During a software assurance assessment, an engineer notices the source code contains multiple instances of strcpy, which does not verify the buffer length. Which of the following solutions should be integrated into the SDLC process to reduce future risks?
- A. Require custom IDS/IPS detection signatures for each type of insecure function found.
- B. Perform a penetration test before moving to the next step of the SDLC.
- C. Update the company’s secure coding policy to exclude insecure functions.
- D. Perform DAST/SAST scanning before handoff to another team.
A software developer needs to add an authentication method to a web application. The following requirements must be met:
• The web application needs to use well-supported standards.
• The initial login to the web application should rely on an outside, trusted third party.
• The login needs to be maintained for up to six months.
Which of the following would best support these requirements? (Choose two.)
- A. SAML
- B. Kerberos
- C. JWT
- D. RADIUS
- E. EAP
- F. Remote attestation
The management team at a company with a large, aging server environment is conducting a server risk assessment in order to create a replacement strategy. The replacement strategy will be based upon the likelihood a server will fail, regardless of the criticality of the application running on a particular server. Which of the following should be used to prioritize the server replacements?
- A. SLE
- B. MTTR
- C. TCO
- D. MTBF
- E. MSA
A recent security assessment generated a recommendation to transition Wi-Fi to WPA2/WPA3 Enterprise requiring EAP-TLS. Which of the following conditions must be met for the organization’s mobile devices to be able to successfully join the corporate wireless network?
- A. Client computer X.509 certificates have been installed.
- B. Supplicants are configured to provide a 64-bit authenticator.
- C. A hardware TOTP token has been issued to mobile users.
- D. The device’s IPSec configuration matches the VPN concentrator.
A security analyst is reviewing the following output from a vulnerability scan from an organization’s internet-facing web services:
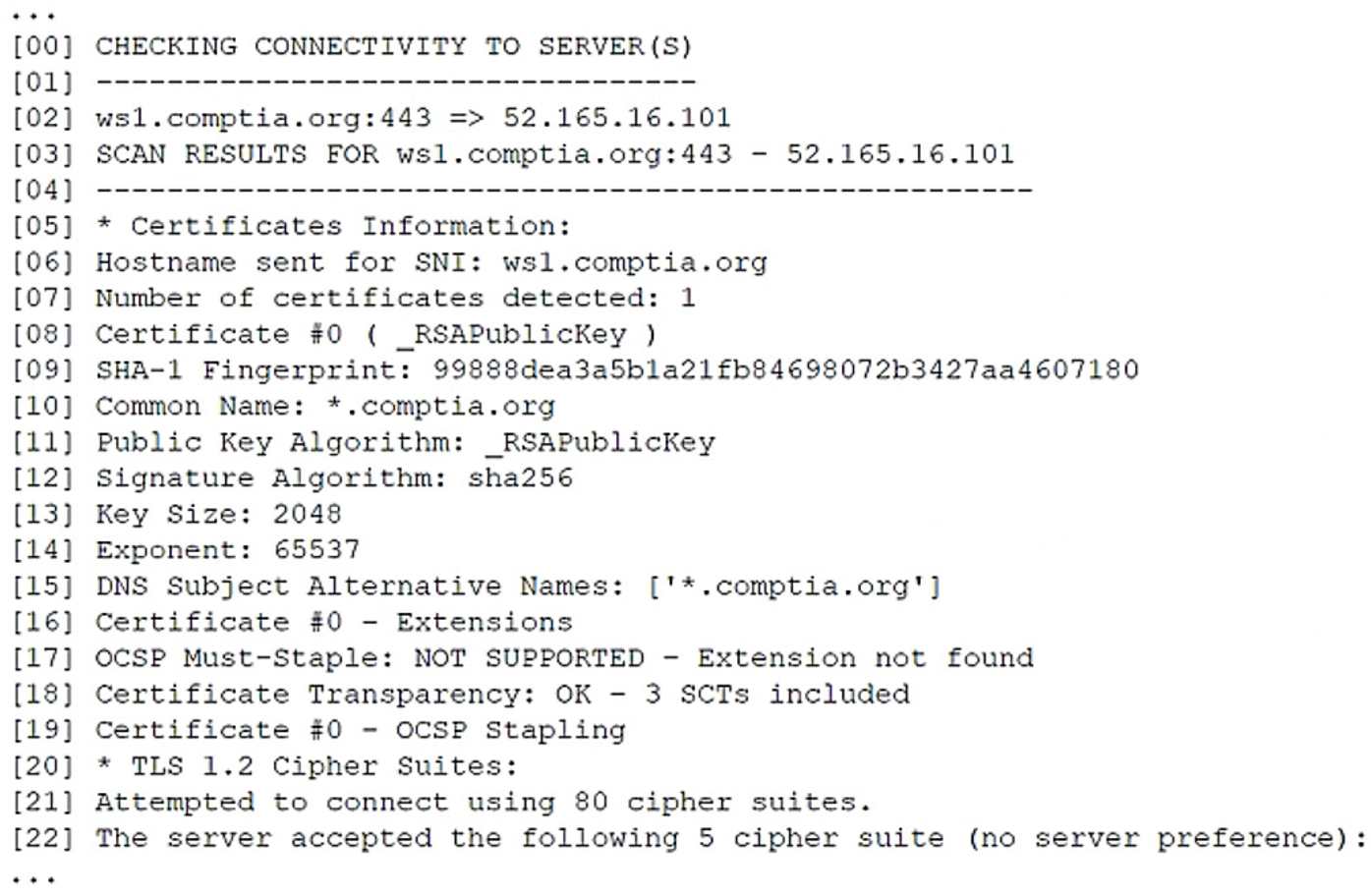
Which of the following indicates a susceptibility whereby an attacker can take advantage of the trust relationship between the client and the server?
- A. Line 06
- B. Line 10
- C. Line 13
- D. Line 17
- E. Line 18
A security team receives alerts regarding impossible travel and possible brute-force attacks after normal business hours. After reviewing more logs, the team determines that specific users were targeted and attempts were made to transfer data to an unknown site. Which of the following should the team do to help mitigate these issues?
