Which of the following provides the best solution for organizations that want to securely back up the MFA seeds for its employees in a central, offline location with minimal management overhead?
- A. Key escrow service
- B. Secrets management
- C. Encrypted database
- D. Hardware security module
A senior security analyst is helping the development team improve the security of an application that is being developed. The developers use third-party libraries and applications. The software in development used old, third-party packages that were not replaced before market distribution. Which of the following should be implemented into the SDLC to resolve the issue?
- A. Software composition analysis
- B. A SCAP scanner
- C. A SAST
- D. A DAST
A security researcher identified the following messages while testing a web application:
/file/admin/myprofile.php ERROR file does not exist.
/file/admin/userinfo.php ERROR file does not exist.
/file/admin/adminprofile.php ERROR file does not exist.
/file/admin/admininfo.php ERROR file does not exist.
/file/admin/universalprofile.php ERROR file does not exist.
/file/admin/universalinfo.php ERROR file does not exist.
/file/admin/restrictedprofile.php ACCESS is denied.
/file/admin/restrictedinfo.php ERROR file does not exist.
Which of the following should the researcher recommend to remediate the issue?
- A. Software composition analysis
- B. Packet inspection
- C. Proper error handling
- D. Elimination of the use of unsafe functions
A company with only U.S.-based customers wants to allow developers from another country to work on the company’s website. However, the company plans to block normal internet traffic from the other country. Which of the following strategies should the company use to accomplish this objective? (Choose two.)
- A. Block foreign IP addresses from accessing the website.
- B. Have the developers use the company’s VPN.
- C. Implement a WAF for the website.
- D. Give the developers access to a jump box on the network.
- E. Employ a reverse proxy for the developers.
- F. Use NAT to enable access for the developers.
A security engineer is re-architecting a network environment that provides regional electric distribution services. During a pretransition baseline assessment, the engineer identified the following security-relevant characteristics of the environment:
• Enterprise IT servers and supervisory industrial systems share the same subnet.
• Supervisory controllers use the 750MHz band to direct a portion of fielded PLCs.
• Command and telemetry messages from industrial control systems are unencrypted and unauthenticated.
Which of the following re-architecture approaches would be best to reduce the company’s risk?
- A. Implement a one-way guard between enterprise IT services and mission-critical systems, obfuscate legitimate RF signals by broadcasting noise, and implement modern protocols to authenticate ICS messages.
- B. Characterize safety-critical versus non-safety-critical systems, isolate safety-critical systems from other systems, and increase the directionality of RF links in the field.
- C. Create a new network segment for enterprise IT servers, configure NGFW to enforce a well-defined segmentation policy, and implement a WIDS to monitor the spectrum.
- D. Segment supervisory controllers from field PLCs, disconnect the entire network from the internet, and use only the 750MHz link for controlling energy distribution services.
A security architect is reviewing the following organizational specifications for a new application:
• Be sessionless and API-based
• Accept uploaded documents with PII, so all storage must be ephemeral
• Be able to scale on-demand across multiple nodes
• Restrict all network access except for the TLS port
Which of the following ways should the architect recommend the application be deployed in order to meet security and organizational infrastructure requirements?
- A. Utilizing the cloud container service
- B. On server instances with auto scaling groups
- C. Using scripted delivery
- D. With a content delivery network
The results of an internal audit indicate several employees reused passwords that were previously included in a published list of compromised passwords.
The company has the following employee password policy:
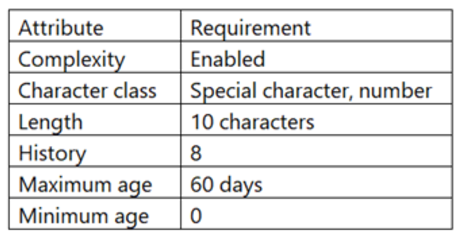
Which of the following should be implemented to best address the password reuse issue? (Choose two.)
- A. Increase the minimum age to two days.
- B. Increase the history to 20.
- C. Increase the character length to 12.
- D. Add case-sensitive requirements to character class.
- E. Decrease the maximum age to 30 days.
- F. Remove the complexity requirements.
- G. Increase the maximum age to 120 days.
A company recently deployed new servers to create an additional cluster to support a new application. The corporate security policy states that all new servers must be resilient. The new cluster has a high-availability configuration for a smooth failover. The failover was successful following a recent power outage, but both clusters lost critical data, which impacted recovery time. Which of the following needs to be configured to help ensure minimal delays when power outages occur in the future?
- A. Replication
- B. Caching
- C. Containerization
- D. Redundancy
- E. High availability
Ann, a user, brings her laptop to an analyst after noticing it has been operating very slowly. The security analyst examines the laptop and obtains the following output:
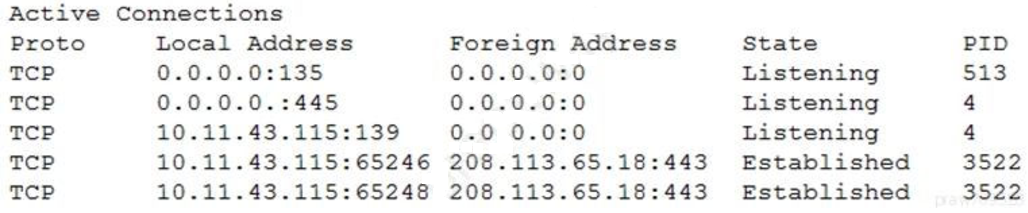
Which of the following will the analyst most likely use NEXT?
- A. Process explorer
- B. Vulnerability scanner
- C. Antivirus
- D. Network enumerator
A company has identified a number of vulnerable, end-of-support systems with limited defensive capabilities. Which of the following would be the first step in reducing the attack surface in this environment?
- A. Utilizing hardening recommendations
- B. Deploying IPS/IDS throughout the environment
- C. Installing and updating antivirus
- D. Installing all available patches
