A medium-sized business wants to deploy laptops for remote employees. The deployment must provide higher control and authority over the devices, but also allow employees the flexibility to install their preferred software of choice. Which of the following is the best deployment option, given these requirements?
- A. BYOD
- B. CYOD
- C. COPE
- D. CO
Which of the following items should be included when crafting a disaster recovery plan?
- A. Redundancy
- B. Testing exercises
- C. Autoscaling
- D. Competitor locations
After a server was compromised, an incident responder looks at log files to determine the attack vector that was used. The incident responder reviews the web server log files from the time before an unexpected SSH session began:
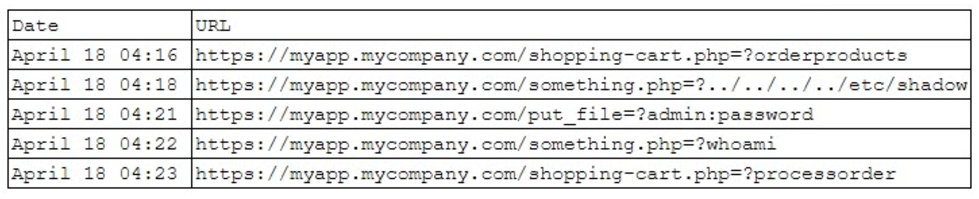
Which of the following is the most likely vulnerability that was exploited, based on the log files?
- A. Directory traversal revealed the hashed SSH password, which was used to access the server.
- B. A SQL injection was used during the ordering process to compromise the database server.
- C. The root password was easily guessed and used as a parameter to open a reverse shell.
- D. An outdated, third-party PHP plug-in was vulnerable to a known remote code execution.
A small software company deployed a new web application after a network security scan found no vulnerabilities. A customer using this application reported malicious activity believed to be associated with the application. During an investigation, the company discovered that the customer closed the browser tab and connected to another application, using the same credentials on both platforms. Which of the following detection methods should the software company implement before deploying the next version?
- A. Multifactor authentication
- B. Static application code scanning
- C. Stronger password policy
- D. A SIEM
