
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
Chief Information Security Officer (CISO) wants to disable a functionality on a business-critical web application that is vulnerable to RCE in order to maintain the minimum risk level with minimal increased cost. Which of the following risk treatments best describes what the CISO is looking for?
- A. Transfer
- B. Mitigate
- C. Accept
- D. Avoid
An organization wants to implement a privileged access management solution to better manage the use of emergency and privileged service accounts. Which of the following would BEST satisfy the organization’s goal?
- A. Access control lists
- B. Discretionary access controls
- C. Policy-based access controls
- D. Credential vaulting
An analyst discovers unusual outbound connections to an IP that was previously blocked at the web proxy and firewall. Upon further investigation, it appears that the proxy and firewall rules that were in place were removed by a service account that is not recognized. Which of the following parts of the Cyber Kill Chain does this describe?
- A. Delivery
- B. Command and control
- C. Reconnaissance
- D. Weaponization
An organization’s email account was compromised by a bad actor. Given the following information:
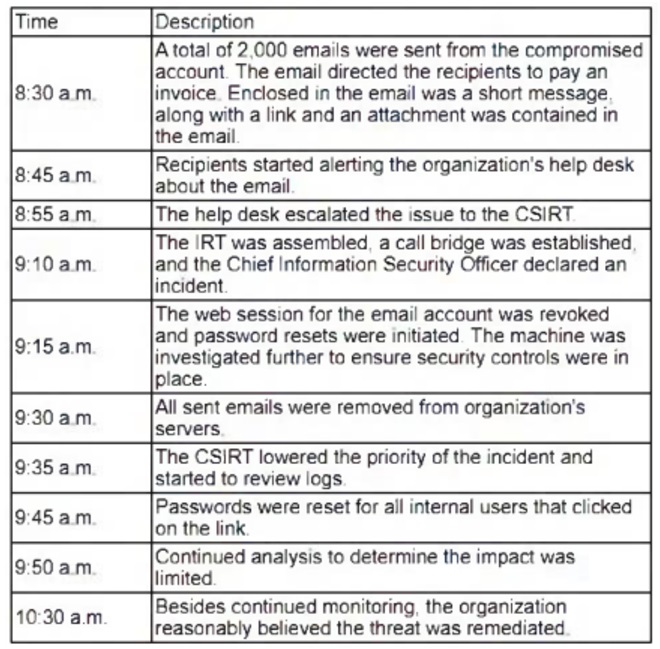
Which of the following is the length of time the team took to detect the threat?
- A. 25 minutes
- B. 40 minutes
- C. 45 minutes
- D. 2 hours
Which of the following BEST explains the function of a managerial control?
- A. To scope the security planning, program development, and maintenance of the security life cycle
- B. To guide the development of training, education, security awareness programs, and system maintenance
- C. To implement data classification, risk assessments, security control reviews, and contingency planning
- D. To ensure tactical design, selection of technology to protect data, logical access reviews, and the implementation of audit trails
Which of the following provides an automated approach to checking a system configuration?
