
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A manufacturer has hired a third-party consultant to assess the security of an OT network that includes both fragile and legacy equipment. Which of the following must be considered to ensure the consultant does no harm to operations?
- A. Employing Nmap Scripting Engine scanning techniques
- B. Preserving the state of PLC ladder logic prior to scanning
- C. Using passive instead of active vulnerability scans
- D. Running scans during off-peak manufacturing hours
A team of analysts is developing a new internal system that correlates information from a variety of sources, analyzes that information, and then triggers notifications according to company policy. Which of the following technologies was deployed?
- A. SIEM
- B. SOAR
- C. IPS
- D. CERT
Which of following would best mitigate the effects of a new ransomware attack that was not properly stopped by the company antivirus?
- A. Install a firewall.
- B. Implement vulnerability management.
- C. Deploy sandboxing.
- D. Update the application blocklist.
A Chief Information Security Officer wants to implement security by design, starting with the implementation of a security scanning method to identify vulnerabilities, including SQL injection, RFI, XSS, etc. Which of the following would most likely meet the requirement?
- A. Reverse engineering
- B. Known environment testing
- C. Dynamic application security testing
- D. Code debugging
A security analyst scans a host and generates the following output:
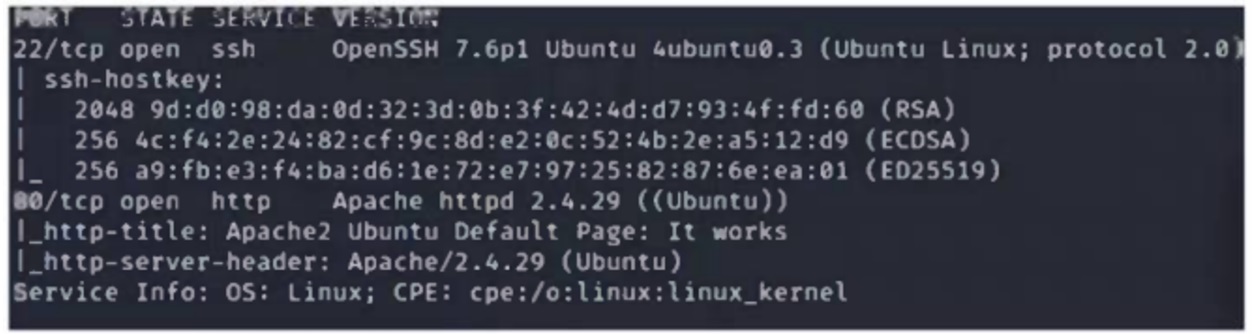
Which of the following best describes the output?
- A. The host is unresponsive to the ICMP request.
- B. The host is running a vulnerable mail server.
- C. The host is allowing unsecured FTP connections.
- D. The host is vulnerable to web-based exploits.
The security team at a company, which was a recent target of ransomware, compiled a list of hosts that were identified as impacted and in scope for this incident. Based on the following host list:
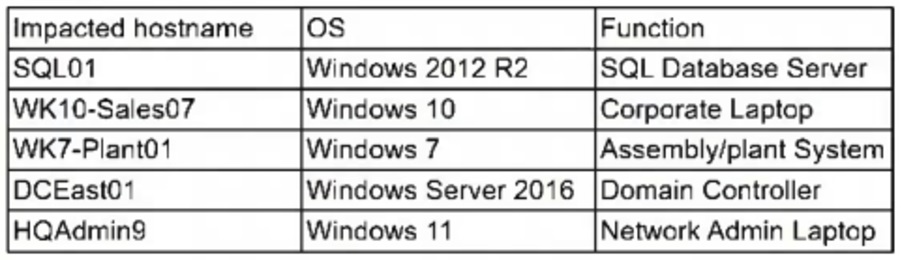
Which of the following systems was most pivotal to the threat actor in its distribution of the encryption binary via Group Policy?
- A. SQL01
- B. WK10-Sales07
- C. WK7-Plant01
- D. DCEast01
- E. HQAdmin9
After a security assessment was done by a third-party consulting firm, the cybersecurity program recommended integrating DLP and CASE to reduce analyst alert fatigue. Which of the following is the best possible outcome that this effort hopes to achieve?
- A. SIEM ingestion logs are reduced by 20%.
- B. Phishing alerts drop by 20%.
- C. False positive rates drop to 20%.
- D. The MTTR decreases by 20%.
Which of the following threat actors is most likely to target a company due to its questionable environmental policies?
- A. Hacktivist
- B. Organized crime
- C. Nation-state
- D. Lone wolf
A cybersecurity analyst is recording the following details:
• ID
• Name
• Description
• Classification of information
• Responsible party
In which of the following documents is the analyst recording this information?
- A. Risk register
- B. Change control documentation
- C. Incident response playbook
- D. Incident response plan
A SOC manager is establishing a reporting process to manage vulnerabilities. Which of the following would be the best solution to identify potential loss incurred by an issue?
- A. Trends
- B. Risk score
- C. Mitigation
- D. Prioritization
