An organization handles sensitive information that must be displayed on call center technicians’ screens to verify the identities of remote callers. The technicians use three randomly selected fields of information to complete the identity verification process. Some of the fields contain PII that are unique identifiers for the remote callers. Which of the following should be implemented to identify remote callers while also reducing the risk that technicians could improperly use the identification information?
- A. Data masking
- B. Encryption
- C. Tokenization
- D. Scrubbing
- E. Substitution
Which of the following is the best reason for obtaining file hashes from a confiscated laptop?
- A. To prevent metadata tampering on each file
- B. To later validate the integrity of each file
- C. To generate unique identifiers for each file
- D. To preserve the chain of custody of files
Which of the following is the best reason to maintain visibility into vendor supply chains?
- A. To circumvent interdiction of shipments by nation-state actors
- B. To prevent clandestine tampering with components in transit
- C. To comply with import/export legal regulations
- D. To ensure the lowest possible price is quoted
A security team is creating tickets to track the progress of remediation. Which of the following is used to specify the due dates for high- and critical-priority findings?
- A. MSA
- B. SLA
- C. ISA
- D. MOU
A company wants to reduce its backup storage requirement and is undertaking a data cleanup project. Which of the following should a security administrator consider first when determining which data should be deleted?
- A. Retention schedules
- B. Classification levels
- C. Sanitization requirements
- D. Data labels
- E. File size
An IDS was unable to detect malicious network traffic during a recent security incident, even though all traffic was being sent using HTTPS. As a result, a website used by employees was compromised. Which of the following detection mechanisms would allow the IDS to detect an attack like this one in the future?
- A. Deobfuscation
- B. Protocol decoding
- C. Inspection proxy
- D. Digital rights management
Which of the following is the reason why security engineers often cannot upgrade the security of embedded facility automation systems?
- A. They are constrained by available compute.
- B. They lack x86-64 processors.
- C. They lack EEPROM.
- D. They are not logic-bearing devices.
A company is migrating its data center to the cloud. Some hosts had been previously isolated, but a risk assessment convinced the engineering team to reintegrate the systems.
Because the systems were isolated, the risk associated with vulnerabilities was low. Which of the following should the security team recommend be performed before migrating these servers to the cloud?
- A. Performing patching and hardening
- B. Deploying host and network IDS
- C. Implementing least functionality and time-based access
- D. Creating a honeypot and adding decoy files
A mobile device hardware manufacturer receives the following requirements from a company that wants to produce and sell a new mobile platform:
• The platform should store biometric data.
• The platform should prevent unapproved firmware from being loaded.
• A tamper-resistant, hardware-based counter should track if unapproved firmware was loaded.
Which of the following should the hardware manufacturer implement? (Choose three.)
- A. ASLR
- B. NX
- C. eFuse
- D. SED
- E. SELinux
- F. Secure boot
- G. Shell restriction
- H. Secure enclave
An analyst reviews the following output collected during the execution of a web application security assessment:
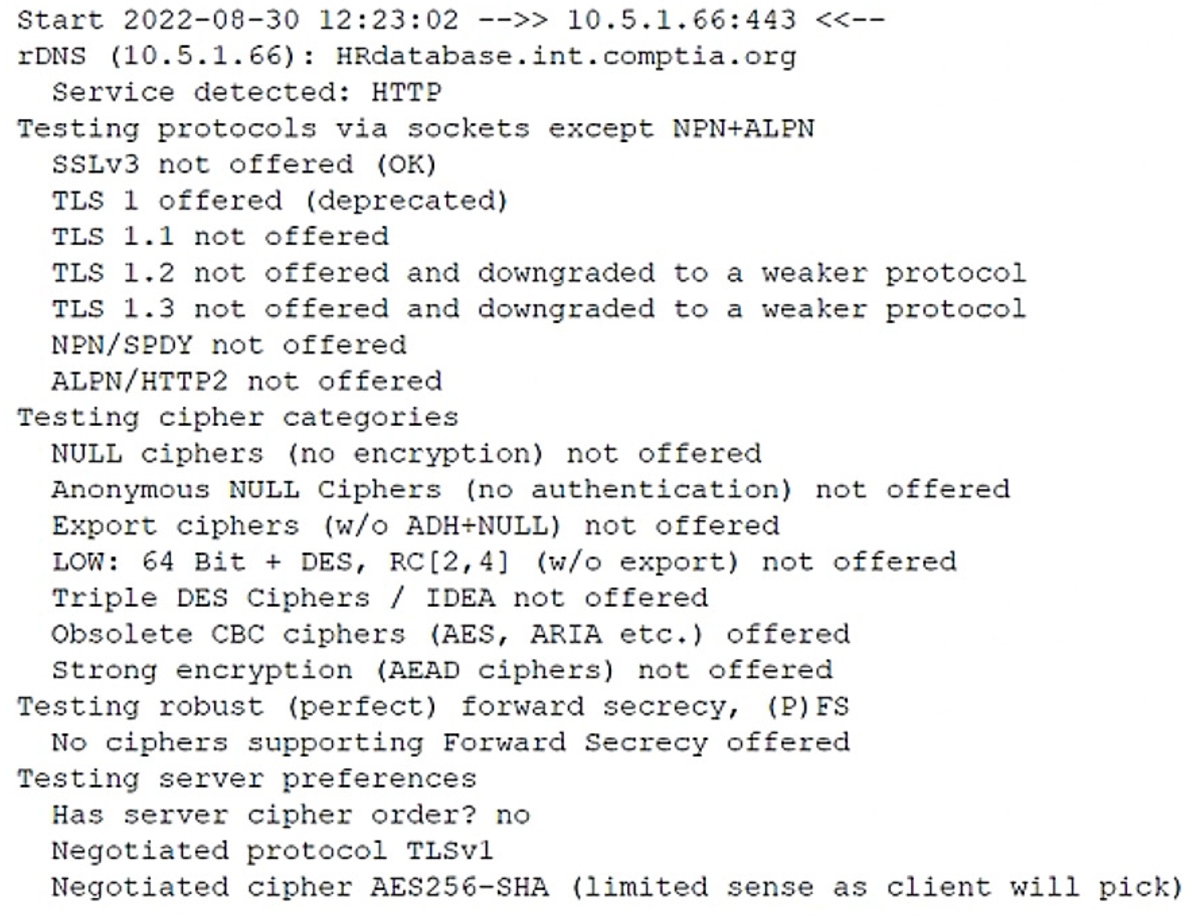
Which of the following attacks would be most likely to succeed, given the output?
- A. NULL and unauthenticated cipher downgrade attack
- B. Availability attack from manipulation of associated authentication data
- C. Padding oracle attack
- D. On-path forced renegotiation to insecure ciphers
