A security architect is implementing a SOAR solution in an organization’s cloud production environment to support detection capabilities. Which of the following will be the most likely benefit?
- A. Improved security operations center performance
- B. Automated firewall log collection tasks
- C. Optimized cloud resource utilization
- D. Increased risk visibility
A security administrator wants to enable a feature that would prevent a compromised encryption key from being used to decrypt all the VPN traffic. Which of the following should the security administrator use?
- A. Salsa20 cipher
- B. TLS-based VPN
- C. PKI-based IKE IPSec negotiation
- D. Perfect forward secrecy
A help desk analyst suddenly begins receiving numerous calls from remote employees who state they are unable to connect to the VPN. The employees indicate the VPN client software is warning about an expired certificate. The help desk analyst determines the VPN certificate is valid. Which of the following is the most likely cause of the issue?
- A. The certificate has been compromised and needs to be replaced.
- B. The VPN concentrator is running an old version of code and needs to be upgraded.
- C. The NTP settings on the VPN concentrator are incorrectly configured.
- D. The end users are using outdated VPN client software.
A security analyst has been provided the following partial Snort IDS rule to review and add into the company’s Snort IDS to identify a CVE:
alert tcp any any -> SHOME_NET 3389 (flow:to_server,established; content:”MS_T120|00|”; fasc_pattern:only)
Which of the following should the analyst recommend to mitigate this type of vulnerability?
- A. IPSec rules
- B. OS patching
- C. Two-factor authentication
- D. TCP wrappers
A security assessor identified an internet-facing web service API provider that was deemed vulnerable. Execution of testssl provided the following insight:
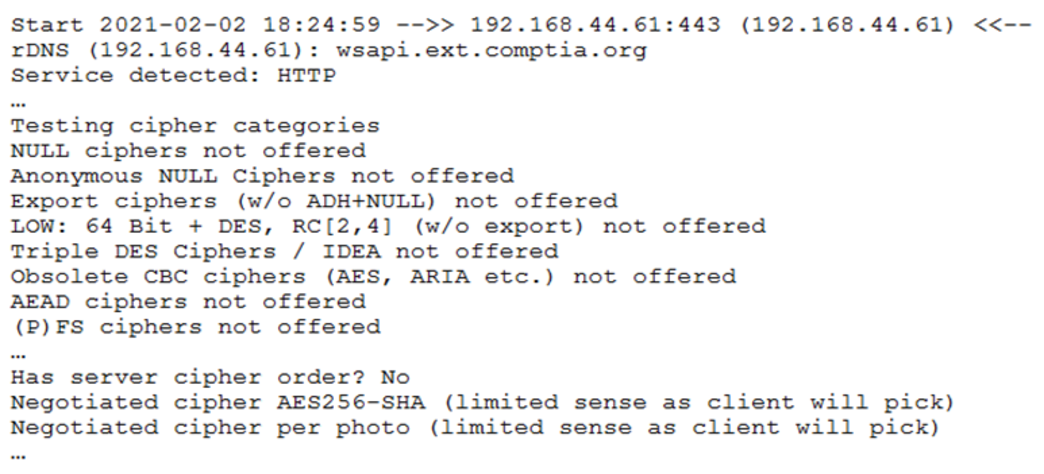
Which of the following configuration changes would BEST mitigate chosen ciphertext attacks?
- A. Enable 3DES ciphers IDEA.
- B. Enable export ciphers.
- C. Enable PFS ciphers.
- D. Enable AEAD.
An organization’s load balancers have reached end of life and have a vulnerability that will require them to be replaced. The load balancers are scheduled to be decommissioned within the next month. The management team has decided not to resolve this risk and instead allow the load balancers to remain in place until their decommission date. Which of the following risk handling techniques is the management team using?
- A. Avoid
- B. Mitigate
- C. Accept
- D. Transfer
A security analyst is reviewing a new IOC in which data is injected into an online process. The IOC shows the data injection could happen in the following ways:
• Five numerical digits followed by a dash, followed by four numerical digits; or
• Five numerical digits
When one of these IOCs is identified. the online process stops working. Which of the following regular expressions should be implemented in the NIPS?
- A. ^\d{4}(-\d{5})?$
- B. ^\d{5}(-\d{4})?$
- C. ^\d{5-4}$
- D. ^\d{9}$
Which of the following testing plans is used to discuss disaster recovery scenarios with representatives from multiple departments within an incident response team but without taking any invasive actions?
- A. Disaster recovery checklist
- B. Tabletop exercise
- C. Full interruption test
- D. Parallel test
Recently, two large engineering companies in the same line of business decided to approach cyberthreats in a united way. Which of the following best describes this unified approach?
- A. NDA
- B. ISA
- C. SLA
- D. MOU
Application owners are reporting performance issues with traffic using port 1433 from the cloud environment. A security administrator has various pcap files to analyze the data between the related source and destination servers. Which of the following tools should be used to help troubleshoot the issue?
- A. Fuzz testing
- B. Wireless vulnerability scan
- C. Exploit framework
- D. Password cracker
- E. Protocol analyzer