- A. SCAP
- B. CI/CD
- C. OVAL
- D. Scripting
- E. SOAR
HOTSPOT
–
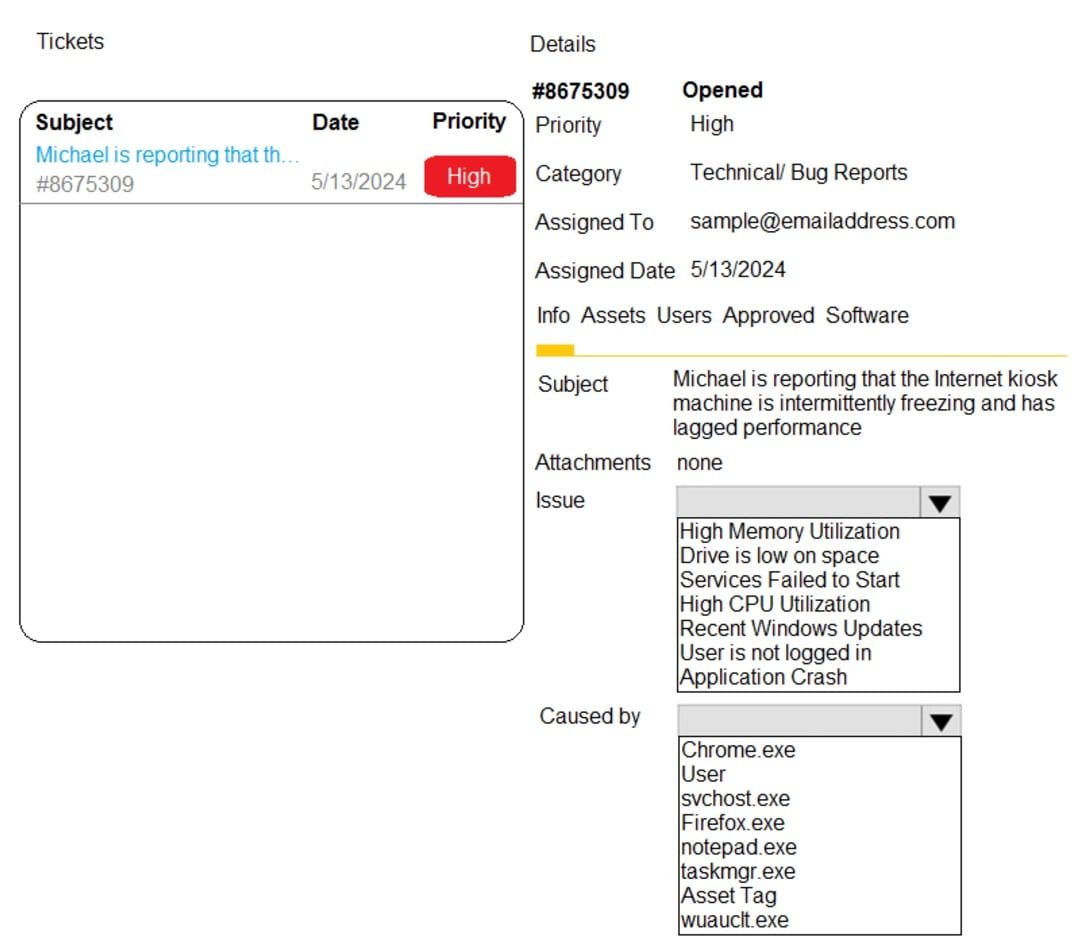
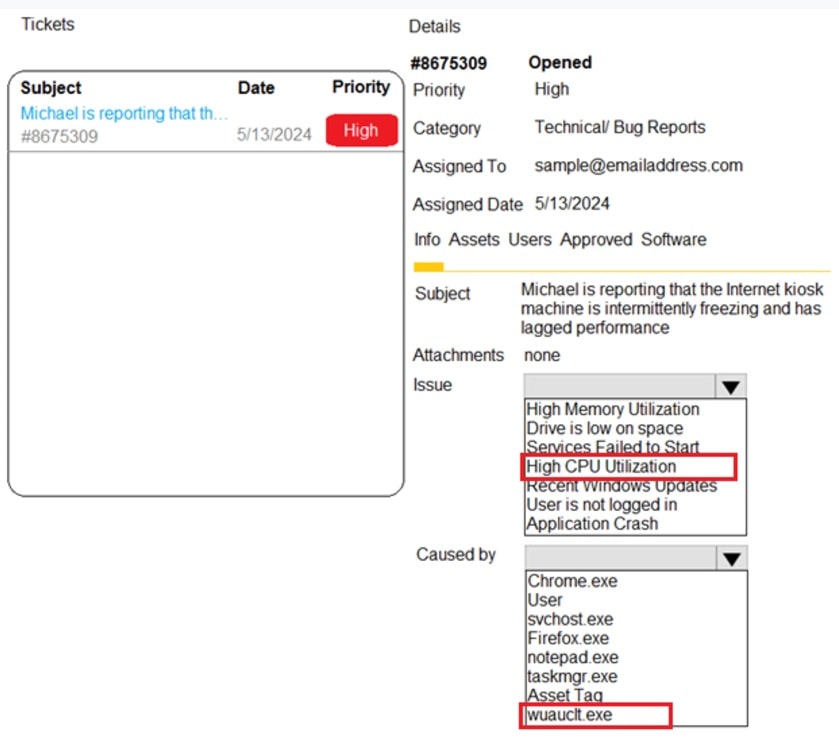
Welcome to the Enterprise Help Desk System. Please work the ticket escalated to you in the help desk ticket queue.
