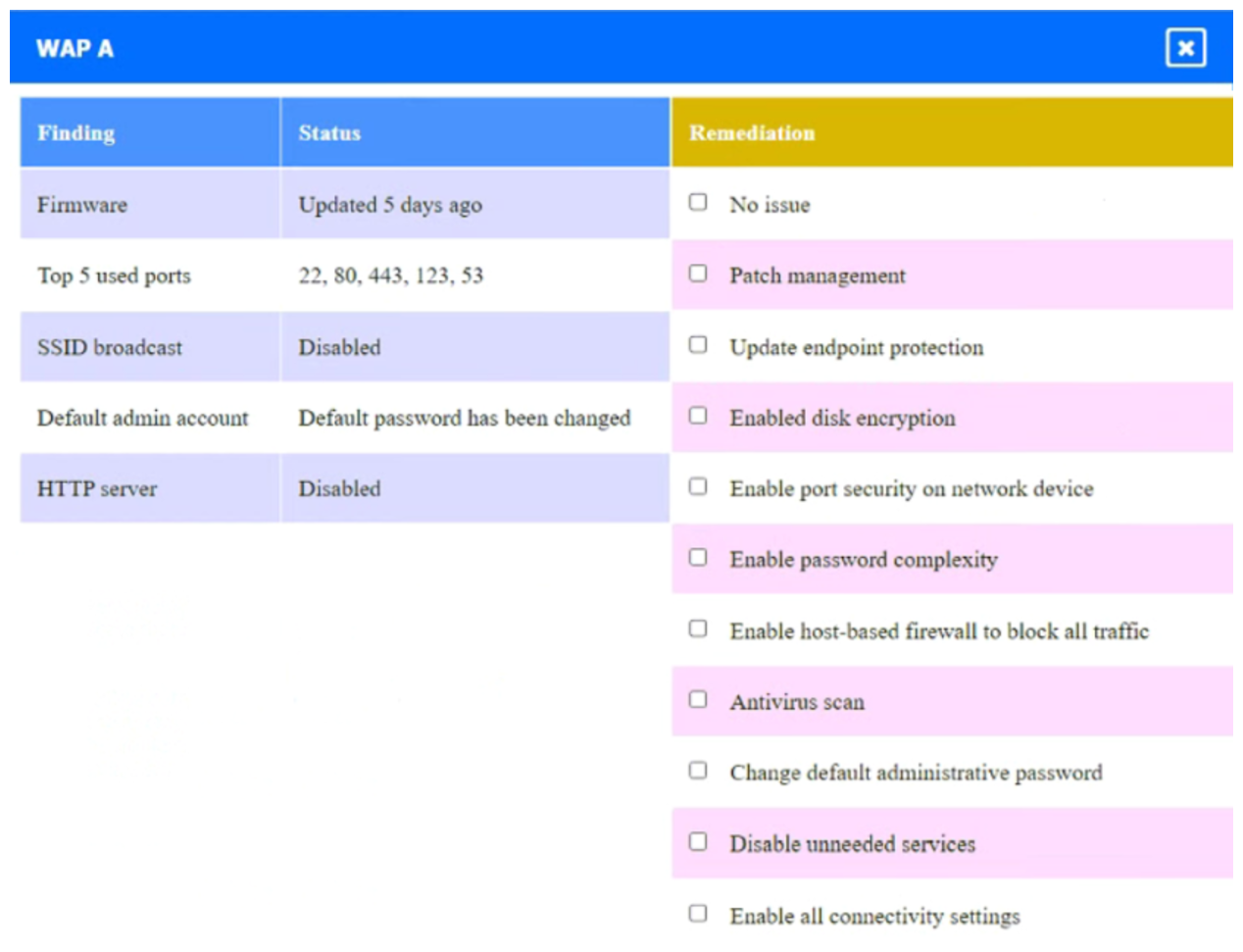
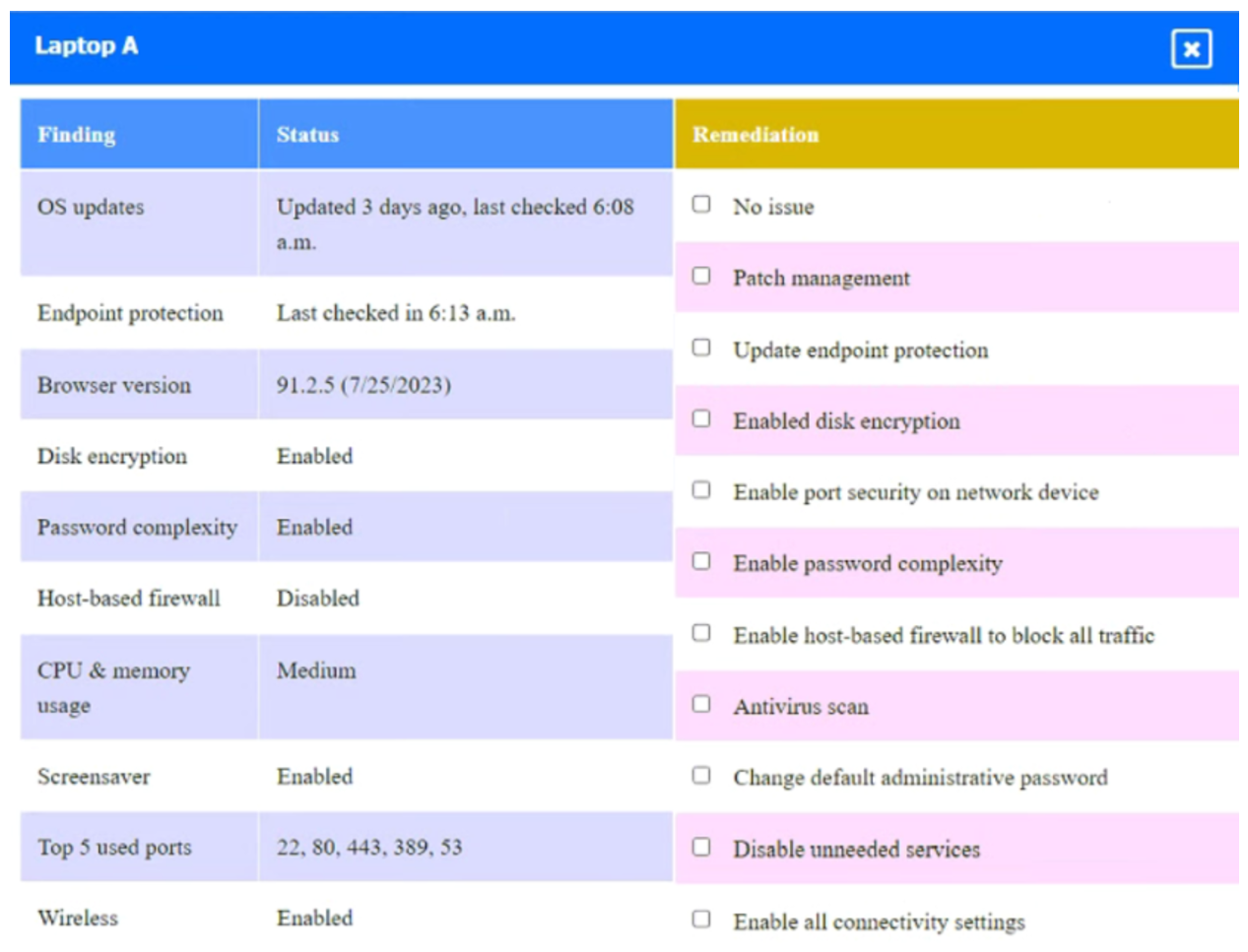
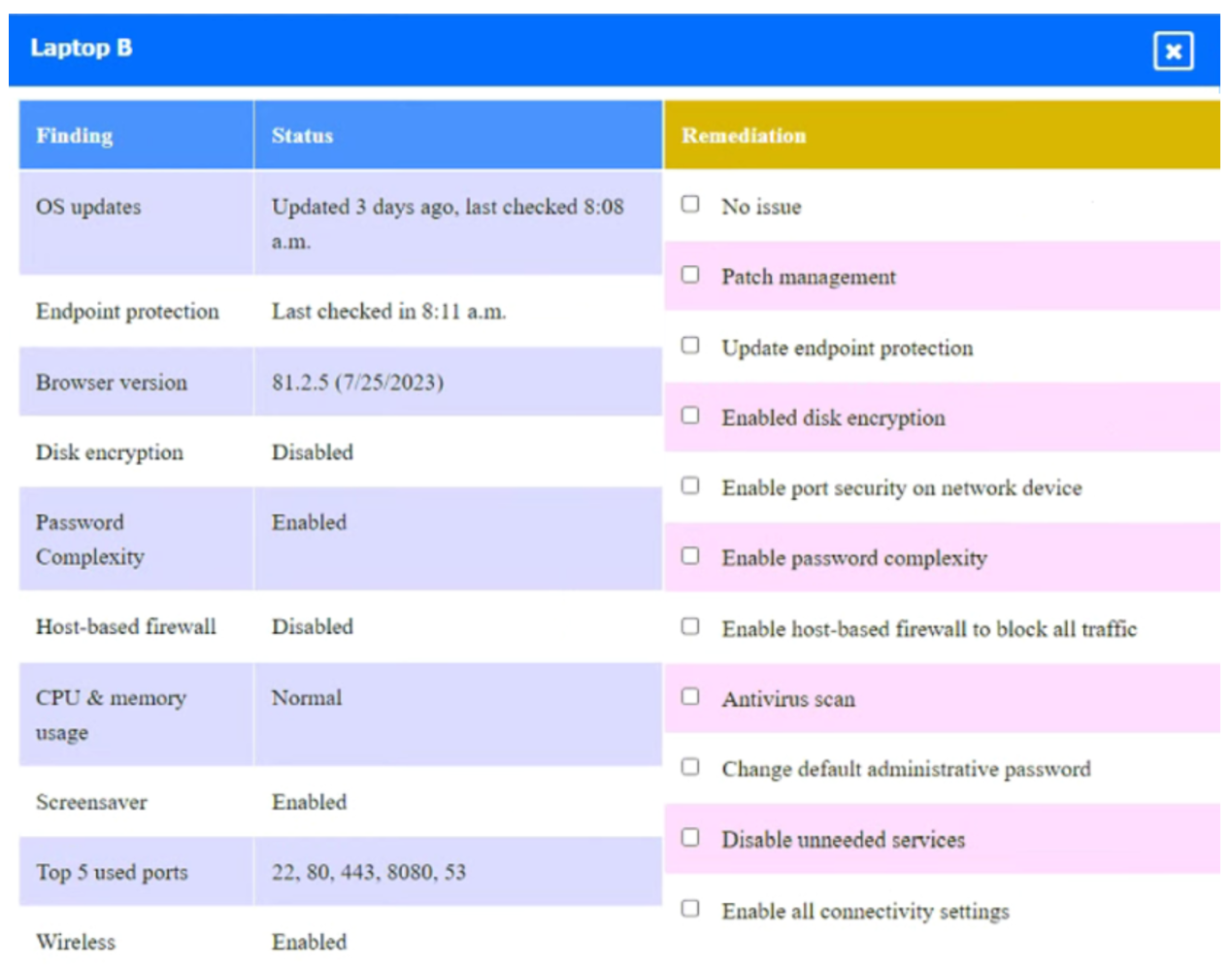
