
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
An incident response analyst is investigating the root cause of a recent malware outbreak. Initial binary analysis indicates that this malware disables host security services and performs cleanup routines on its infected hosts, including deletion of initial dropper and removal of event log entries and prefetch files from the host. Which of the following data sources would most likely reveal evidence of the root cause? (Choose two.)
- A. Creation time of dropper
- B. Registry artifacts
- C. EDR data
- D. Prefetch files
- E. File system metadata
- F. Sysmon event log
When undertaking a cloud migration of multiple SaaS applications, an organization’s systems administrators struggled with the complexity of extending identity and access management to cloud-based assets. Which of the following service models would have reduced the complexity of this project?
- A. CASB
- B. SASE
- C. ZTNA
- D. SWG
Audit and system logs are being forwarded to a syslog solution. An administrator observes that two application servers have not generated any logs for a period of three days, while others continue to send logs normally. Which of the following BEST explains what is occurring?
- A. There is a configuration failure in the syslog solution
- B. The application servers were migrated to the cloud as IaaS instances
- C. The application administrators have not performed any activity in those servers
- D. There is a local firewall policy restriction on the syslog server
A security analyst is responding to an incident that involves a malicious attack on a network data closet. Which of the following best explains how the analyst should properly document the incident?
- A. Back up the configuration file for all network devices.
- B. Record and validate each connection.
- C. Create a full diagram of the network infrastructure.
- D. Take photos of the impacted items.
A cybersecurity analyst is participating with the DLP project team to classify the organization’s data. Which of the following is the primary purpose for classifying data?
- A. To identify regulatory compliance requirements
- B. To facilitate the creation of DLP rules
- C. To prioritize IT expenses
- D. To establish the value of data to the organization
A security analyst observed the following activity from a privileged account:
• Accessing emails and sensitive information
• Audit logs being modified
• Abnormal log-in times
Which of the following best describes the observed activity?
- A. Irregular peer-to-peer communication
- B. Unauthorized privileges
- C. Rogue devices on the network
- D. Insider attack
A vulnerability management team found four major vulnerabilities during an assessment and needs to provide a report for the proper prioritization for further mitigation. Which of the following vulnerabilities should have the highest priority for the mitigation process?
- A. A vulnerability that has related threats and IoCs, targeting a different industry
- B. A vulnerability that is related to a specific adversary campaign, with IoCs found in the SIEM
- C. A vulnerability that has no adversaries using it or associated IoCs
- D. A vulnerability that is related to an isolated system, with no IoCs
A security analyst received an alert regarding multiple successful MFA log-ins for a particular user. When reviewing the authentication logs, the analyst sees the following:
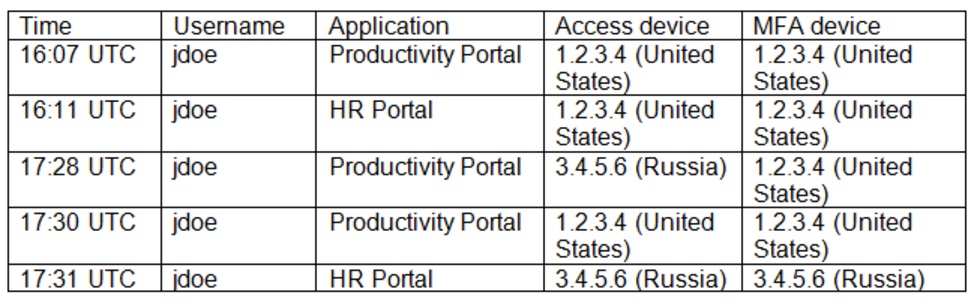
Which of the following are most likely occurring, base on the MFA logs? (Choose two.)
- A. Dictionary attack
- B. Push phishing
- C. Impossible geo-velocity
- D. Subscriber identity module swapping
- E. Rogue access point
- F. Password spray
A security analyst has identified a new malware file that has impacted the organization. The malware is polymorphic and has built-in conditional triggers that require a connection to the internet. The CPU has an idle process of at least 70%. Which of the following best describes how the security analyst can effectively review the malware without compromising the organization’s network?
- A. Utilize an RDP session on an unused workstation to evaluate the malware.
- B. Disconnect and utilize an existing infected asset off the network.
- C. Create a virtual host for testing on the security analyst workstation.
- D. Subscribe to an online service to create a sandbox environment.
Which of the following threat-modeling procedures is in the OWASP Web Security Testing Guide?
- A. Review of security requirements
- B. Compliance checks
- C. Decomposing the application
- D. Security by design