INSTRUCTIONS
–
Click on the ticket to see the ticket details. Additional content is available on tabs within the ticket.
First, select the appropriate issue from the drop-down menu. Then, select the MOST likely root cause from second drop-down menu.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
SIMULATION
–
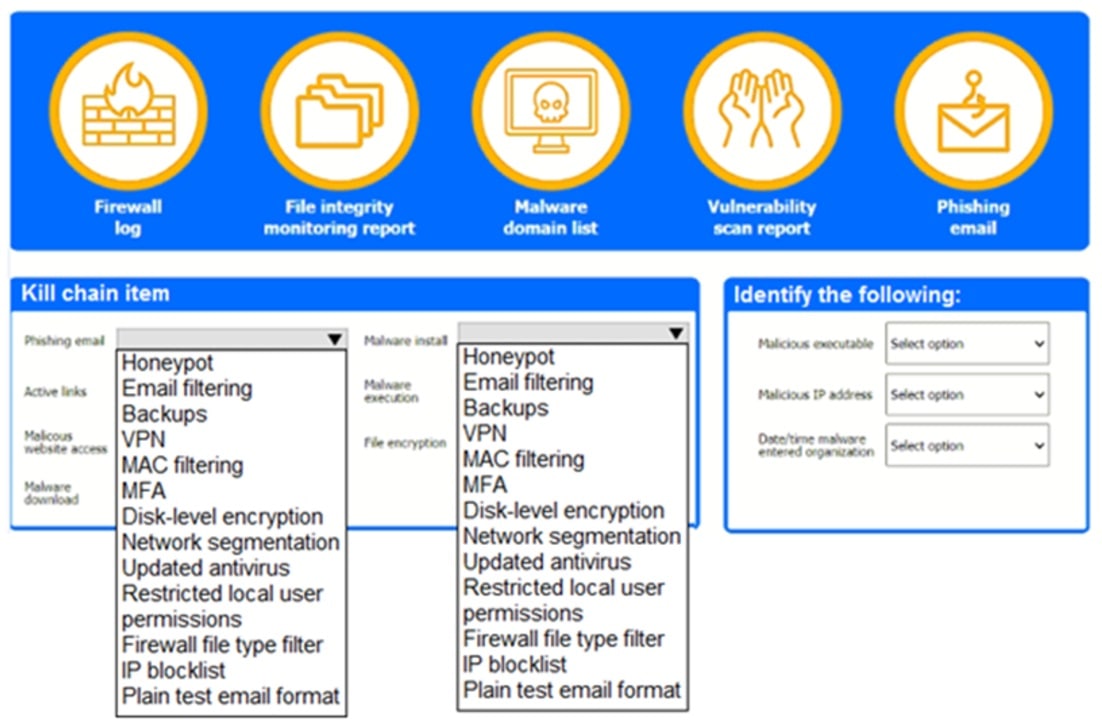
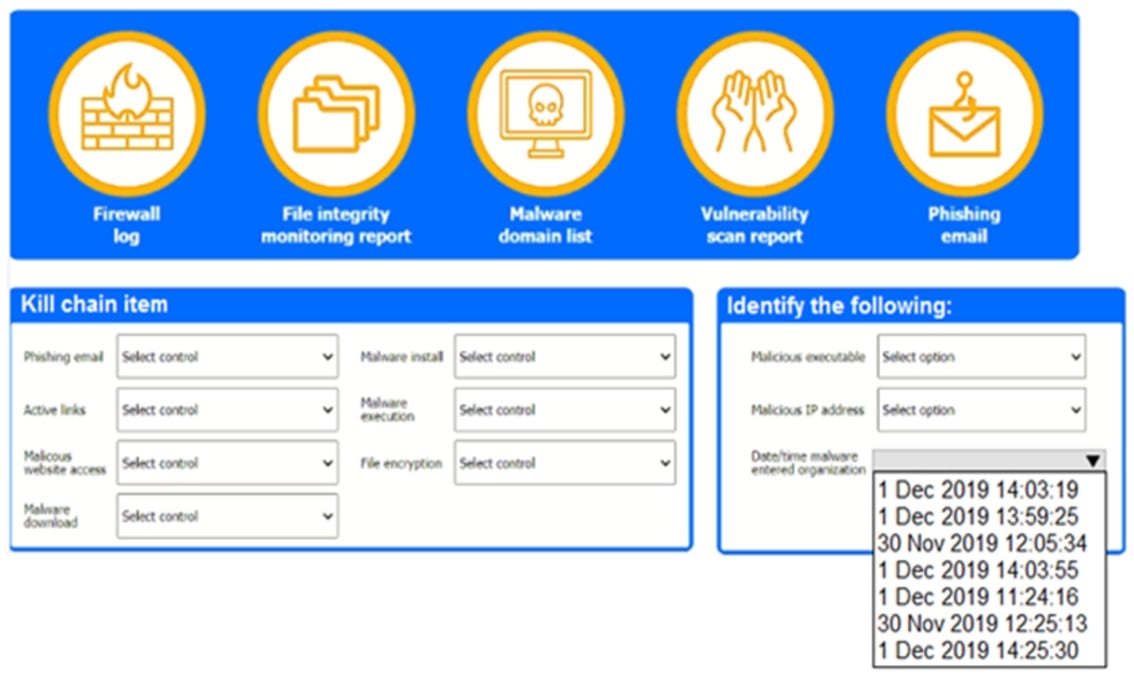
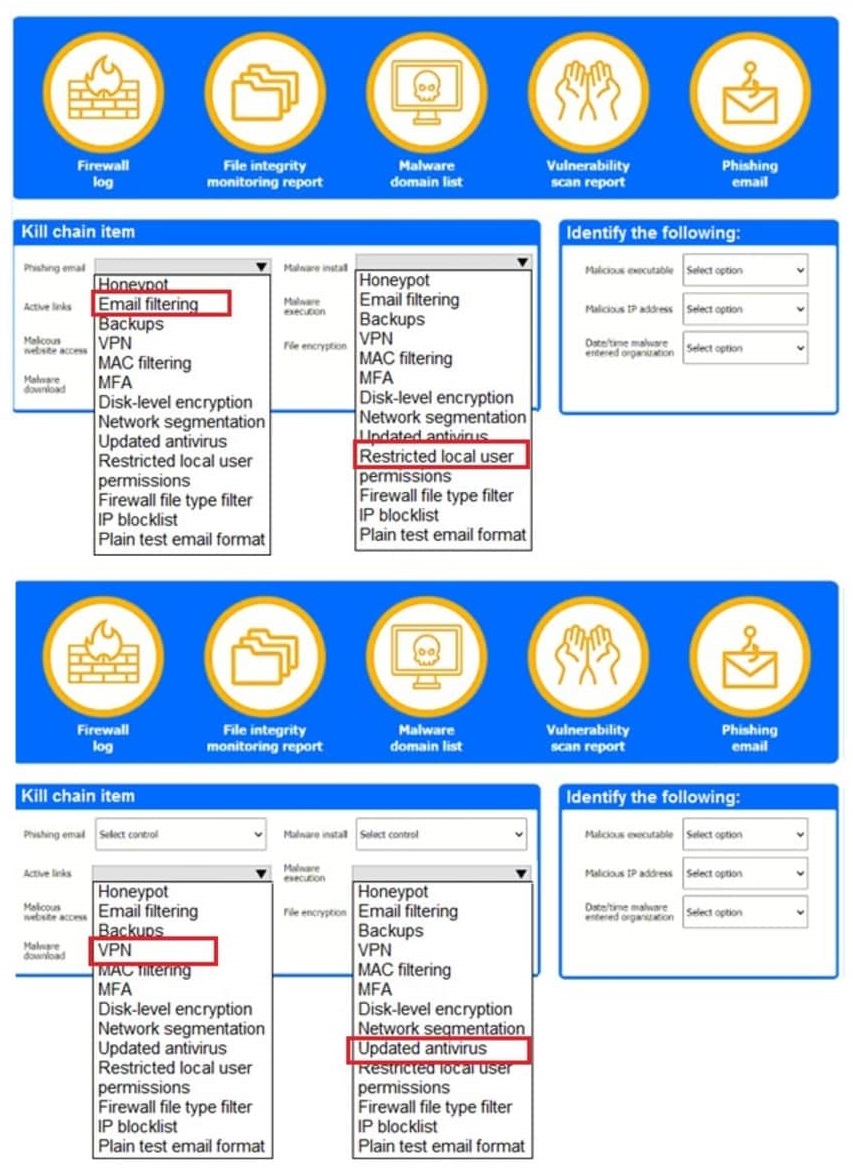
A company recently experienced a security incident. The security team has determined a user clicked on a link embedded in a phishing email that was sent to the entire company. The link resulted in a