A security engineer at a manufacturing facility is trying to determine whether any of the OT devices are susceptible to a recently announced vulnerability. Which of the following is the best way for the engineer to detect exploitable vulnerabilities?
- A. Utilize a passive vulnerability scanner on the network.
- B. Compare deployed equipment to the CVE disclosure.
- C. Perform threat hunting on the OT segment.
- D. Review software inventory for vulnerable versions.
A security team performed an external attack surface analysis and discovered the following issues on a group of application servers:
• The majority of the systems have end-of-life operating systems.
• The latest patches that are available are over two years old.
• The systems are considered mission critical for client support.
• The proprietary software running on the systems is not compatible with newer versions of the operating system.
• Server outages would negatively affect quarterly revenue projections.
Which of the following would allow the security team to immediately mitigate the risks inherent to this situation?
- A. Implement a WAF between the application servers and the external perimeter.
- B. Contact the vendor for the proprietary software and negotiate a new maintenance contract.
- C. Document the application servers as being end of life and define a target date for decommission.
- D. Isolate the servers from the internet and configure an internal ACL, only allowing to authorized employees.
In a situation where the cost of anti-malware exceeds the potential loss from a malware threat, which of the following is the most cost-effective risk response?
A. Risk transfer
B. Risk mitigation
C. Risk acceptance
D. Risk avoidance
A security architect is tasked with securing a new cloud-based videoconferencing and collaboration platform to support a new distributed workforce. The security architect’s key objectives are to:
• Maintain customer trust
• Minimize data leakage
• Ensure non-repudiation
Which of the following would be the best set of recommendations from the security architect?
- A. Enable the user authentication requirement, enable end-to-end encryption, and enable waiting rooms.
- B. Disable file exchange, enable watermarking, and enable the user authentication requirement.
- C. Enable end-to-end encryption, disable video recording, and disable file exchange.
- D. Enable watermarking, enable the user authentication requirement, and disable video recording.
Based on a recent security audit, a company discovered the perimeter strategy is inadequate for its recent growth. To address this issue, the company is looking for a solution that includes the following requirements:
• Collapse of multiple network security technologies into a single footprint
• Support for multiple VPNs with different security contexts
• Support for application layer security (Layer 7 of the OSI Model)
Which of the following technologies would be the most appropriate solution given these requirements?
- A. NAT gateway
- B. Reverse proxy
- C. NGFW
- D. NIDS
Due to budget constraints, an organization created a policy that only permits vulnerabilities rated high and critical according to CVSS to be fixed or mitigated. A security analyst notices that many vulnerabilities that were previously scored as medium are now breaching higher thresholds. Upon further investigation, the analyst notices certain ratings are not aligned with the approved system categorization.
Which of the following can the analyst do to get a better picture of the risk while adhering to the organization’s policy?
- A. Align the exploitability metrics to the predetermined system categorization.
- B. Align the remediation levels to the predetermined system categorization.
- C. Align the impact subscore requirements to the predetermined system categorization.
- D. Align the attack vectors to the predetermined system categorization.
