Signed applications reduce risks by:
- A. encrypting the application’s data on the device
- B. requiring the developer to use code-level hardening techniques.
- C. providing assurance that the application is using unmodified source code.
- D. costing the developer money to publish, which reduces the likelihood of malicious intent.
A security engineer is assessing a legacy server and needs to determine if FTP is running and on which port. The service cannot be turned off, as it would impact a critical application’s ability to function. Which of the following commands would provide the information necessary to create a firewall rule to prevent that service from being exploited?
- A. service –-status-all | grep ftpd
- B. chkconfig –-list
- C. netstat –tulpn
- D. systemctl list-unit-file –-type service ftpd
- E. service ftpd status
A security assessor identified an internet-facing web service API provider that was deemed vulnerable. Execution of testssl provided the following insight:
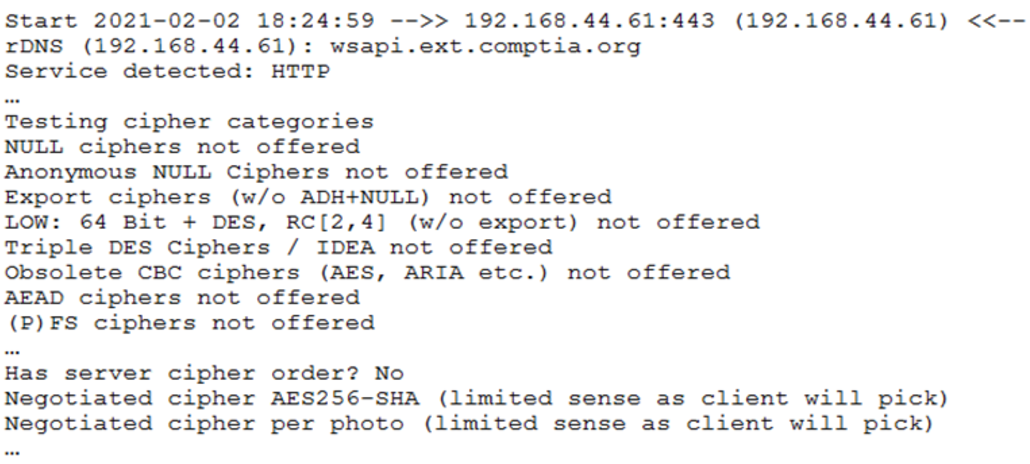
Which of the following configuration changes would BEST mitigate chosen ciphertext attacks?
- A. Enable 3DES ciphers IDEA.
- B. Enable export ciphers.
- C. Enable PFS ciphers.
- D. Enable AEAD.
A company underwent an audit in which the following issues were enumerated:
• Insufficient security controls for internet-facing services, such as VPN and extranet
• Weak password policies governing external access for third-party vendors
Which of the following strategies would help mitigate the risks of unauthorized access?
- A. 2FA
- B. RADIUS
- C. Federation
- D. OTP
A company recently implemented a CI/CD pipeline and is now concerned with the current state of its software development processes. The company wants to augment its CI/CD pipeline with a solution to:
• Prevent code configuration drifts.
• Ensure coding standards are followed.
Which of the following should the company implement to address these concerns? (Choose two.)
- A. Code signing
- B. Fuzzers
- C. Dynamic code analysis
- D. Manual approval processes
- E. Linters
- F. Regression testing
A SaaS startup is maturing its DevSecOps program and wants to identify weaknesses earlier in the development process in order to reduce the average time to identify serverless application vulnerabilities and the costs associated with remediation. The startup began its early security testing efforts with DAST to cover public-facing application components and recently implemented a bug bounty program. Which of the following will BEST accomplish the company’s objectives?
- A. RASP
- B. SAST
- C. WAF
- D. CMS
A security manager has written an incident response play book for insider attacks and is ready to begin testing it. Which of the following should the manager conduct to test the playbook?
- A. Automated vulnerability scanning
- B. Centralized logging, data analytics, and visualization
- C. Threat hunting
- D. Threat emulation
A company wants to improve the security of its web applications that are running on in-house servers. A risk assessment has been performed, and the following capabilities are desired:
• Terminate SSL connections at a central location
• Manage both authentication and authorization for incoming and outgoing web service calls
• Advertise the web service API
• Implement DLP and anti-malware features
Which of the following technologies will be the BEST option?
- A. WAF
- B. XML gateway
- C. ESB gateway
- D. API gateway
A bank hired a security architect to improve its security measures against the latest threats. The solution must meet the following requirements:
– Recognize and block fake websites.
– Decrypt and scan encrypted traffic on standard and non-standard
ports.
– Use multiple engines for detection and prevention.
– Have central reporting.
Which of the following is the BEST solution the security architect can propose?
A. CASB
B. Web filtering
C. NGFW
D. EDR
A mobile administrator is reviewing the following mobile device DHCP logs to ensure the proper mobile settings are applied to managed devices:
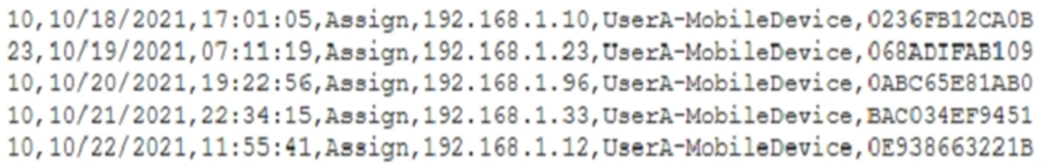
Which of the following mobile configuration settings is the mobile administrator verifying?
- A. Service set identifier authentication
- B. Wireless network auto joining
- C. 802.1X with mutual authentication
- D. Association MAC address randomization
