A company recently deployed a SIEM and began importing logs from a firewall, a file server, a domain controller, a web server, and a laptop. A security analyst receives a series of SIEM alerts and prepares to respond. The following is the alert information:
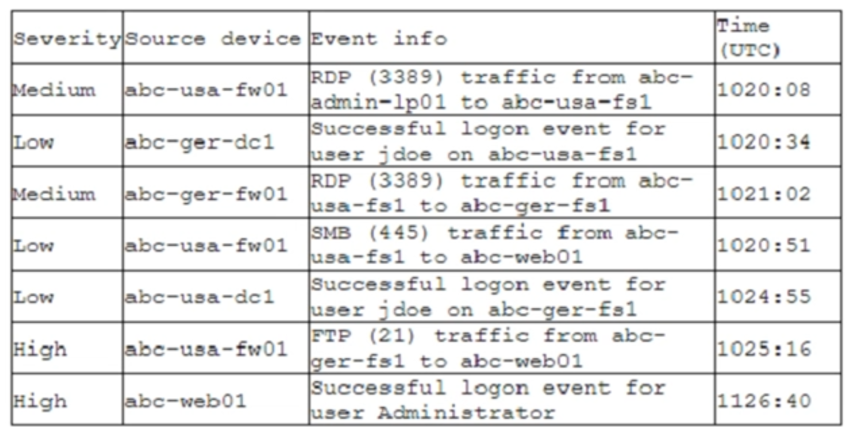
Which of the following should the security analyst do FIRST?
- A. Disable Administrator on abc-usa-fs1; the local account is compromised.
- B. Shut down the abc-usa-fs1 server; a plaintext credential is being used.
- C. Disable the jdoe account; it is likely compromised.
- D. Shut down abc-usa-fw01; the remote access VPN vulnerability is exploited.
A web service provider has just taken on a very large contract that comes with requirements that are currently not being implemented. In order to meet contractual requirements, the company must achieve the following thresholds:
• 99.99% uptime
• Load time in 3 seconds
• Response time = <1.0 seconds
Starting with the computing environment, which of the following should a security engineer recommend to BEST meet the requirements? (Choose three.)
- A. Installing a firewall at corporate headquarters
- B. Deploying a content delivery network
- C. Implementing server clusters
- D. Employing bare-metal loading of applications
- E. Lowering storage input/output
- F. Implementing RAID on the backup servers
- G. Utilizing redundant power for all developer workstations
- H. Ensuring technological diversity on critical servers
A security architect is designing a solution for a new customer who requires significant security capabilities in its environment. The customer has provided the architect with the following set of requirements:
• Capable of early detection of advanced persistent threats.
• Must be transparent to users and cause no performance degradation.
• Allow integration with production and development networks seamlessly.
• Enable the security team to hunt and investigate live exploitation techniques.
Which of the following technologies BEST meets the customer’s requirements for security capabilities?
- A. Threat Intelligence
- B. Deception software
- C. Centralized logging
- D. Sandbox detonation
A global financial firm wants to onboard a new vendor that sells a very specific SaaS application. The application is only hosted in the vendor’s home country, and the firm cannot afford any significant downtime. Which of the following is the GREATEST risk to the firm, assuming the decision is made to work with the new vendor?
- A. The application’s performance will be different in regional offices.
- B. There are regulatory concerns with using SaaS applications.
- C. The SaaS application will only be available to users in one country.
- D. There is no geographical redundancy in case of network outages.
A company is experiencing a large number of attempted network-based attacks against its online store. To determine the best course of action, a security analyst reviews the following logs.

Which of the following should the company do NEXT to mitigate the risk of a compromise from these attacks?
- A. Restrict HTTP methods.
- B. Perform parameterized queries.
- C. Implement input sanitization.
- D. Validate content types.
An organization must implement controls that are aligned with its financial requirements; specifically, the organization is looking to implement the following:
• Financial transactions that require one reviewer
• Audits of funds disbursements
• Cross-training of employees
Which of the following controls will address the organization’s requirements?