malware download, which was subsequently installed and run.
INSTRUCTIONS
–
Part 1
–
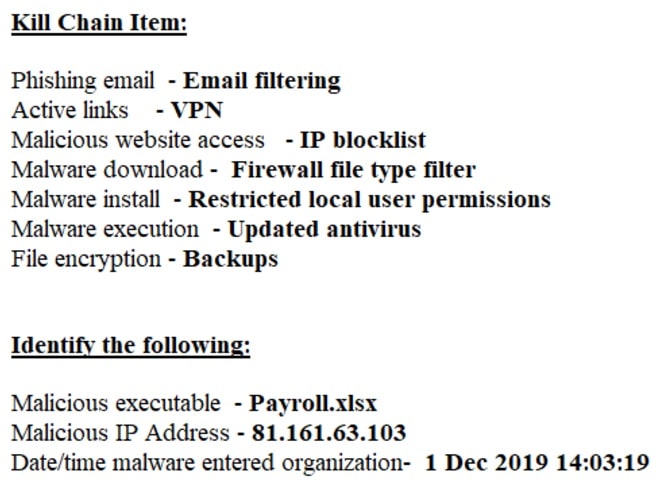
Review the artifacts associated with the security Incident. Identify the name of the malware, the malicious IP address, and the date and time when the malware executable entered the organization.
