
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
After identifying a threat, a company has decided to implement a patch management program to remediate vulnerabilities. Which of the following risk management principles is the company exercising?
- A. Transfer
- B. Accept
- C. Mitigate
- D. Avoid
A security analyst discovers an ongoing ransomware attack while investigating a phishing email. The analyst downloads a copy of the file from the email and isolates the affected workstation from the network. Which of the following activities should the analyst perform next?
- A. Wipe the computer and reinstall software
- B. Shut down the email server and quarantine it from the network
- C. Acquire a bit-level image of the affected workstation
- D. Search for other mail users who have received the same file
The security analyst received the monthly vulnerability report. The following findings were included in the report:
• Five of the systems only required a reboot to finalize the patch application
• Two of the servers are running outdated operating systems and cannot be patched
The analyst determines that the only way to ensure these servers cannot be compromised is to isolate them. Which of the following approaches will best minimize the risk of the outdated servers being compromised?
- A. Compensating controls
- B. Due diligence
- C. Maintenance windows
- D. Passive discovery
The vulnerability analyst reviews threat intelligence regarding emerging vulnerabilities affecting workstations that are used within the company:
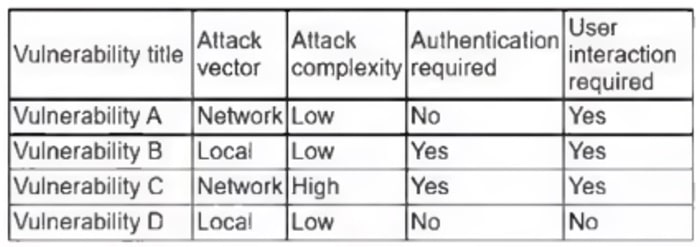
Which of the following vulnerabilities should the analyst be most concerned about, knowing that end users frequently click on malicious links sent via email?
- A. Vulnerability A
- B. Vulnerability B
- C. Vulnerability C
- D. Vulnerability D
An incident response analyst is taking over an investigation from another analyst. The investigation has been going on for the past few days. Which of the following steps is most important during the transition between the two analysts?
- A. Identify and discuss the lessons learned with the prior analyst.
- B. Accept all findings and continue to investigate the next item target.
- C. Review the steps that the previous analyst followed.
- D. Validate the root cause from the prior analyst.
A company recently removed administrator rights from all of its end user workstations. An analyst uses CVSSv3.1 exploitability metrics to prioritize the vulnerabilities for the workstations and produces the following information:
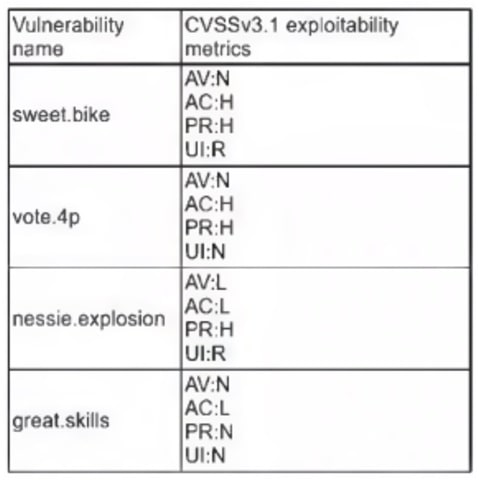
Which of the following vulnerabilities should be prioritized for remediation?
- A. nessie.explosion
- B. vote.4p
- C. sweet.bike
- D. great.skills
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
- A. Increasing training and awareness for all staff
- B. Ensuring that malicious websites cannot be visited
- C. Blocking all scripts downloaded from the internet
- D. Disabling all staff members’ ability to run downloaded applications
A security analyst at a company is reviewing an alert from the file integrity monitoring indicating a mismatch in the login. html file hash. After comparing the code with the previous version of the page source code, the analyst found the following code snippet added:
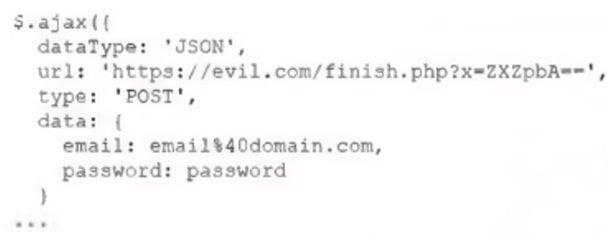
Which of the following best describes the activity the analyst has observed?
- A. Obfuscated links
- B. Exfiltration
- C. Unauthorized changes
- D. Beaconing
A security administrator has been notified by the IT operations department that some vulnerability reports contain an incomplete list of findings. Which of the following methods should be used to resolve this issue?
- A. Credentialed scar
- B. External scan
- C. Differential scan
- D. Network scan
Question 140
An organization enabled a SIEM rule to send an alert to a security analyst distribution list when ten failed logins occur within one minute. However, the control was unable to detect an attack with nine failed logins. Which of the following best represents what occurred?
- A. False positive
- B. True negative
- C. False negative
- D. True positive
