Which of the following is the reason security engineers in the power industry include mechanisms to control power generation equipment via air-gapped and other offline methods?
- A. The ability of some malicious code to maneuver and trigger repeated damaging failures
- B. The capability of ICS control to be centrally managed and logged
- C. The brittleness of electrical relays subject to repeated power cycles over a short period of time
- D. The requirements to maintain administrative systems in the event of a power outage
Several unlabeled documents in a cloud document repository contain cardholder information. Which of the following configuration changes should be made to the DLP system to correctly label these documents in the future?
- A. Digital rights management
- B. Network traffic decryption
- C. Regular expressions
- D. Watermarking
A company is developing an application that will be used to perform e-commerce transactions for a subscription-based service. The application must be able to use previously saved payment methods to perform recurring transactions. Which of the following is the most appropriate?
- A. Tokenization through an HSM.
- B. Self-encrypting disks with field-level encryption
- C. NX/XN implementation to minimize data retention
- D. Token-based access for application users
- E. Address space layout randomization
SIMULATION
–
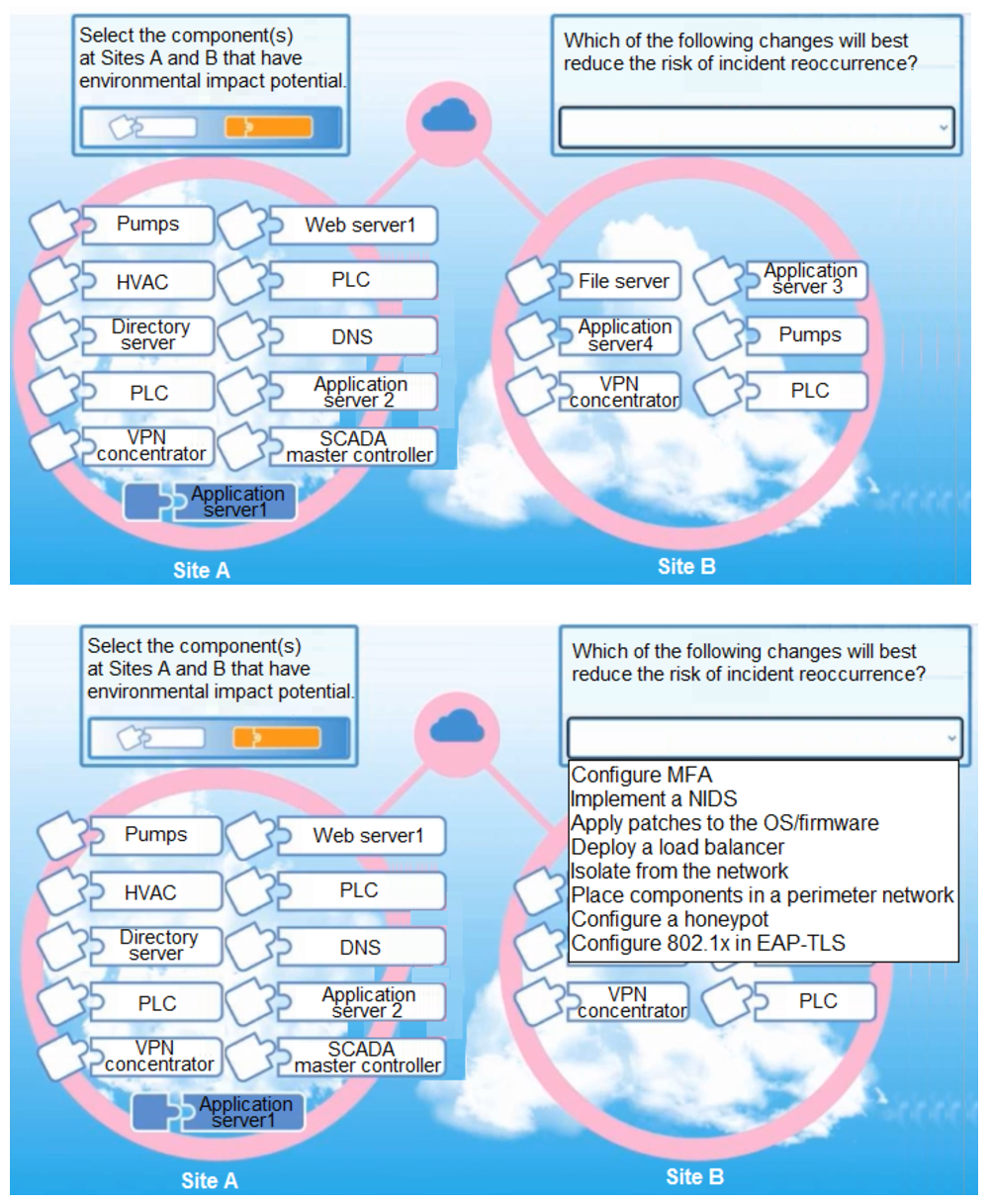
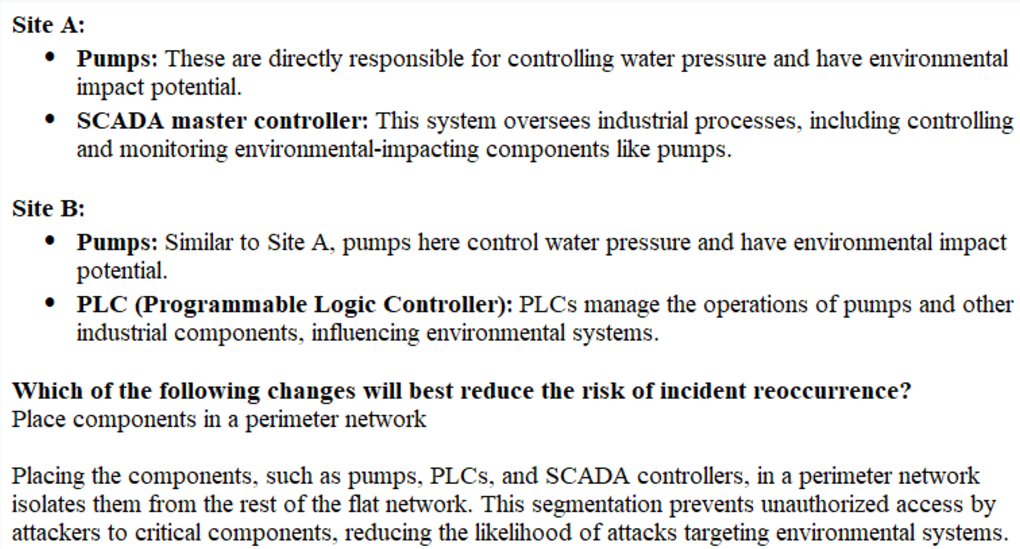
An incident occurred at Site A when an attacker successfully caused water pressure to increase in the pump room.
The organization is concerned about reoccurrence of this attack and that similar attacks might be successful on other cyber-physical systems within the network.
All devices and components reside on a flat network within the 10.1.0.0/16 space.
INSTRUCTIONS
–
Take the appropriate actions to reduce the risk of reoccurrence of this and other environmental security vulnerabilities.
Select the component(s) at Sites A and B that have environmental impact potential. Then, select the corrective action that will best reduce the risk of incident reoccurrence.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Answer :
