
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
An organization would like to ensure its cloud infrastructure has a hardened configuration. A requirement is to create a server image that can be deployed with a secure template. Which of the following is the best resource to ensure secure configuration?
- A. CIS Benchmarks
- B. PCI DSS
- C. OWASP Top Ten
- D. ISO 27001
A company uses self-signed certificates when sending emails to recipients within the company. Users are calling the help desk because they are getting warnings when attempting to open emails sent by internal users. A security analyst checks the certificates and sees the following
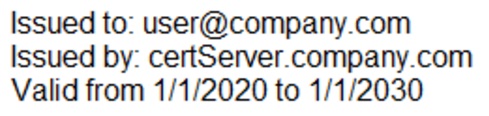
Which of the following should the security analyst conclude?
- A. user@company.com is a malicious insider.
- B. The valid dates are too far apart and are generating the alerts
- C. certServer has been compromised
- D. The root certificate was not installed in the trusted store.
Which of the following stakeholders are most likely to receive a vulnerability scan report? (Choose two.)
- A. Executive management
- B. Law enforcement
- C. Marketing
- D. Legal
- E. Product owner
- F. Systems administration
Which of the following techniques can help a SOC team to reduce the number of alerts related to the internal security activities that the analysts have to triage?
- A. Enrich the SIEM-ingested data to include all data required for triage
- B. Schedule a task to disable alerting when vulnerability scans are executing
- C. Filter all alarms in the SIEM with low seventy
- D. Add a SOAR rule to drop irrelevant and duplicated notifications
An analyst is evaluating a vulnerability management dashboard. The analyst sees that a previously remediated vulnerability has reappeared on a database server. Which of the following is the most likely cause?
- A. The finding is a false positive and should be ignored.
- B. A rollback had been executed on the instance.
- C. The vulnerability scanner was configured without credentials.
- D. The vulnerability management software needs to be updated.
Question 216
A company has decided to expose several systems to the internet. The systems are currently available internally only. A security analyst is using a subset of CVSS3.1 exploitability metrics to prioritize the vulnerabilities that would be the most exploitable when the systems are exposed to the internet. The systems and the vulnerabilities are shown below:
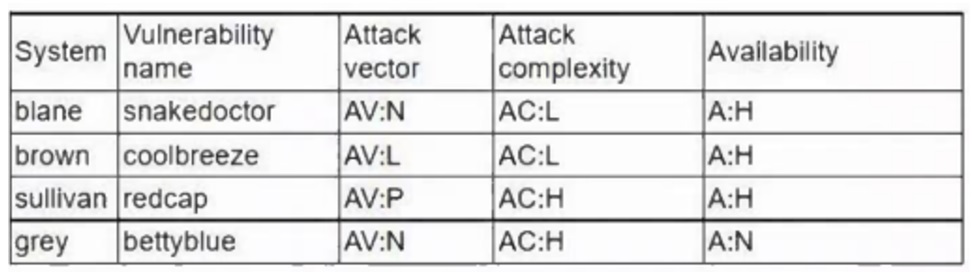
Which of the following systems should be prioritized for patching?
- A. brown
- B. grey
- C. blane
- D. sullivan
During an incident in which a user machine was compromised, an analyst recovered a binary file that potentially caused the exploitation. Which of the following techniques could be used for further analysis?
- A. Fuzzing
- B. Static analysis
- C. Sandboxing
- D. Packet capture
A leader on the vulnerability management team is trying to reduce the team’s workload by automating some simple but time-consuming tasks. Which of the following activities should the team leader consider first?
- A. Assigning a custom recommendation for each finding
- B. Analyzing false positives
- C. Rendering an additional executive report
- D. Regularly checking agent communication with the central console
The Chief Information Security Officer (CISO) of a large management firm has selected a cybersecurity framework that will help the organization demonstrate its investment in tools and systems to protect its data. Which of the following did the CISO most likely select?
- A. PCI DSS
- B. COBIT
- C. ISO 27001
- D. ITIL
A high volume of failed RDP authentication attempts was logged on a critical server within a one-hour period. All of the attempts originated from the same remote IP address and made use of a single valid domain user account. Which of the following would be the most effective mitigating control to reduce the rate of success of this brute-force attack?
- A. Enabling a user account lockout after a limited number of failed attempts
- B. Installing a third-party remote access tool and disabling RDP on all devices
- C. Implementing a firewall block for the remote system’s IP address
- D. Increasing the verbosity of log-on event auditing on all devices