- A. Create a firewall rule to prevent those users from accessing sensitive data.
- B. Restrict uploading activity to only authorized sites.
- C. Enable packet captures to continue to run for the source and destination related to the file transfer.
- D. Disable login activity for those users after business hours.
A company that provides services to clients who work with highly sensitive data would like to provide assurance that the data’s confidentiality is maintained in a dynamic, low-risk environment. Which of the following would best achieve this goal? (Choose two.)
- A. Install a SOAR on all endpoints.
- B. Hash all files.
- C. Install SIEM within a SOC.
- D. Encrypt all data and files at rest, in transit, and in use.
- E. Configure SOAR to monitor and intercept files and data leaving the network.
- F. Implement file integrity monitoring.
As part of an organizational risk assessment, the compliance officer has worked with business unit leaders to identify risks and assess impacts to the organization. Which of the following activities should be performed next?
- A. Review risks and assign remediation activities to stakeholders.
- B. Mitigate risk by obtaining a cyber insurance policy.
- C. Perform a gap analysis against application regulatory requirements.
- D. Use a business impact analysis to quantify the ROI for risk mitigation.
A security engineer receives reports through the organization’s bug bounty program about remote code execution in a specific component in a custom application. Management wants to properly secure the component and proactively avoid similar issues. Which of the following is the best approach to uncover additional vulnerable paths in the application?
- A. Implement fuzz testing focused on the component and inputs uncovered by the bug bounty program.
- B. Leverage a software composition analysis tool to find all known vulnerabilities in dependencies.
- C. Use a vulnerability scanner to perform multiple types of network scans to look for vulnerabilities.
- D. Utilize a network traffic analyzer to find malicious packet combinations that lead to remote code execution.
- E. Run an exploit framework with all payloads against the application to see if it is able to gain access.
A security analyst is configuring an IPSec tunnel to use the strongest encryption currently available. Which of the following algorithms should be deployed to provide the most secure initial key exchange?
- A. 3DES
- B. ECDSA
- C. ECDH
- D. AES
