An employee in the accounting department created a potential security incident by emailing an internal spreadsheet to an external email address. The spreadsheet contained thousands of payment card numbers. A security administrator queried the following filter log and filter policy settings:
Outbound filter log information for the email:
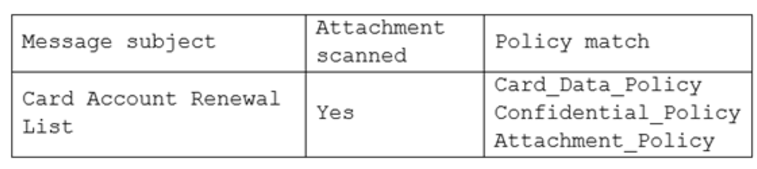
Outbound filter policy settings:
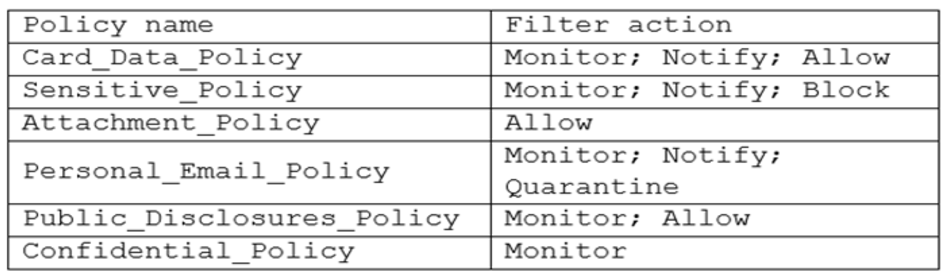
Which of the following would best prevent this scenario from reoccurring without causing disruptions to normal business operations?
- A. Add “Sensitive” data classification tags to all files that include matches to the payment card number format.
- B. Change the Filter action for Card_Data_Policy from Allow to Quarantine.
- C. Add the Filter actions Block and Notify to the Confidential_Policy.
- D. Change the Filter action for all Attachment_Policy from Allow to Block.
- E. Change the Filter action for Personal_Email_Policy from Quarantine to Block.
- F. Configure the Monitor action to send automated alerts to the sender’s immediate supervisor.
Which of the following industrial protocols is most likely to be found in public utility applications, such as water or electric?
- A. CIP
- B. Zigbee
- C. Modbus
- D. DNP3
Following a Log4j outbreak, several network appliances were not managed and remained undetected despite an application inventory system being in place. Which of the following solutions should the security director recommend to best understand the composition of applications on unmanaged devices?
- A. Protocol analyzer
- B. Package monitoring
- C. Software bill of materials
- D. Fuzz testing
A commercial OSINT provider utilizes and reviews data from various sources of publicly available information. The provider is transitioning the subscription service to a model that limit’s the scope of available data based on subscription tier. Which of the following approaches would best ensure subscribers are only granted access to data associated with their tier? (Choose two.)
- A. Storing collected data on separate physical media per tier
- B. Controlling access to data based on the role of users
- C. Employing attribute-based access control
- D. Implementing a behavior-based IDS positioned at the storage network gateway
- E. Establishing a classification and labeling scheme
- F. Implementing a mandatory access control scheme
A security engineer evaluates the overall security of a custom mobile gaming application and notices that developers are bringing in a large number of open-source packages without appropriate patch management. Which of the following would the engineer most likely recommend for uncovering known vulnerabilities in the packages?
- A. Leverage an exploitation framework to uncover vulnerabilities.
- B. Use fuzz testing to uncover potential vulnerabilities in the application.
- C. Utilize a software composition analysis tool to report known vulnerabilities.
- D. Reverse engineer the application to look for vulnerable code paths.
- E. Analyze the use of an HTTP intercepting proxy to dynamically uncover issues.
A company is rewriting a vulnerable application and adding the mprotect() system call in multiple parts of the application’s code that was being leveraged by a recent exploitation tool. Which of the following should be enabled to ensure the application can leverage the new system call against similar attacks in the future?
- A. TPM
- B. Secure boot
- C. NX bit
- D. HSM
An incident response team completed recovery from offline backup for several workstations. The workstations were subjected to a ransomware attack after users fell victim to a spear-phishing campaign, despite a robust training program. Which of the following questions should be considered during the lessons-learned phase to most likely reduce the risk of reoccurrence? (Choose two.)
- A. Are there opportunities for legal recourse against the originators of the spear-phishing campaign?
- B. What internal and external stakeholders need to be notified of the breach?
- C. Which methods can be implemented to increase speed of offline backup recovery?
- D. What measurable user behaviors were exhibited that contributed to the compromise?
- E. Which technical controls, if implemented, would provide defense when user training fails?
- F. Which user roles are most often targeted by spear phishing attacks?
An analyst determined that the current process for manually handling phishing attacks within the company is ineffective. The analyst is developing a new process to ensure phishing attempts are handled internally in an appropriate and timely manner. One of the analyst’s requirements is that a blocklist be updated automatically when phishing attempts are identified. Which of the following would help satisfy this requirement?
- A. SOAR
- B. MSSP
- C. Containerization
- D. Virtualization
- E. MDR deployment
A security analyst is conducting an investigation regarding a potential insider threat. An unauthorized USB device might have been used to exfiltrate proprietary data from a Linux system.
Which of the following options would identify the IoCs and provide the appropriate response?
- A. Review the network logs and update the firewall rules.
- B. Review the operating system logs and update the DLP rules.
- C. Review the vulnerability logs and update the IDS rules.
- D. Obtain the device ID using dmesg and update the portable storage inventory.
A security engineer is implementing DLP. Which of the following should the security engineer include in the overall DLP strategy?
- A. Tokenization
- B. Network traffic analysis
- C. Data classification
- D. Multifactor authentication
