A DNS forward lookup zone named comptia.org must:
• Ensure the DNS is protected from on-path attacks.
• Ensure zone transfers use mutual authentication and are authenticated and negotiated.
Which of the following should the security architect configure to meet these requirements? (Choose two.)
- A. Public keys
- B. Conditional forwarders
- C. Root hints
- D. DNSSEC
- E. CNAME records
- F. SRV records
An accounting team member received a voicemail message from someone who sounded like the Chief Financial Officer (CFO). In the voicemail message, the caller requested a wire transfer to a bank account the organization had not used before. Which of the following best describes this type of attack?
- A. The attacker used deep fake technology to simulate the CFO’s voice.
- B. The CFO tried to commit a form of embezzlement.
- C. The attacker used caller ID spoofing to imitate the CFO’s internal phone extension.
- D. The attacker successfully phished someone in the accounts payable department.
A social media company wants to change encryption ciphers after identifying weaknesses in the implementation of the existing ciphers. The company needs the new ciphers to meet the following requirements:
• Utilize less RAM than competing ciphers.
• Be more CPU-efficient than previous ciphers.
• Require customers to use TLS 1.3 while broadcasting video or audio.
Which of the following is the best choice for the social media company?
- A. IDEA-CBC
- B. AES-GCM
- C. ChaCha20-Poly1305
- D. Camellia-CBC
While performing mandatory monthly patch updates on a production application server, the security analyst reports an instance of buffer overflow for a new application that was migrated to the cloud and is also publicly exposed. Security policy requires that only internal users have access to the application. Which of the following should the analyst implement to mitigate the issues reported? (Choose two.)
- A. Configure firewall rules to block all external traffic.
- B. Enable input validation for all fields.
- C. Enable automatic updates to be installed on all servers.
- D. Configure the security group to enable external traffic.
- E. Set up a DLP policy to alert for exfiltration on all application servers.
- F. Enable nightly vulnerability scans.
A company implements the following access control methodology based on the following data classifications:
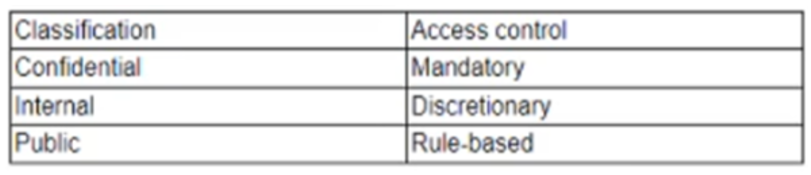
The Chief Information Security Officer (CISO) wants to implement an additional layer of access control based on the geographic location of the underlying system that processes and stores data. The additional layer will be added to the existing access control system. Which of the following components must be implemented to achieve these goals? (Choose two.)
- A. Tagging
- B. Attribute-based access control
- C. Role-based access control
- D. Groups
- E. Tokenization
- F. Digital rights management
A security engineer is assessing a new tool to segment data and communications between domains. The assessment must determine how data transmission controls can be bypassed without detection. Which of the following techniques should the security engineer use?
- A. Machine-learning statistical analysis
- B. Fuzz testing
- C. Covert channel analysis
- D. Protocol analysis
An engineer has had scaling issues with a web application hosted on premises and would like to move to a serverless architecture. Which of the following cloud benefits would be best to utilize for this project?
- A. Cost savings for hosting
- B. Automation of resource provisioning
- C. Providing geo-redundant hosting
- D. Eliminating need to patch
Multiple users have reported that an internal website’s status is listed as insecure because the TLS certificate has expired. Although a new certificate was generated, this issue has become a common occurrence throughout the year for multiple websites. Which of the following best prevents recurrence of this issue?
- A. OCSP responder
- B. Life-cycle management
- C. Wildcard certificates
- D. Certificate pinning
Following a successful exploitation of an RCE vulnerability during a penetration test, a systems administrator is performing remediation activities of the target system. Since the systems administrator was not involved in the planning process for the penetration test, a production server was inadvertently targeted and impacted by the actions of the penetration tester. Which of the following would be the most appropriate to reduce the impact of the penetration test in the future?
- A. Leverage a purple team approach to refine scope definition.
- B. Exclude non-production systems from the penetration test.
- C. Implement a black-box approach for the penetration test.
- D. Include an intercepting proxy in the production environment.
- E. Rely on web application vulnerability scans instead of penetration testing.
An organization is working to secure its development process to ensure developers cannot deploy artifacts directly into the production environment. Which of the following security practice recommendations would be the best to accomplish this objective?
- A. Implement least privilege access to all systems.
- B. Roll out security awareness training for all users.
- C. Set up policies and systems with separation of duties.
- D. Enforce job rotations for all developers and administrators.
- E. Utilize mandatory vacations for all developers.
- F. Review all access to production systems on a quarterly basis.