- A. Change management
- B. Job rotation
- C. Least privilege
- D. Separation of duties
A company recently migrated all its workloads to the cloud and implemented a transit VPC with a managed firewall. The cloud infrastructure implements a 10.0.0.0/16 network, and the firewall implements the following ACLs:
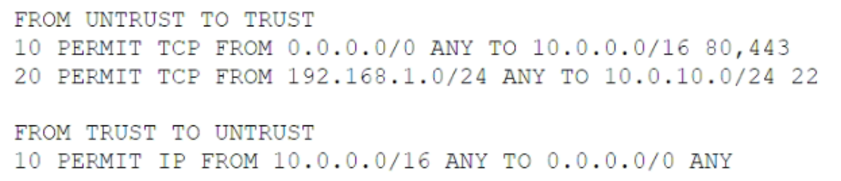
The Chief Information Security Officer wants to monitor relevant traffic for signs of data exfiltration. Which of the following should the organization place in its monitoring tool to BEST detect data exfiltration while reducing log size and the time to search logs?
- A. FROM UDP 10.0.0.0/16 ANY TO 0.0.0.0/0 ANY
- B. FROM TCP 10.0.0.0/16 80,443 TO 0.0.0.0/0 ANY
- C. FROM TCP 0.0.0.0/0 ANY TO 10.0.0.0/16 80,443,22
- D. FROM IP 10.0.0.0/16 ANY TO 0.0.0.0/0 ANY
- E. FROM IP 0.0.0.0/0 ANY TO TCP 0.0.0.0/0 ANY
- F. FROM UDP 0.0.0.0/0 ANY TO 0.0.0.0/0 ANY
A security analyst is reviewing the data portion acquired from the following command:
tcpdump -lnvi icmp and src net 192.168.1.0/24 and dst net 0.0.0.0/0 -w output.pcap
The data portion of the packet capture shows the following:
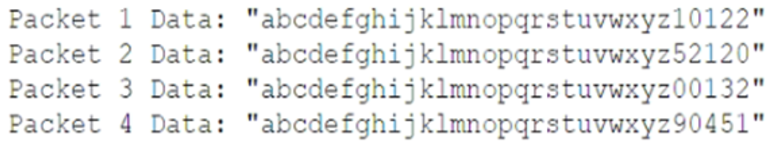
The analyst suspects that a data exfiltration attack is occurring using a pattern in which the last five digits are encoding sensitive information. Which of the following technologies and associated rules should the analyst implement to stop this specific attack? (Choose two.)
- A. Intrusion prevention system
- B. Data loss prevention
- C. sed -e ‘s/a-z.*0-9.*//g’
- D. reject icmp any any <> any any (msg:”alert”; regex [a-z]{26}[0-9]{5})
- E. Second-generation firewall
- F. drop icmp from 192.168.1.0/24 to 0.0.0.0/0
The Chief Information Security Officer (CISO) has outlined a five-year plan for the company that includes the following:
• Implement an application security program.
• Reduce the click rate on phishing simulations from 73% to 8%.
• Deploy EDR to all workstations and servers.
• Ensure all systems are sending logs to the SIEM.
• Reduce the percentage of systems with vulnerabilities from 89% to 5%.
Which of the following would BEST aid the CISO in determining whether these goals are obtainable?
- A. An asset inventory
- B. A third-party audit
- C. A risk assessment
- D. An organizational CMMI
The Chief Security Officer (CSO) requested the security team implement technical controls that meet the following requirements:
• Monitors traffic to and from both local NAS and cloud-based file repositories
• Prevents on-site staff who are accessing sensitive customer PII documents on file repositories from accidentally or deliberately sharing sensitive documents on personal SaaS solutions
• Uses document attributes to reduce false positives
• Is agentless and not installed on staff desktops or laptops
Which of the following when installed and configured would BEST meet the CSO’s requirements? (Choose two.)
- A. DLP
- B. NGFW
- C. UTM
- D. UEBA
- E. CASB
- F. HIPS