SIMULATION
–
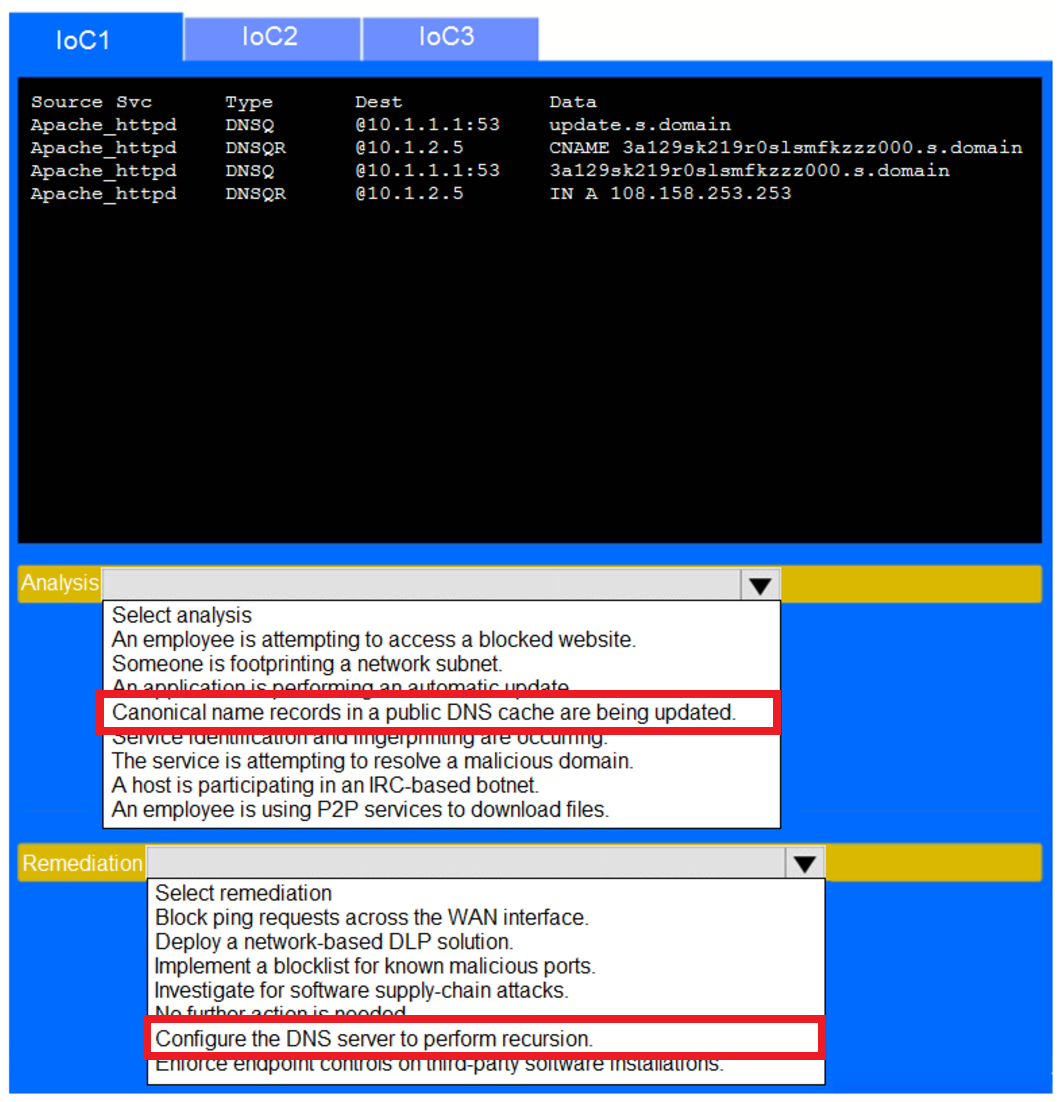
During the course of normal SOC operations, three anomalous events occurred and were flagged as potential IoCs. Evidence for each of these potential IoCs is provided.