Due to reports of malware targeting companies in the same industry, an organization wants to develop a comprehensive list of IoCs to determine if the systems might be affected in a similar attack. Which of the following would be best to use to develop this list?
- A. Simulators
- B. Sandbox detonation
- C. Antivirus
- D. Endpoint detection and response
Which of the following is the best way to protect the website browsing history for an executive who travels to foreign countries where internet usage is closely monitored?
- A. DoH
- B. EAP-TLS
- C. Geofencing
- D. Private browsing mode
A company hired a third-party consultant to run a cybersecurity incident simulation in order to identify security gaps and prepare stakeholders for a potential incident. Which of the following best describes this activity?
- A. Tabletop exercise
- B. Walk-through review
- C. Lessons learned
- D. Business impact analysis
A systems administrator discovered that several updates were missing on a system, even though a vulnerability management process is in place. Which of the following processes would allow the administrator to update the systems consistently and provide an accurate view of the system security posture?
- A. Instituting a rigorous change control process
- B. Planning and conducting an annual security review
- C. Continuously monitoring system audit logs
- D. Implementing a scan-patch-scan methodology
A systems engineer is designing the infrastructure for an enterprise client with colocation services from a data center operator. The new infrastructure must protect against threats associated with data exfiltration by malicious insiders who may gain direct access to systems during maintenance operations. Which of the following is the best solution?
- A. Deactivation of unused interfaces
- B. Configuration of anti-malware scanning for USB devices
- C. Usage of 802.1x to limit network access to only authorized systems
- D. Activation of out-of-band maintenance interfaces
A software development company is implementing a SaaS-based password vault for customers to use. The requirements for the password vault include:
• Vault encryption using a variable bloc and key size
• Resistance to brute-force attacks
Which of the following should be implemented to meet these requirements? (Choose two.)
- A. PBKDF2
- B. RC5
- C. AES
- D. P256
- E. ECDSA
- F. RIPEMD
