
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
To minimize the impact of a security incident, a cybersecurity analyst has configured audit settings in the organization’s cloud services. Which of the following security controls has the analyst configured?
- A. Preventive
- B. Corrective
- C. Directive
- D. Detective
A web developer reports the following error that appeared on a development server when testing a new application:
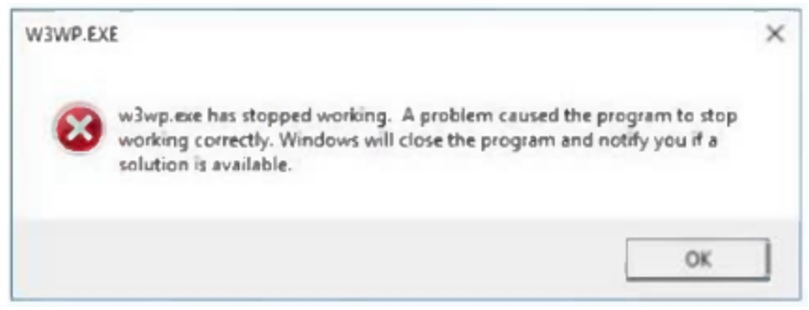
Which of the following tools can be used to identify the application’s point of failure?
- A. OpenVAS
- B. Angry IP scanner
- C. Immunity debugger
- D. Burp Suite
Which of the following describes a contract that is used to define the various levels of maintenance to be provided by an external business vendor in a secure environment?
- A. MOU
- B. NDA
- C. BIA
- D. SLA
A security team is concerned about recent Layer 4 DDoS attacks against the company website. Which of the following controls would best mitigate the attacks?
- A. Block the attacks using firewall rules
- B. Deploy an IPS in the perimeter network
- C. Roll out a CDN
- D. Implement a load balancer
An analyst is reviewing system logs while threat hunting:
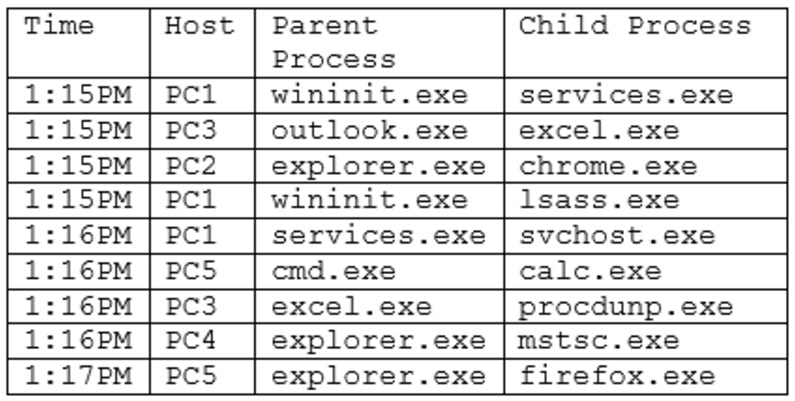
Which of the following hosts should be investigated first?
- A. PC1
- B. PC2
- C. PC3
- D. PC4
- E. PC5
An organization needs to bring in data collection and aggregation from various endpoints. Which of the following is the best tool to deploy to help analysts gather this data?
- A. DLP
- B. NAC
- C. EDR
- D. NIDS
A regulated organization experienced a security breach that exposed a list of customer names with corresponding PII data. Which of the following is the best reason for developing the organization’s communication plans?
- A. For the organization’s public relations department to have a standard notification
- B. To ensure incidents are immediately reported to a regulatory agency
- C. To automate the notification to customers who were impacted by the breach
- D. To have approval from executive leadership on when communication should occur
A penetration tester is conducting a test on an organization’s software development website. The penetration tester sends the following request to the web interface:
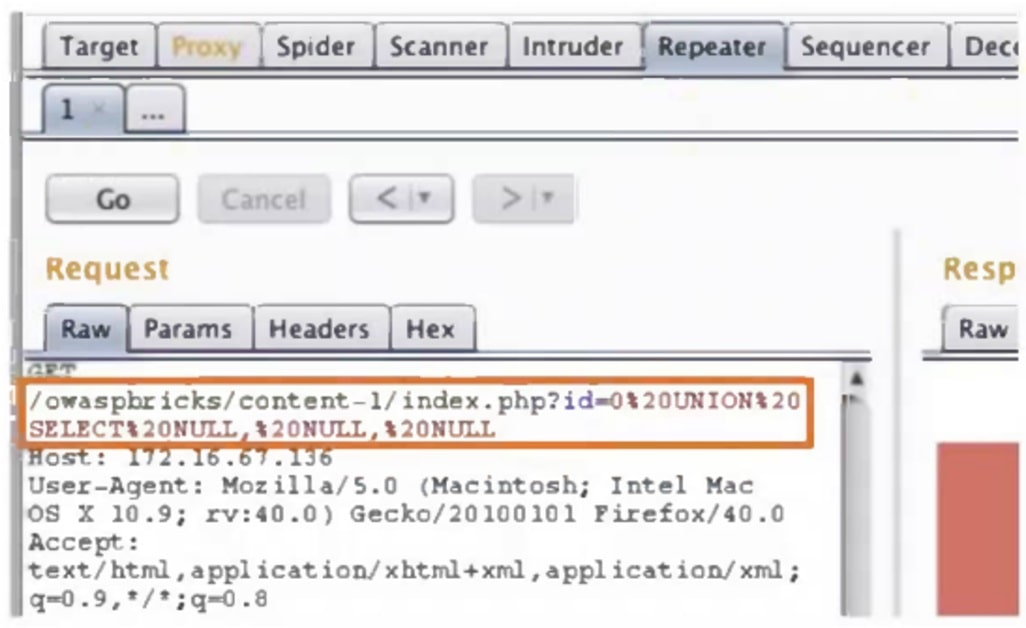
Which of the following exploits is most likely being attempted?
- A. SQL injection
- B. Local file inclusion
- C. Cross-site scripting
- D. Directory traversal
An administrator has noticed mobile devices from an adjacent company on the corporate wireless network. Malicious activity is being reported from those devices.
To add another layer of security in an enterprise environment, an administrator wants to add contextual authentication to allow users to access enterprise resources only while present in corporate buildings. Which of the following technologies would accomplish this?
- A. Port security
- B. Rogue device detection
- C. Bluetooth
- D. GPS
Two employees in the finance department installed a freeware application that contained embedded malware. The network is robustly segmented based on areas of responsibility. These computers had critical sensitive information stored locally that needs to be recovered. The department manager advised all department employees to turn off their computers until the security team could be contacted about the issue. Which of the following is the first step the incident response staff members should take when they arrive?
- A. Turn on all systems, scan for infection, and back up data to a USB storage device.
- B. Identify and remove the software installed on the impacted systems in the department.
- C. Explain that malware cannot truly be removed and then reimage the devices.
- D. Log on to the impacted systems with an administrator account that has privileges to perform backups.
- E. Segment the entire department from the network and review each computer offline.