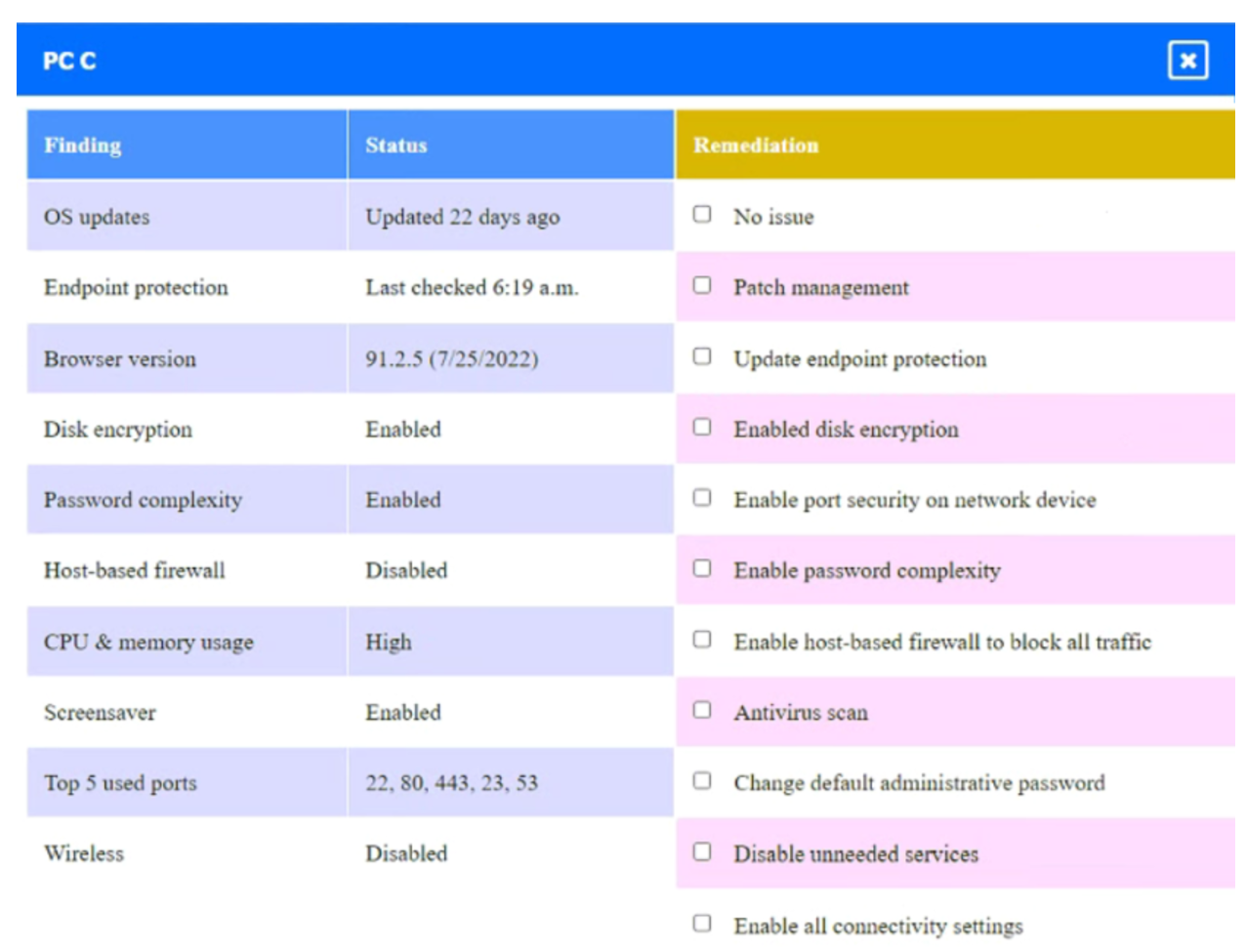
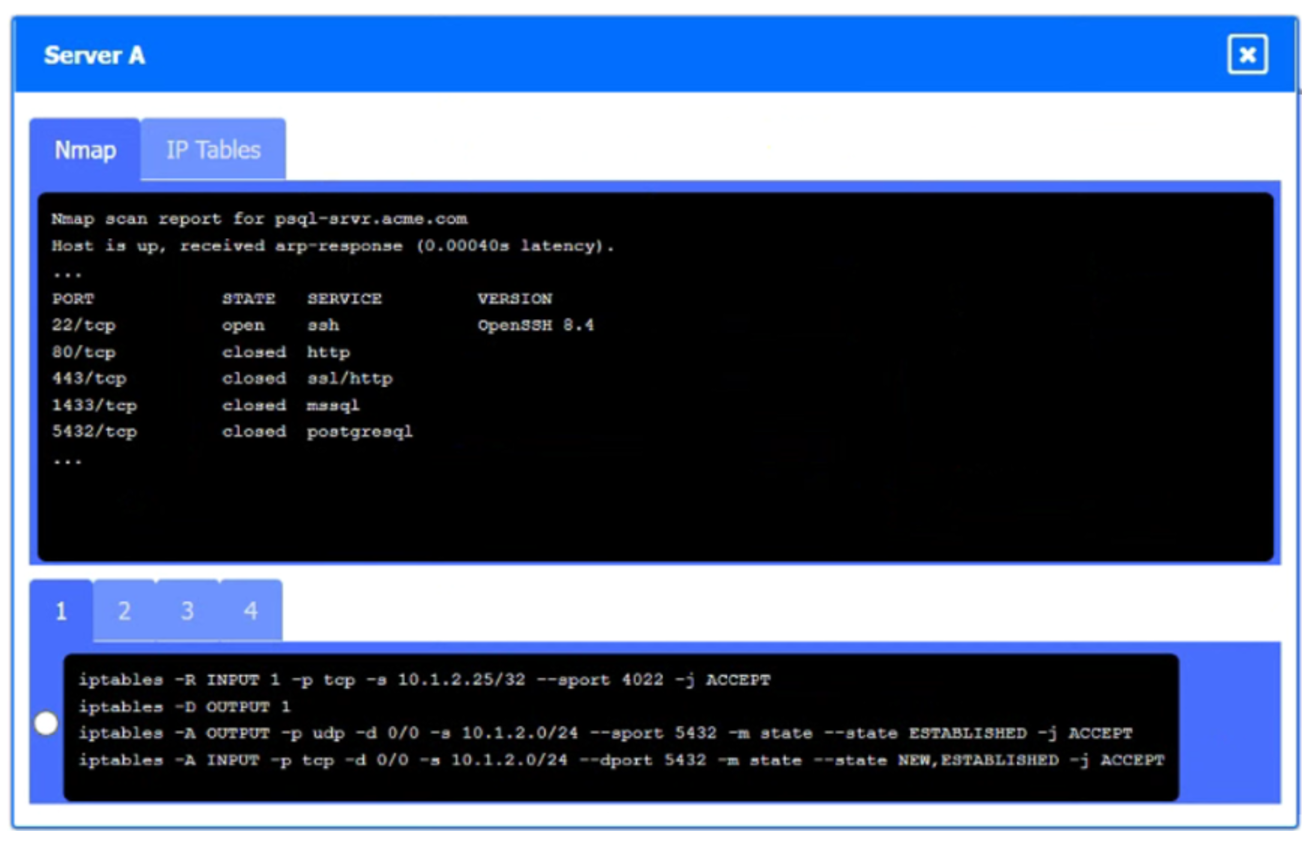
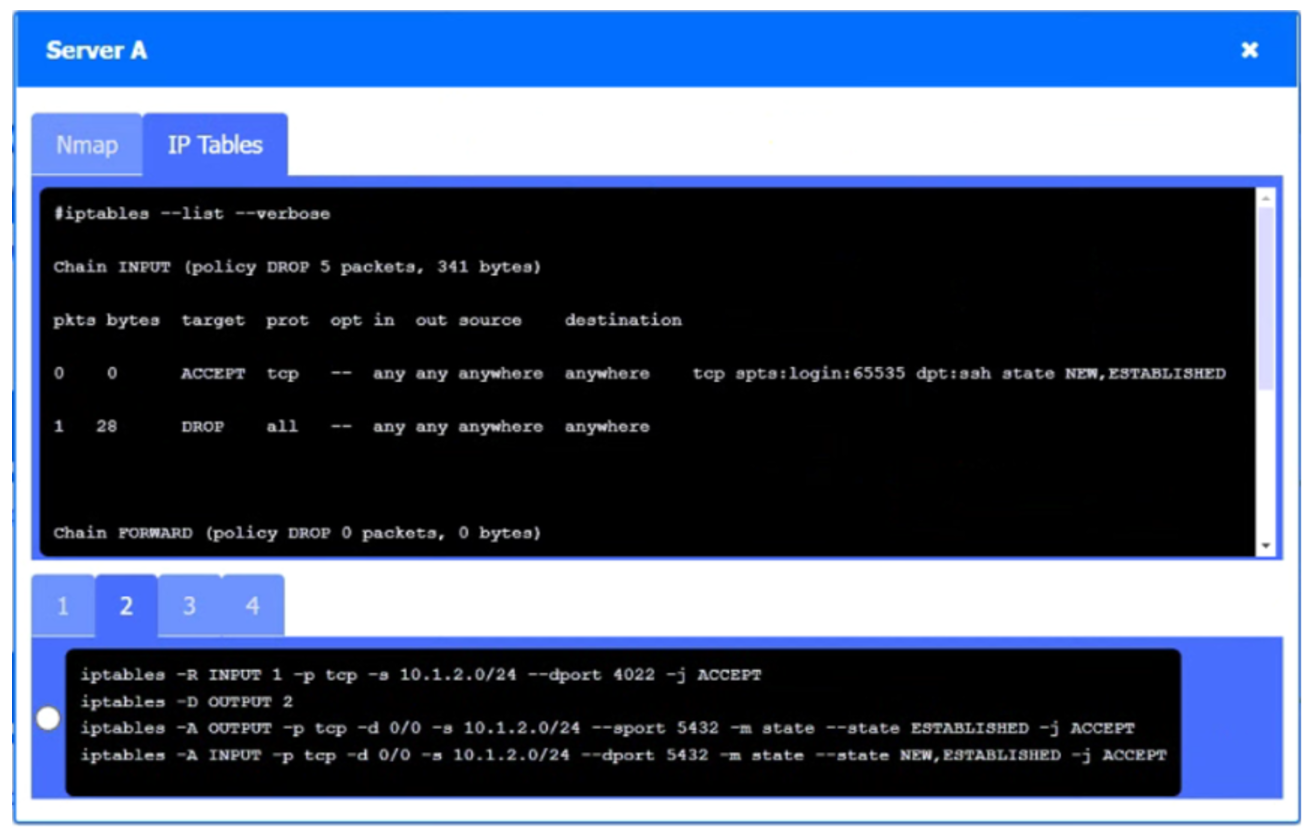