INSTRUCTIONS
–
Review each of the events and select the appropriate analysis and remediation options for each IoC.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
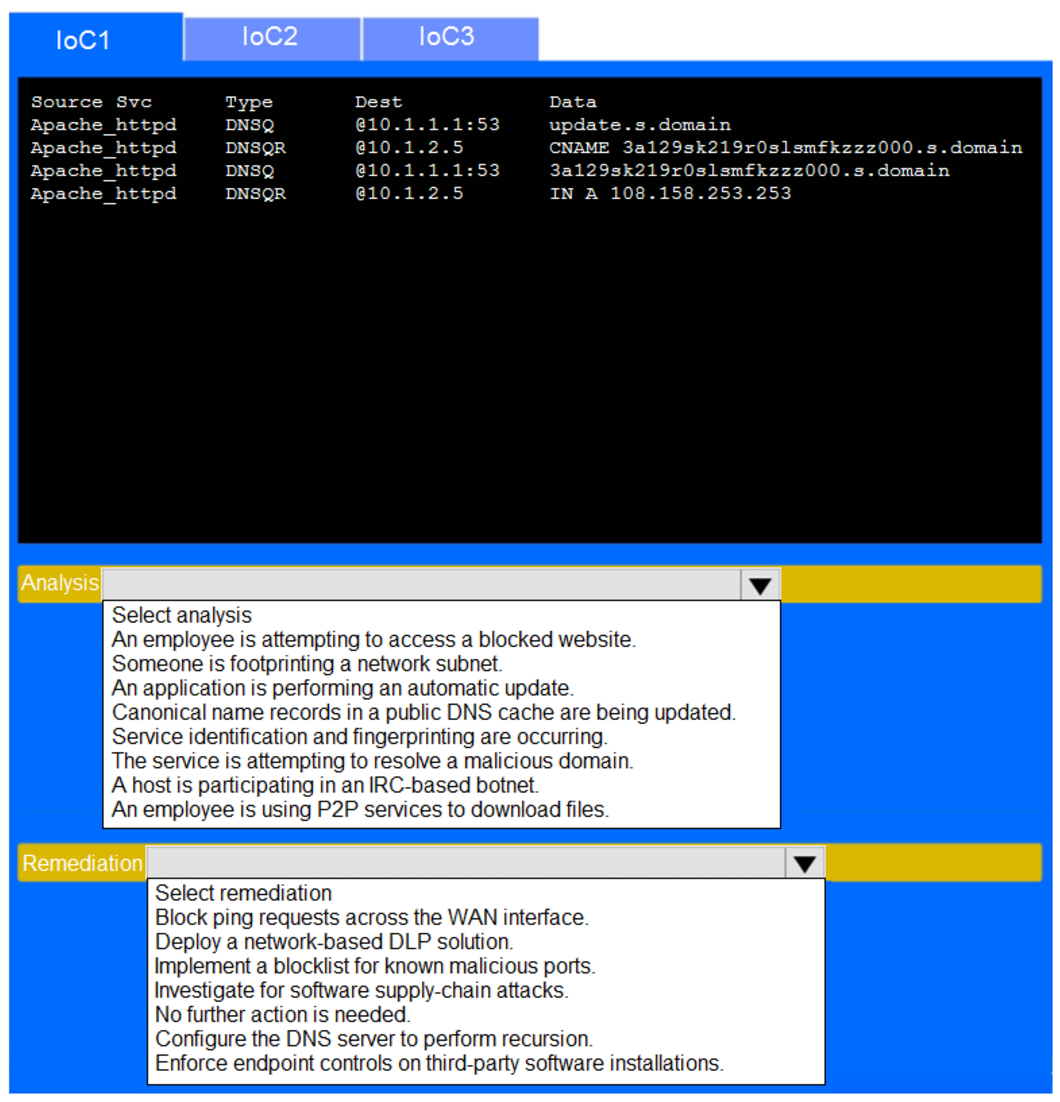
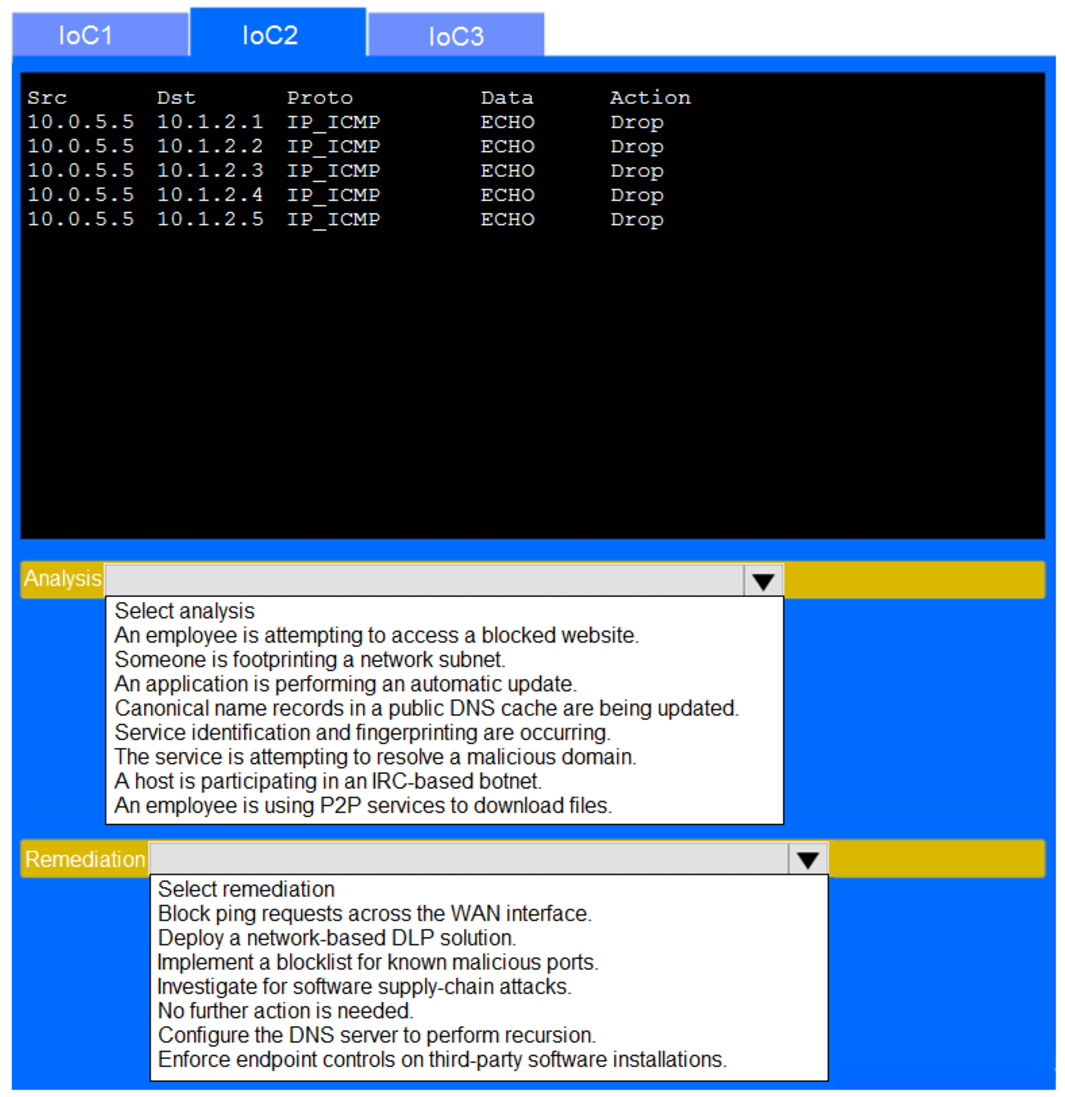
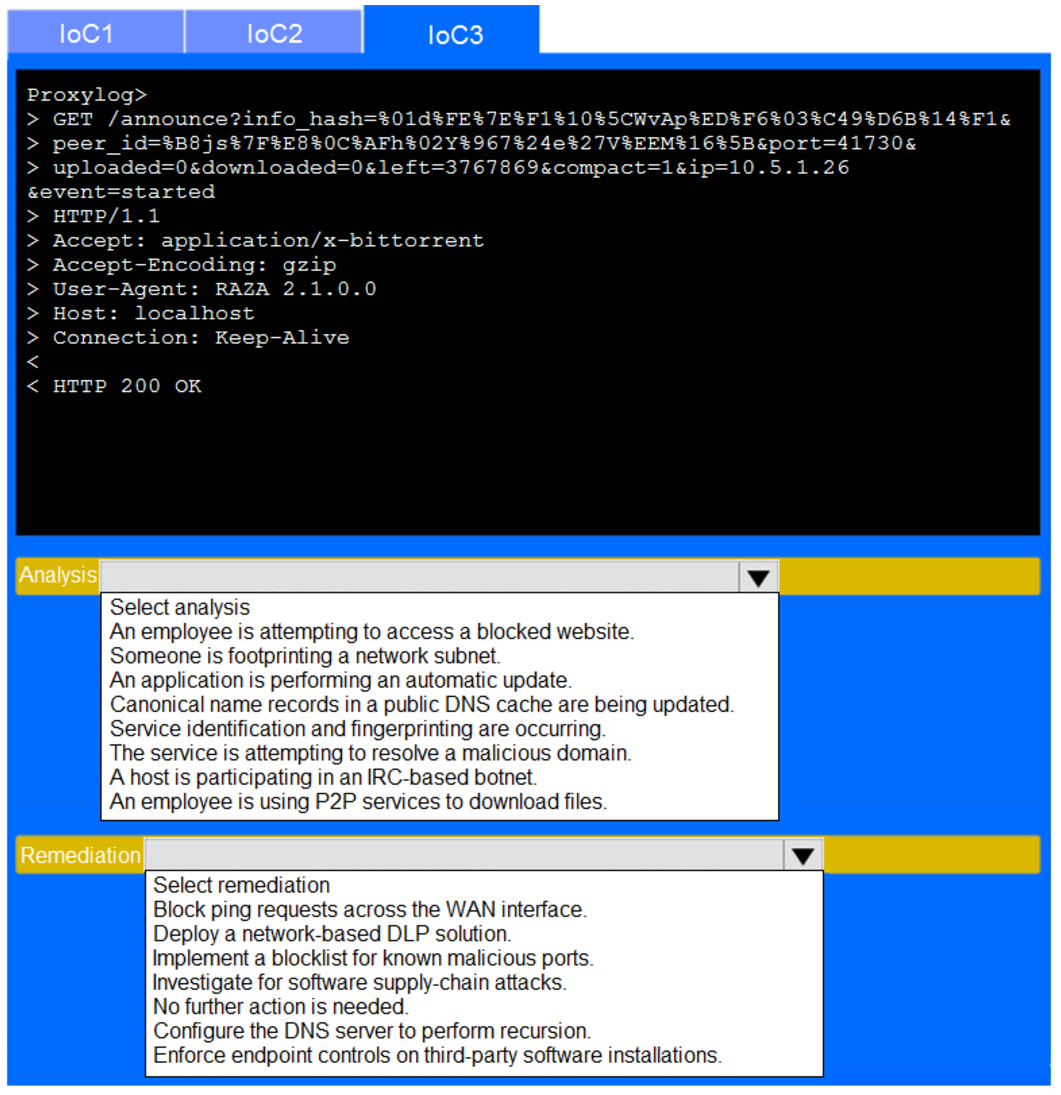
Answer Area :
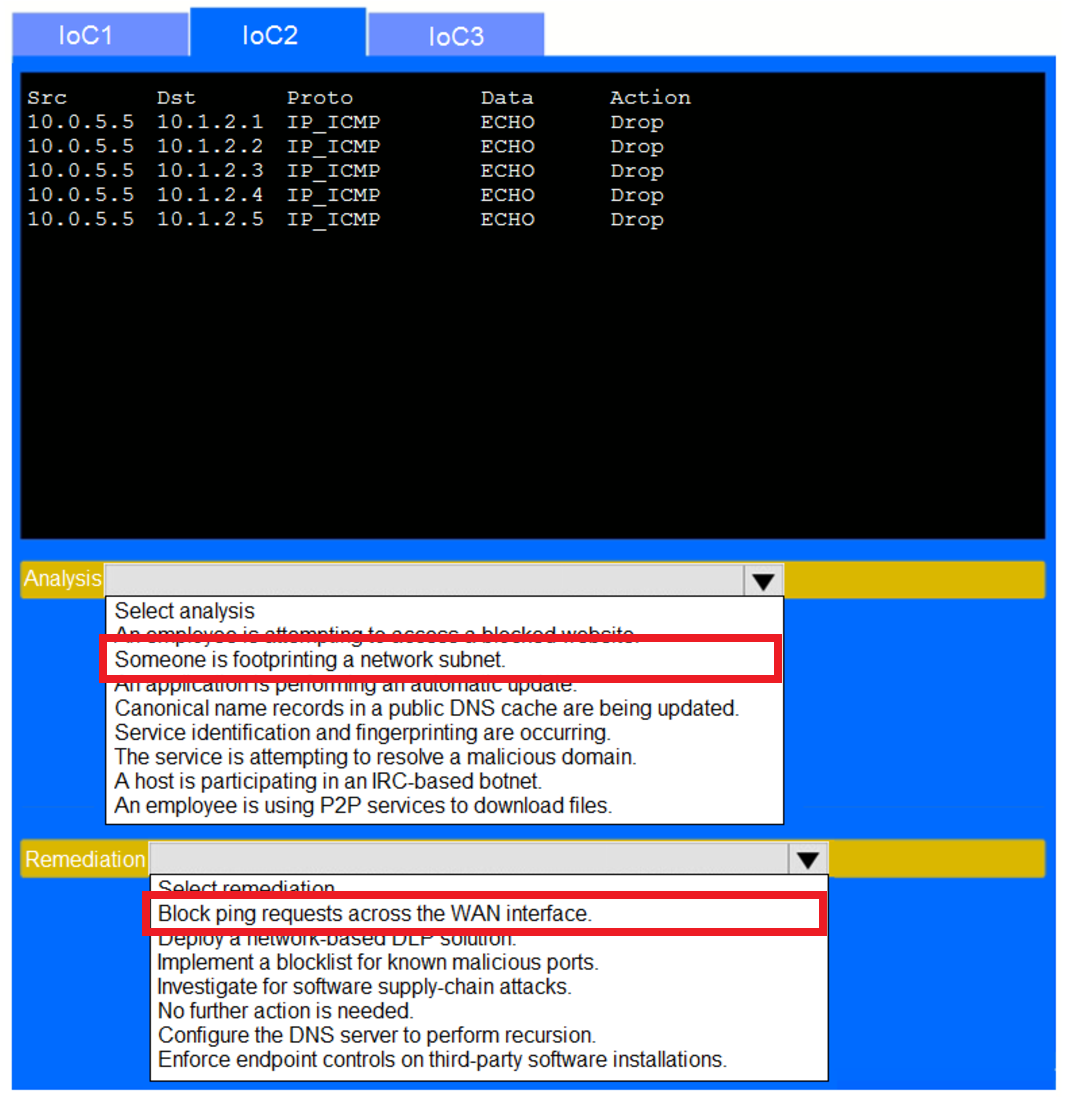
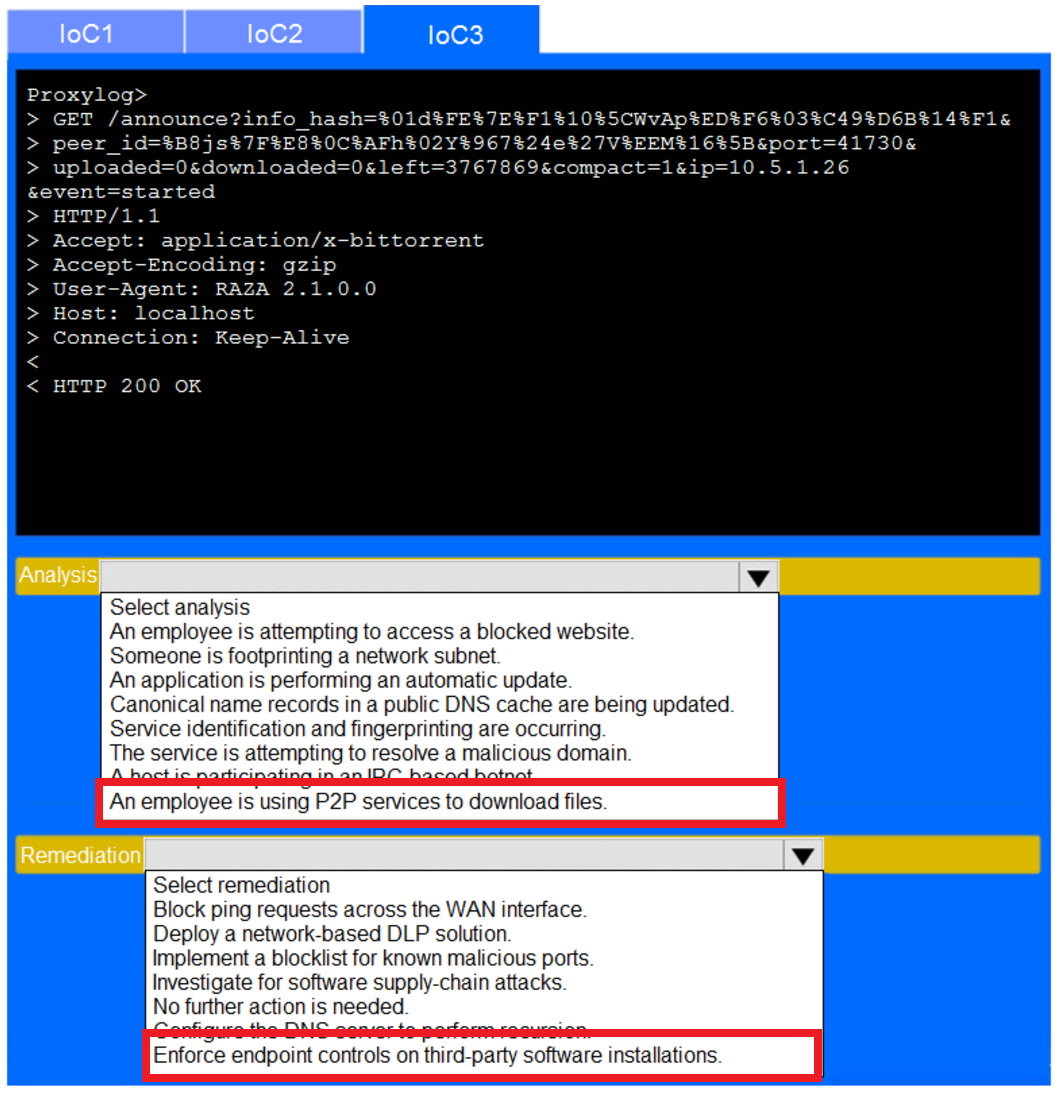
