An organization has an operational requirement with a specific equipment vendor. The organization is located in the United States, but the vendor is located in another region. Which of the following risks would be MOST concerning to the organization in the event of equipment failure?
- A. Support may not be available during all business hours.
- B. The organization requires authorized vendor specialists.
- C. Each region has different regulatory frameworks to follow.
- D. Shipping delays could cost the organization money.
A company has grown rapidly in the past few years and has prioritized building new systems over maintaining and patching legacy systems. Now that company growth has slowed, the company is focusing on patching critical legacy systems. Which of the following best describes what the security team should do to address open vulnerabilities?
- A. Ensure the scan results are compliant with ARF.
- B. Ensure the output of the scan results contains the CVSSv3 for each vulnerability.
- C. Ensure IoCs are included in the vulnerability reports for the management team.
- D. Ensure the CVE is listed in the output of the scan.
A security manager is creating a standard configuration across all endpoints that handle sensitive data. Which of the following techniques should be included in the standard configuration to ensure the endpoints are hardened?
- A. Drive encryption
- B. Patch management
- C. Event logging
- D. Resource monitoring
A regulated company is in the process of refreshing its entire infrastructure. The company has a business-critical process running on an old 2008 Windows server. If this server fails, the company would lose millions of dollars in revenue. Which of the following actions should the company take?
- A. Accept the risk as the cost of doing business.
- B. Create an organizational risk register for project prioritization.
- C. Implement network compensating controls.
- D. Purchase insurance to offset the cost if a failure occurred.
An analyst is working to address a potential compromise of a corporate endpoint and discovers the attacker accessed a user’s credentials. However, it is unclear if the system baseline was modified to achieve persistence. Which of the following would most likely support forensic activities in this scenario?
- A. Side-channel analysis
- B. Bit-level disk duplication
- C. Software composition analysis
- D. SCAP scanner
A security engineer needs to ensure production containers are automatically scanned for vulnerabilities before they are accepted into the production environment. Which of the following should the engineer use to automatically incorporate vulnerability scanning on every commit?
- A. Code repository
- B. CI/CD pipeline
- C. Integrated development environment
- D. Container orchestrator
A security architect is making recommendations for a new system that will be built to store and exchange health records. The application will be a single-page application that calls server-side, web-based API endpoints. Due to compliance implications, the system must meet the following security requirements:
• Resistance to session takeover attacks
• Able to revoke access if a system compromise is suspected
• Able to authenticate the user by employing best practices
Which of the following should the architect do to best meet the requirements?
- A. Implement OpenID Connect with granular scopes for data access.
- B. Leverage OAuth with the implicit Grant type.
- C. Configure role-based access control using LDAP.
- D. Utilize Kerberos to implement role-based access control.
- E. Use the Extensible Authentication Protocol.
A security architect discovers the following page while testing a website for vulnerabilities: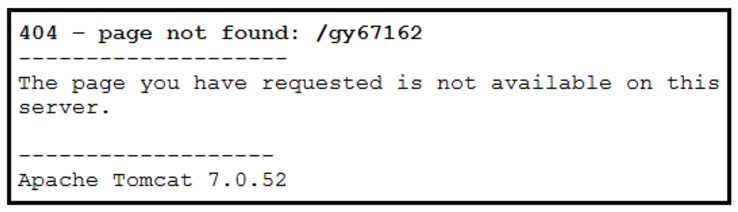
Which of the following best describes why this issue should be corrected?
- A. The website is generating a server error.
- B. The URL for this page can be used for directory traversal.
- C. The website fuzzing tool has overloaded the server’s capacity.
- D. The information can be used for more targeted attacks.
A security engineer would like to control configurations on mobile devices while fulfilling the following requirements:
• Support and control Apple and Android devices.
• The device must be corporate-owned.
Which of the following would enable the engineer to meet these requirements? (Choose two.)
- A. Create a group policy to lock down mobile devices.
- B. Update verbiage in the acceptable use policy for the internet.
- C. Implement an MDM solution.
- D. Implement a captive portal solution.
- E. Update policy to prohibit the use of BYOD devices.
- F. Implement a RADIUS solution.
A mobile gaming company wants to secure the newest version of a game against an on-path attack. The company hires a security architect to perform a threat modeling exercise. Which of the following is the best solution for the architect to recommend?
- A. Requiring certificate pinning in the mobile application
- B. Setting up obfuscation techniques to make reverse engineering more difficult.
- C. Configuring client authentication using certificates within the mobile application.
- D. Developing checks within the application for rooted devices.
