Several application users are no longer able to process orders in large batches after a new DLP system with several policies enabled was installed. Additionally, users are unable to access large Excel documents and XML files, which are required to finalize orders. The security team notices several files have been recently removed and sees the following OLP alerts:
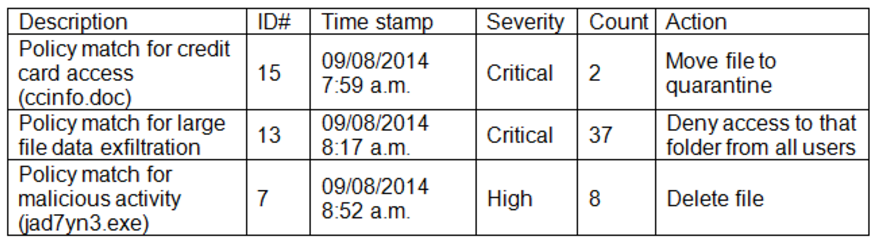
Which of the following will enable the application to process the orders as needed?
- A. Removing the affected files from quarantine
- B. Changing the action for the data exfiltration to alert
- C. Retrieving the deleted files from the recycle bin
- D. Permanently disabling all recent DLP policy changes
Question 552
A retail organization wants to properly test and verify its capabilities to detect and/or prevent specific TTPs as mapped to the MITRE ATT&CK framework specific to APTs. Which of the following should be used by the organization to accomplish this goal?
- A. Tabletop exercise
- B. Penetration test
- C. Sandbox detonation
- D. Honeypot
An organization’s UTM blocked unexpected traffic. After reviewing the following summary of the event, the security engineer categorized this event as a data exfiltration attempt:
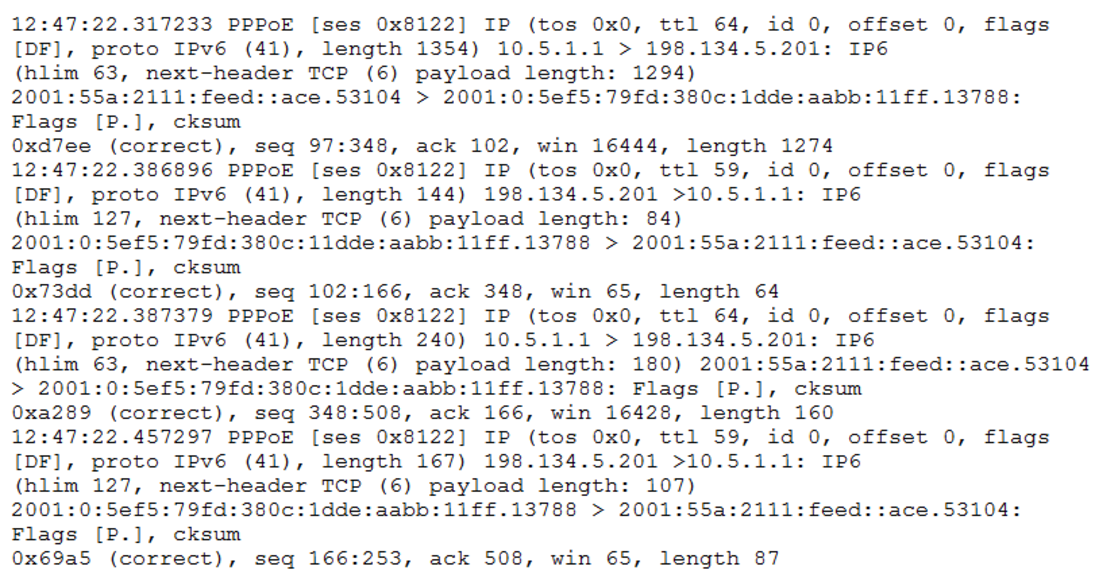
Which of the following explains why the engineer thinks this event is a data exfiltration attempt?
- A. The traffic indicated the request was dropped by the UTM.
- B. 6to4 was used to obfuscate the data.
- C. The traffic indicated a subsecond request-response time.
- D. The data was hidden steganographically in IP headers.
During an adversarial simulation exercise, an external team was able to gain access to sensitive information and systems without the organization detecting this activity. Which of the following mitigation strategies should the organization use to best resolve the findings?
- A. Configuring a honeypot for adversary characterization
- B. Leveraging simulators for attackers
- C. Setting up a honey network for attackers
- D. Utilizing decoy accounts and documents
An analyst needs to evaluate all images and documents that are publicly shared on a website. Which of the following would be the best tool to evaluate the metadata of these files?
- A. OllyDbg
- B. ExifTool
- C. Volatility
- D. Ghidra
The Chief Information Security Officer of a large multinational organization has asked the security risk manager to use risk scenarios during a risk analysis. Which of the following is the most likely reason for this approach?
- A. To connect risks to business objectives
- B. To ensure a consistent approach to risk
- C. To present a comprehensive view of risk
- D. To provide context to the relevancy of risk
A recent risk assessment revealed that users transferred data to and from unauthorized sites through terminal services. The security team needs to implement technical controls that allow specific employees to connect remotely and securely throughout the network. Which of the following data security techniques should the team use? (Choose two.)
- A. Web content filter
- B. Bastion host
- C. Network traffic decryption/deep packet inspection
- D. Tokenization
- E. Data masking
- F. Blocking the use of external media
A security engineer is performing a vulnerability management scan on multihomed Linux systems. The engineer notices that the vulnerability count is high due to the fact that each vulnerability is multiplied by the number of NICs on each system. Which of the following should the engineer do to deduplicate the vulnerabilities and to associate the vulnerabilities with a particular host?
- A. Use a SCAP scanner.
- B. Deploy an agent.
- C. Initiate a discovery scan.
- D. Perform an Nmap scan.
A security analyst is reviewing recently released CVEs for software used on servers. Given the following information:
CVE-1: AV:N/PR:L/AC:H/UI:R –
CVE-2: AV:L/PR:H/AC:H/UI:N –
CVE-3: AV:N/PR:L/AC:L/UI:N –
CVE-4: AV:P/PR:H/AC:L/UI:R –
CVE-5: AV:N/PR:H/AC: H/UI:N –
Which of the following CVEs should the security analyst prioritize first?
- A. CVE-1
- B. CVE-2
- C. CVE-3
- D. CVE-4
- E. CVE-5
A security analyst received the following finding from a cloud security assessment tool:
Virtual Machine Data Disk is encrypted with the default encryption key.
Because the organization hosts highly sensitive data files, regulations dictate it must be encrypted so it is unreadable to the CSP. Which of the following should be implemented to remediate the finding and meet the regulatory requirement? (Choose two.)
- A. Disk encryption with customer-provided keys
- B. Disk encryption with keys from a third party
- C. Row-level encryption with a key escrow
- D. File-level encryption with cloud vendor-provided keys
- E. File-level encryption with customer-provided keys
- F. Disk-level encryption with a cross-signed certificate