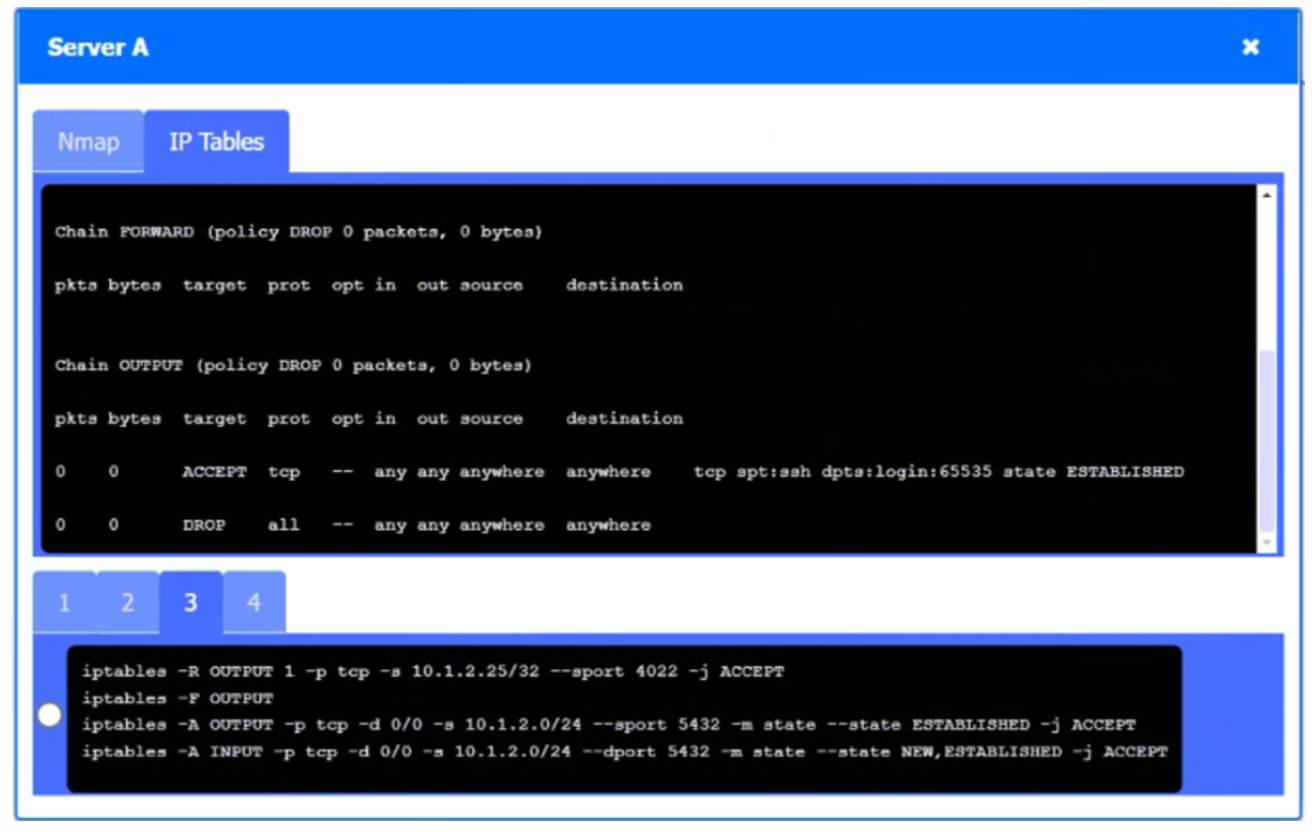
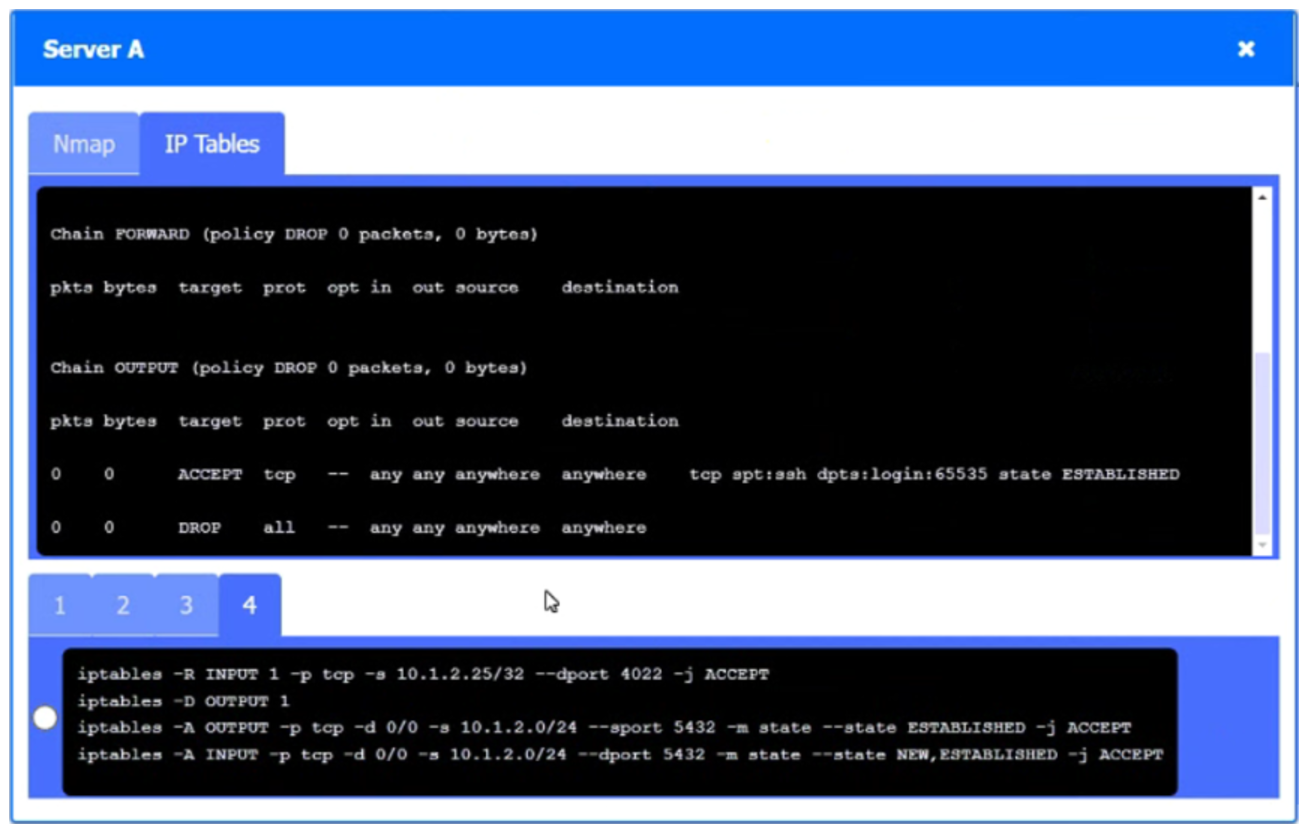
A security engineer needs to review the configurations of several devices on the network to meet the following requirements:
• The PostgreSQL server must only allow connectivity in the 10.1.2.0/24 subnet.
