
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A company is deploying new vulnerability scanning software to assess its systems. The current network is highly segmented, and the networking team wants to minimize the number of unique firewall rules. Which of the following scanning techniques would be most efficient to achieve the objective?
- A. Deploy agents on all systems to perform the scans
- B. Deploy a central scanner and perform non-credentialed scans
- C. Deploy a cloud-based scanner and perform a network scan
- D. Deploy a scanner sensor on every segment and perform credentialed scans
An organization’s email account was compromised by a bad actor. Given the following information:
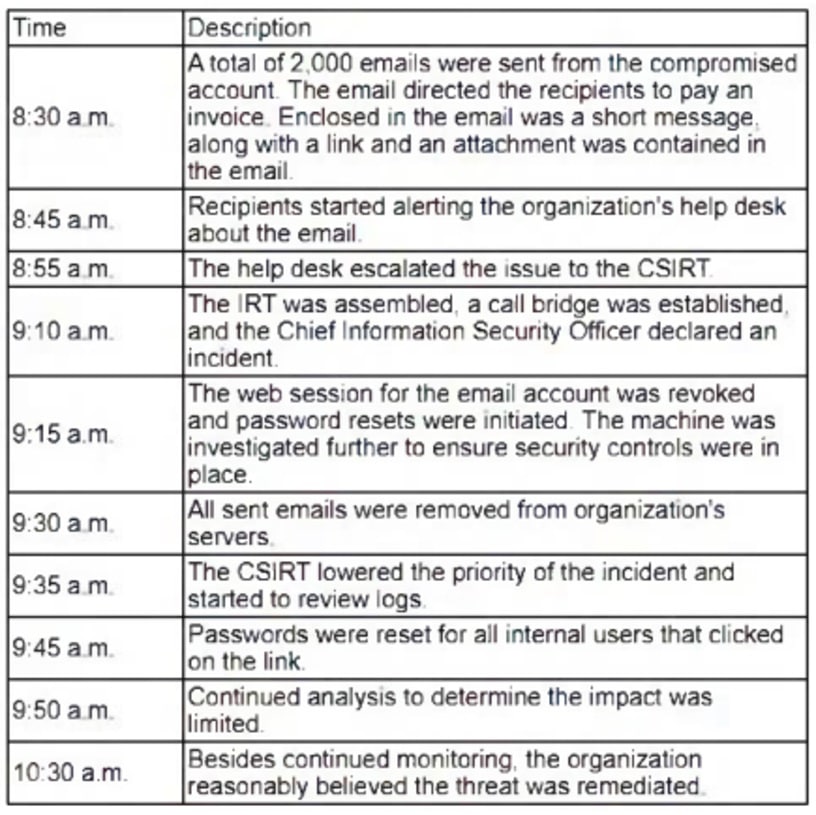
Which of the following is the length of time the team took to detect the threat?
- A. Data masking
- B. Hashing
- C. Watermarking
- D. Encoding
A security administrator needs to import PII data records from the production environment to the test environment for testing purposes. Which of the following would best protect data confidentiality?
- A. Data masking
- B. Hashing
- C. Watermarking
- D. Encoding
The email system administrator for an organization configured DKIM signing for all email legitimately sent by the organization. Which of the following would most likely indicate an email is malicious if the company’s domain name is used as both the sender and the recipient?
- A. The message fails a DMARC check
- B. The sending IP address is the hosting provider
- C. The signature does not meet corporate standards
- D. The sender and reply address are different
During an incident involving phishing, a security analyst needs to find the source of the malicious email. Which of the following techniques would provide the analyst with this information?
- A. Header analysis
- B. Packet capture
- C. SSL inspection
- D. Reverse engineering
An analyst wants to ensure that users only leverage web-based software that has been pre-approved by the organization. Which of the following should be deployed?
- A. Blocklisting
- B. Allowlisting
- C. Graylisting
- D. Webhooks
During a cybersecurity incident, one of the web servers at the perimeter network was affected by ransomware. Which of the following actions should be performed immediately?
- A. Shut down the server.
- B. Reimage the server.
- C. Quarantine the server.
- D. Update the OS to latest version.
An organization recently changed its BC and DR plans. Which of the following would best allow for the incident response team to test the changes without any impact to the business?
- A. Perform a tabletop drill based on previously identified incident scenarios.
- B. Simulate an incident by shutting down power to the primary data center.
- C. Migrate active workloads from the primary data center to the secondary location.
- D. Compare the current plan to lessons learned from previous incidents.
Security analysts review logs on multiple servers on a daily basis. Which of the following implementations will give the best central visibility into the events occurring throughout the corporate environment without logging in to the servers individually?
- A. Deploy a database to aggregate the logging
- B. Configure the servers to forward logs to a SIEM
- C. Share the log directory on each server to allow local access.
- D. Automate the emailing of logs to the analysts.
Following a recent security incident, the Chief Information Security Officer is concerned with improving visibility and reporting of malicious actors in the environment. The goal is to reduce the time to prevent lateral movement and potential data exfiltration. Which of the following techniques will best achieve the improvement?
- A. Mean time to detect
- B. Mean time to respond
- C. Mean time to remediate
- D. Service-level agreement uptime
