
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
After completing a review of network activity, the threat hunting team discovers a device on the network that sends an outbound email via a mail client to a non-company email address daily at 10:00 p.m. Which of the following is potentially occurring?
- A. Irregular peer-to-peer communication
- B. Rogue device on the network
- C. Abnormal OS process behavior
- D. Data exfiltration
A vulnerability scanner generates the following output:
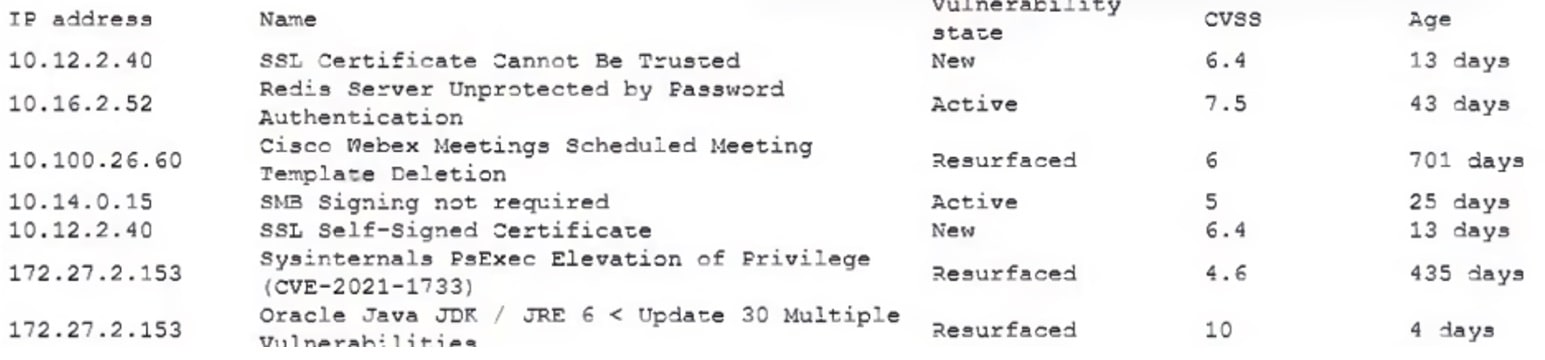
The company has an SLA for patching that requires time frames to be met for high-risk vulnerabilities. Which of the following should the analyst prioritize first for remediation?
- A. Oracle JDK
- B. Cisco Webex
- C. Redis Server
- D. SSL Self-signed Certificate
A web application team notifies a SOC analyst that there are thousands of HTTP/404 events on the public-facing web server. Which of the following is the next step for the analyst to take?
- A. Instruct the firewall engineer that a rule needs to be added to block this external server
- B. Escalate the event to an incident and notify the SOC manager of the activity
- C. Notify the incident response team that there is a DDoS attack occurring
- D. Identify the IP/hostname for the requests and look at the related activity
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system application, or user base is affected by an uptime availability outage?
- A. Timeline
- B. Evidence
- C. Impact
- D. Scope
A security analyst needs to provide evidence of regular vulnerability scanning on the company’s network for an auditing process. Which of the following is an example of a tool that can produce such evidence?
- A. OpenVAS
- B. Burp Suite
- C. Nmap
- D. Wireshark
A security analyst performs a vulnerability scan. Based on the metrics from the scan results, the analyst must prioritize which hosts to patch. The analyst runs the tool and receives the following output:
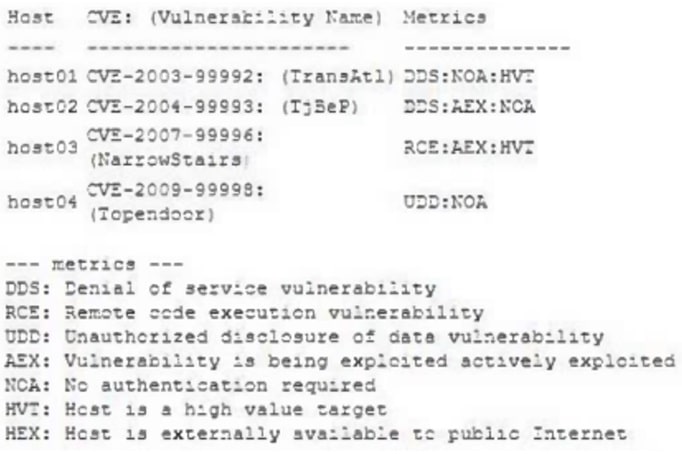
Which of the following hosts should be patched first, based on the metrics?
- A. host01
- B. host02
- C. host03
- D. host04
An organization receives a legal hold request from an attorney. The request pertains to emails related to a disputed vendor contract. Which of the following is the best step for the security team to take to ensure compliance with the request?
- A. Publicly disclose the request to other vendors
- B. Notify the departments involved to preserve potentially relevant information
- C. Establish a chain of custody starting with the attorney’s request
- D. Back up the mailboxes on the server and provide the attorney with a copy
A company has the following security requirements:
• No public IPs
• All data secured at rest
• No insecure ports/protocols
After a cloud scan is completed a security analyst receives reports that several misconfigurations are putting the company at risk. Given the following cloud scanner output:

Which of the following should the analyst recommend be updated first to meet the security requirements and reduce risks?
- A. VM_PRD_DB
- B. VM_DEV_DB
- C. VM_DEV_Web02
- D. VM_PRD_Web01
Which of the following best describes the actions taken by an organization after the resolution of an incident that addresses issues and reflects on the growth opportunities for future incidents?
- A. Lessons learned
- B. Scrum review
- C. Root cause analysis
- D. Regulatory compliance
An analyst is becoming overwhelmed with the number of events that need to be investigated for a timeline. Which of the following should the analyst focus on in order to move the incident forward?
- A. Impact
- B. Vulnerability score
- C. Mean time to detect
- D. Isolation