• The SSH daemon on the database server must be configured to listen to port 4022.
• The SSH daemon must only accept connections from a single workstation.
• All host-based firewalls must be disabled on all workstations.
• All devices must have the latest updates from within the past eight days.
• All HDDs must be configured to secure data at rest.
• Cleartext services are not allowed.
• All devices must be hardened when possible.
INSTRUCTIONS
–
Click on the various workstations and network devices to review the posture assessment results. Remediate any possible issues or indicate that no issue is found.
Click on Server A to review output data. Select commands in the appropriate tab to remediate connectivity problems to the PostgreSQL database via SSH.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
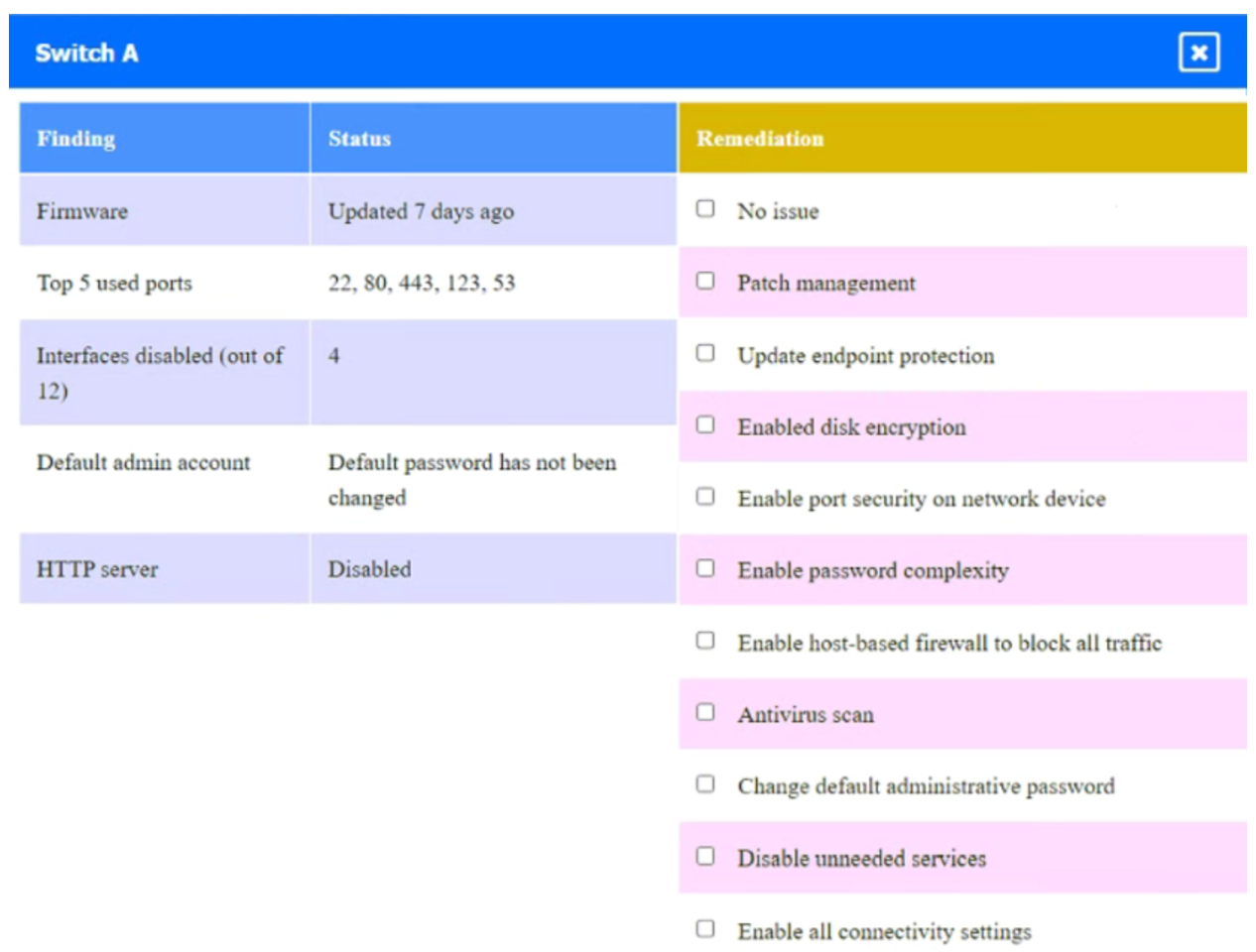
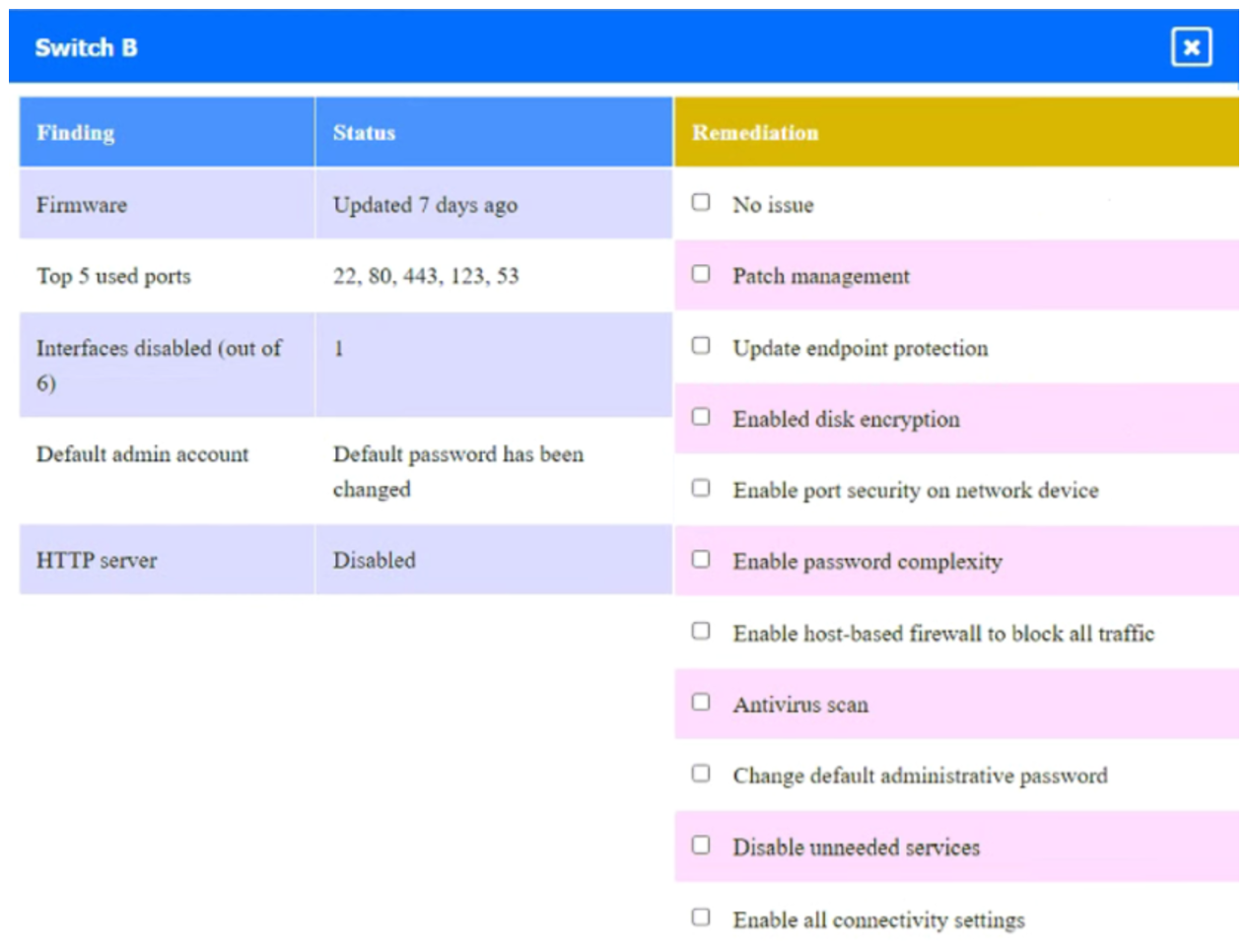
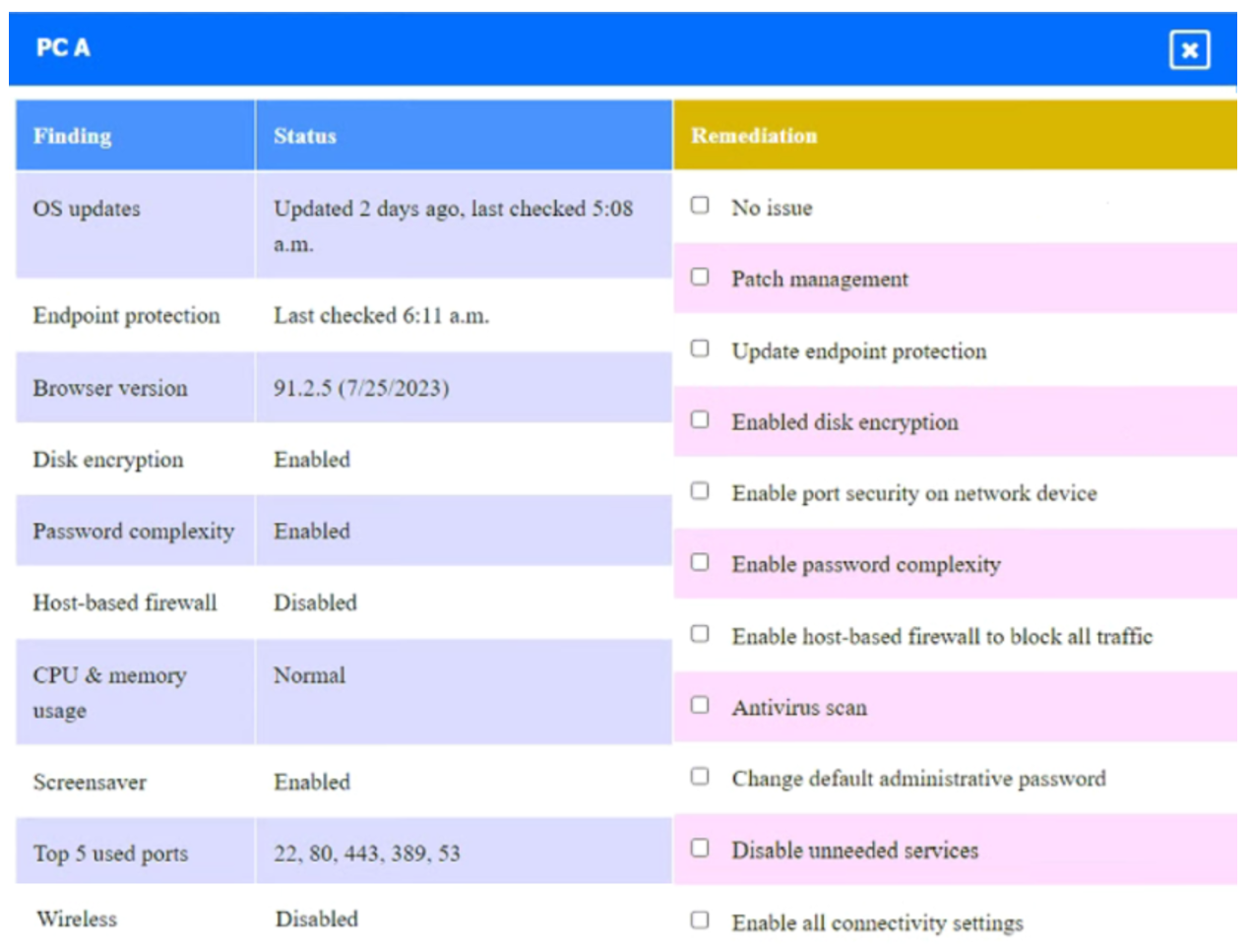
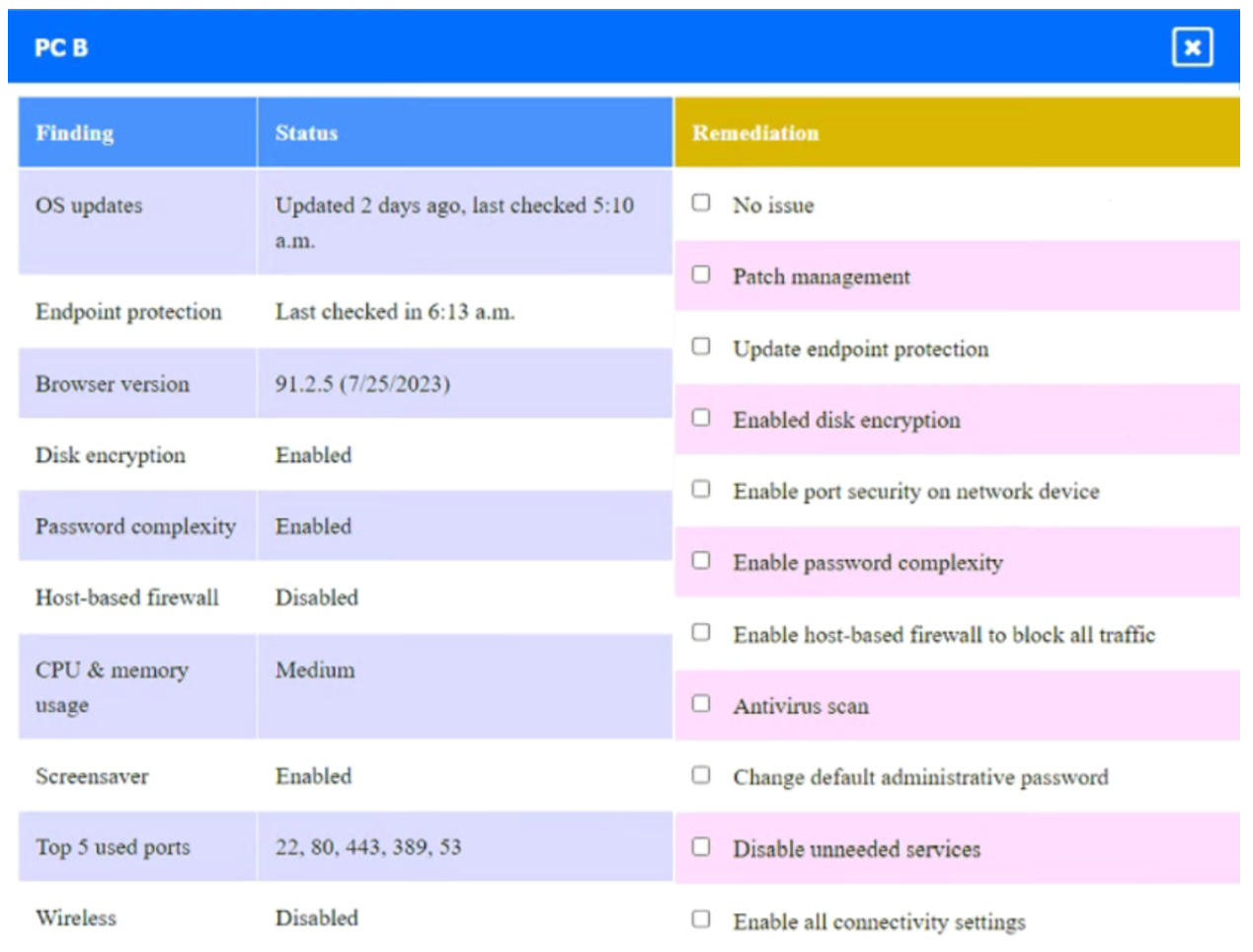
Answer :

A new, online file hosting service is being offered. The service has the following security requirements:
• Threats to customer data integrity and availability should be remediated first.