A security analyst received a report that a suspicious flash drive was picked up in the office’s waiting area, located beyond the secured door. The analyst investigated the drive and found malware designed to harvest and transmit credentials. Security cameras in the area where the flash drive was discovered showed a vendor representative dropping the drive. Which of the following should the analyst recommend as an additional way to identify anyone who enters the building, in the event the camera system fails?
- A. Employee badge logs
- B. Phone call logs
- C. Vehicle registration logs
- D. Visitor logs
An IT director is working on a solution to meet the challenge of remotely managing laptop devices and securely locking them down. The solution must meet the following requirements:
• Cut down on patch management.
• Make use of standard configurations.
• Allow for custom resource configurations.
• Provide access to the enterprise system from multiple types of devices.
Which of the following would meet these requirements?
- A. MDM
- B. Emulator
- C. Hosted hypervisor
- D. VDI
A software developer has been tasked with creating a unique threat detection mechanism that is based on machine learning. The information system for which the tool is being developed is on a rapid CI/CD pipeline, and the tool developer is considered a supplier to the process. Which of the following presents the most risk to the development life cycle and to the ability to deliver the security tool on time?
- A. Deep learning language barriers
- B. Big Data processing required for maturity
- C. Secure, multiparty computation requirements
- D. Computing capabilities available to the developer