• The environment should be dynamic to match increasing customer demands.
• The solution should not interfere with customers’ ability to access their data at anytime.
• Security analysts should focus on high-risk items.
Which of the following would BEST satisfy the requirements?
- A. Expanding the use of IPS and NGFW devices throughout the environment
- B. Increasing the number of analysts to identify risks that need remediation
- C. Implementing a SOAR solution to address known threats
- D. Integrating enterprise threat feeds in the existing SIEM
Due to internal resource constraints, the management team has asked the principal security architect to recommend a solution that shifts most of the responsibility for application-level controls to the cloud provider. In the shared responsibility model, which of the following levels of service meets this requirement?
- A. IaaS
- B. SaaS
- C. FaaS
- D. PaaS
In comparison with traditional on-premises infrastructure configurations, defining ACLs in a CSP relies on:
- A. cloud-native applications.
- B. containerization.
- C. serverless configurations.
- D. software-defined networking.
- E. secure access service edge.
HOTSPOT
–
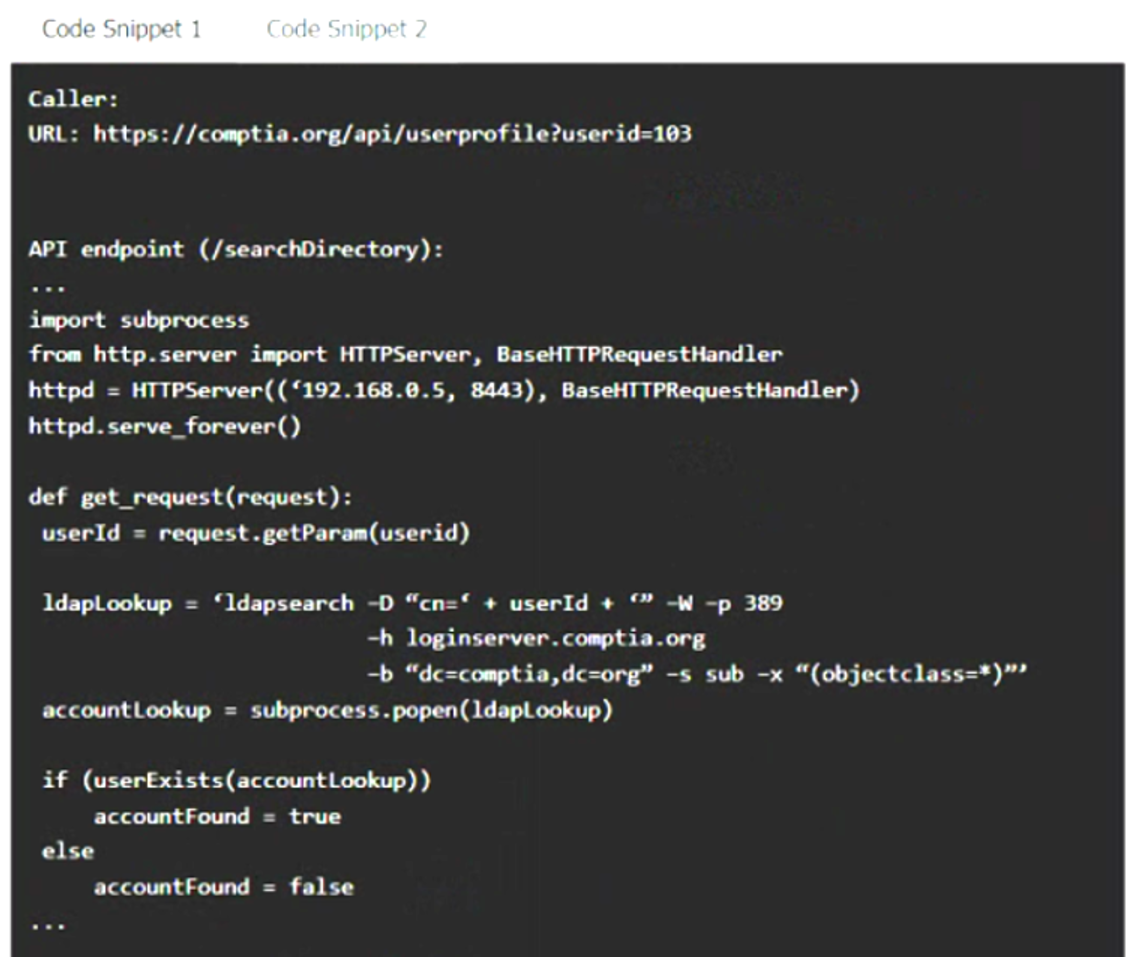
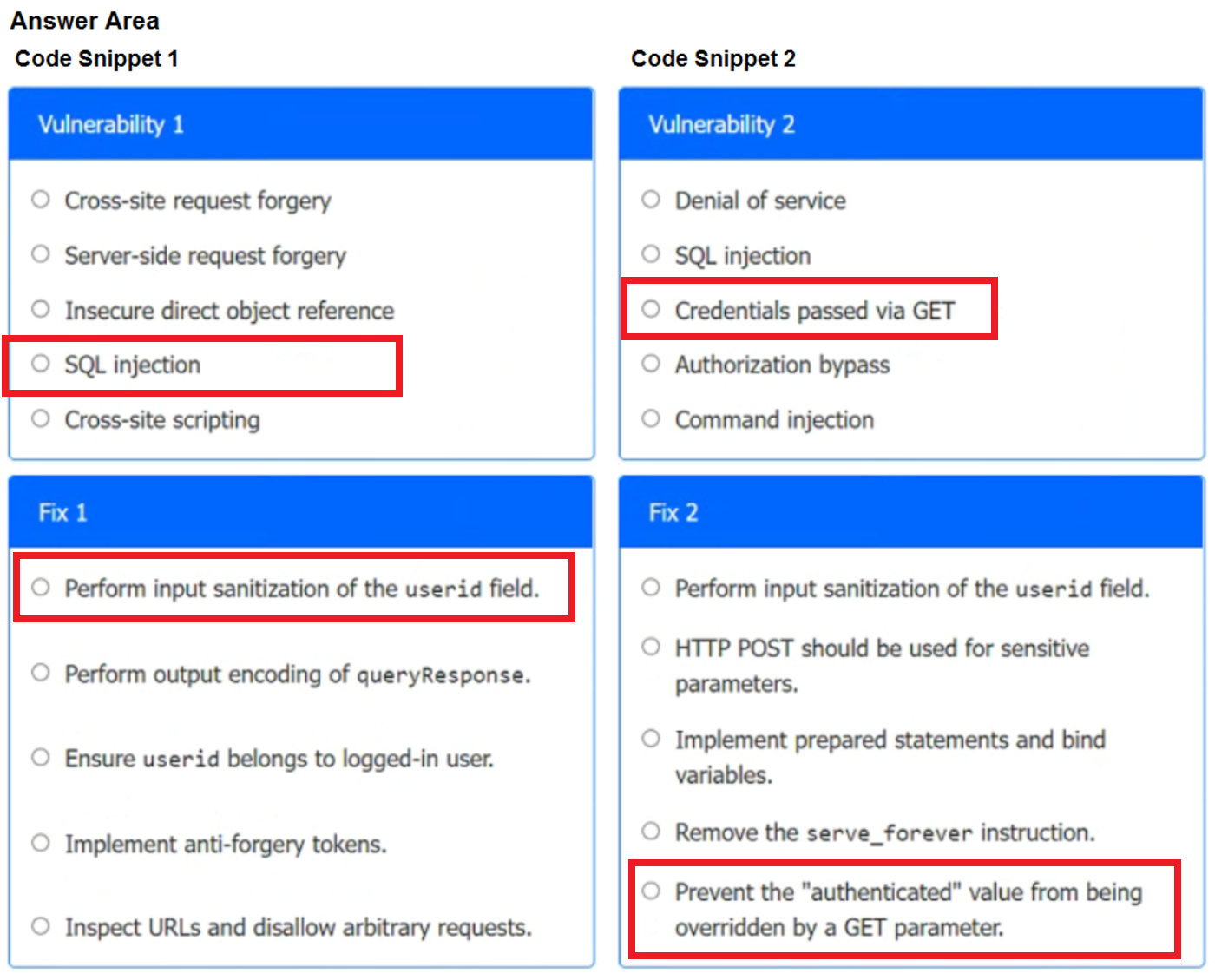
A product development team has submitted code snippets for review prior to release.
INSTRUCTIONS
–
Analyze the code snippets, and then select one vulnerability, and one fix for each code snippet.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Code Snippet 1
–
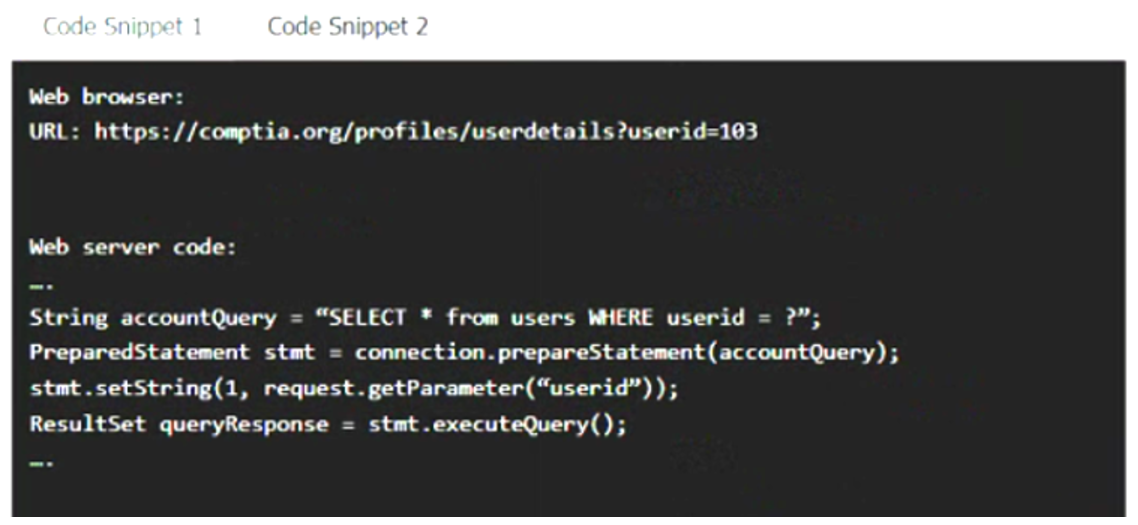
Code Snippet 2
–

A pharmaceutical company was recently compromised by ransomware. Given the following EDR output from the process investigation:
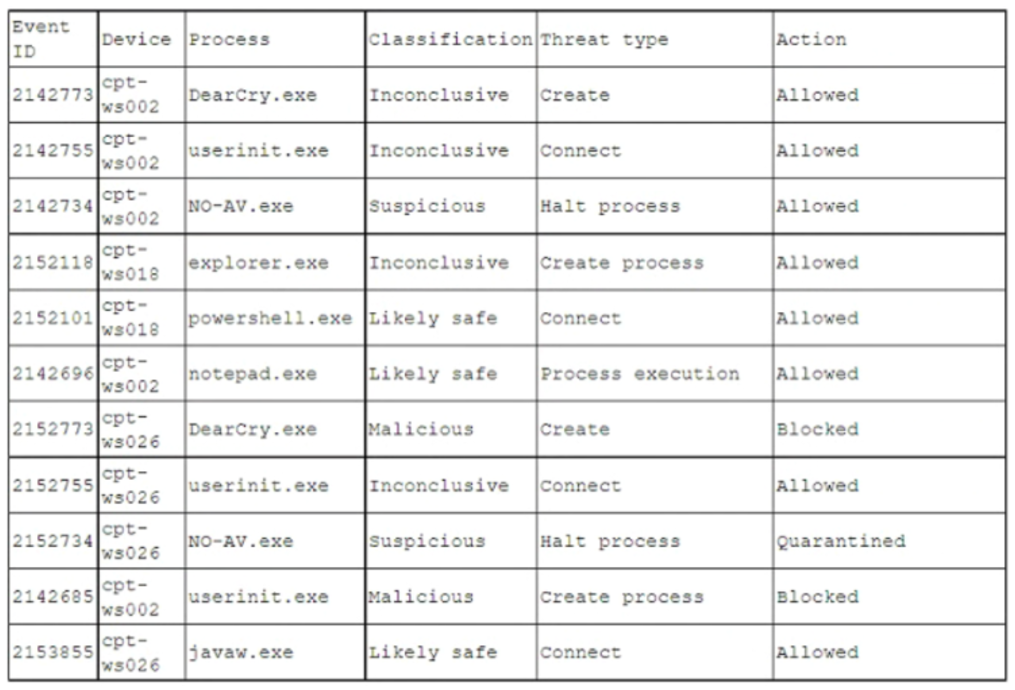
On which of the following devices and processes did the ransomware originate?
- A. cpt-ws018, powershell.exe
- B. cpt-ws026, DearCry.exe
- C. cpt-ws002, NO-AV.exe
- D. cpt-ws026, NO-AV.exe
- E. cpt-ws002, DearCry.exe