Part 2
–
Review the kill chain items and select an appropriate control for each that would improve the security posture of the organization and would have helped to prevent this incident from occurring. Each control may only be used once, and not all controls will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
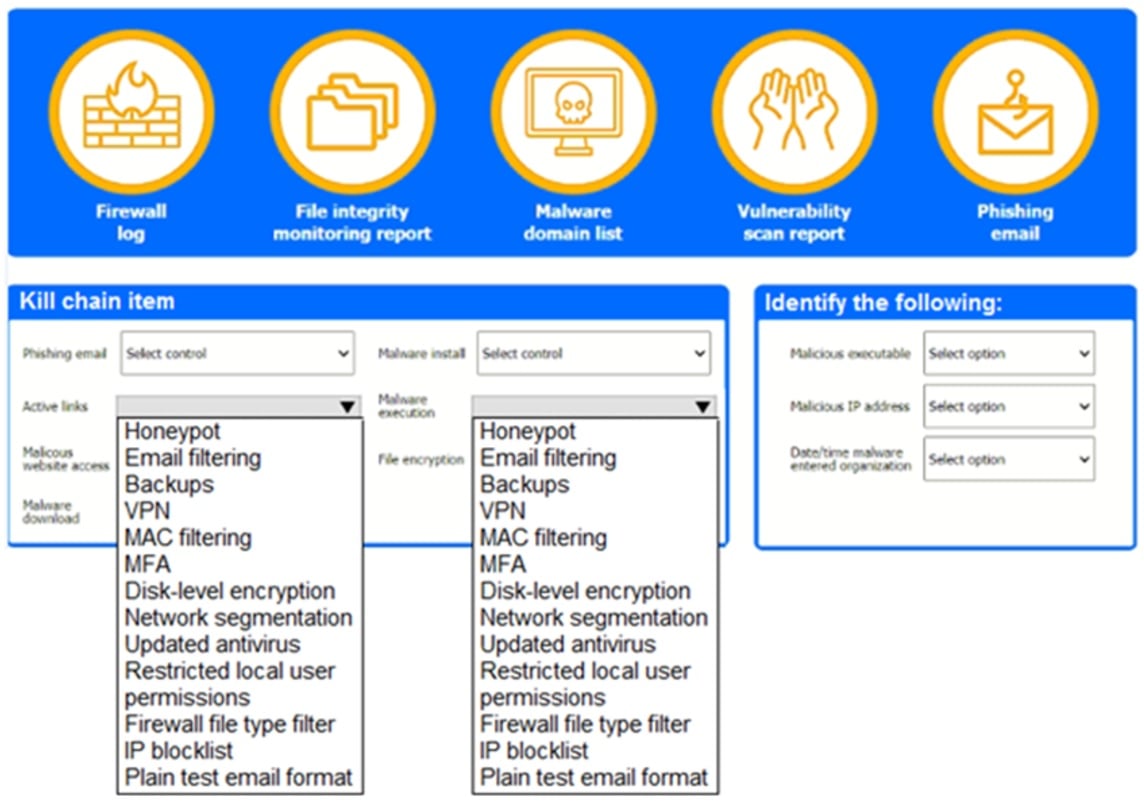
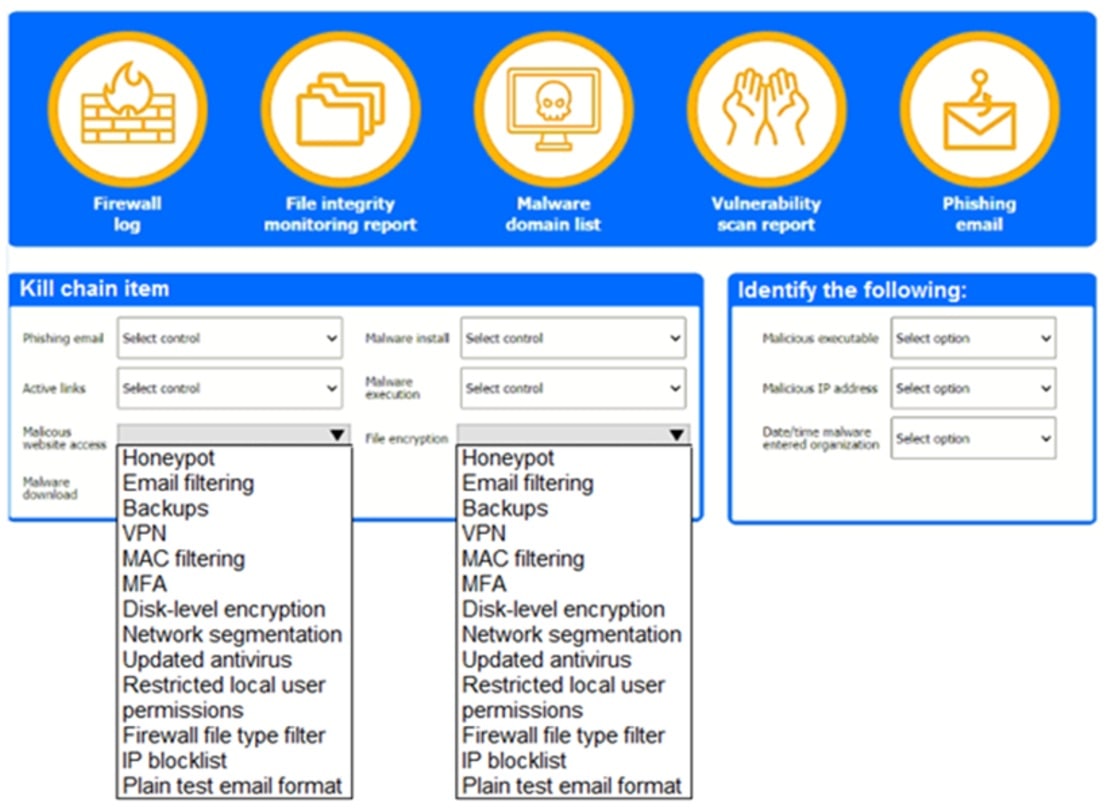
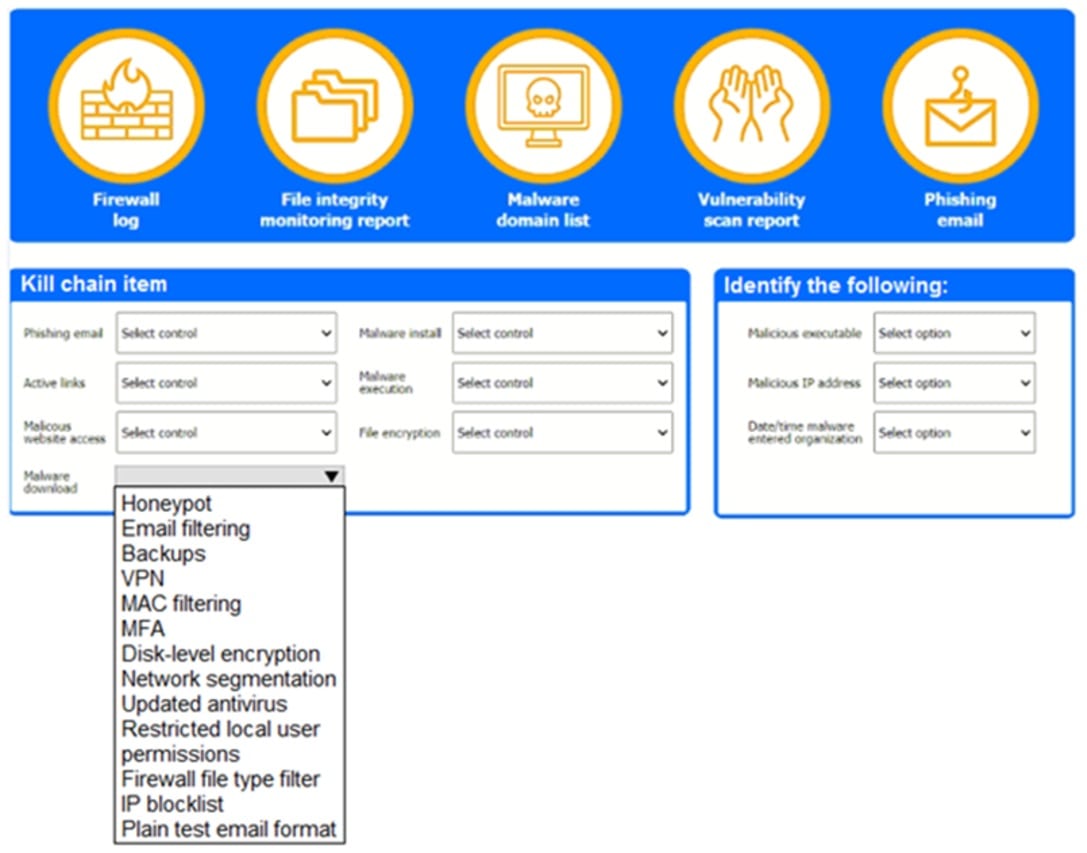
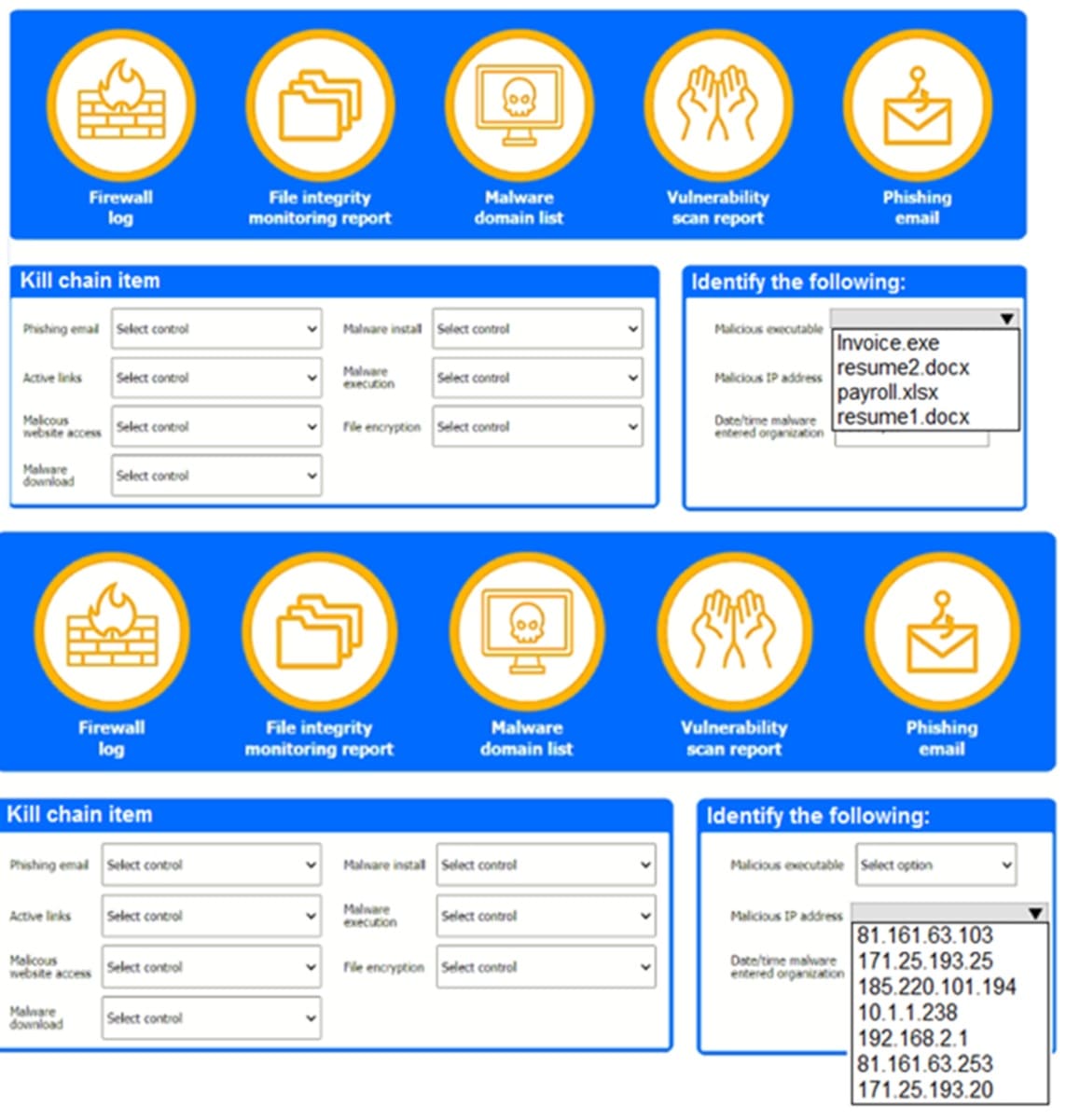
Answer:
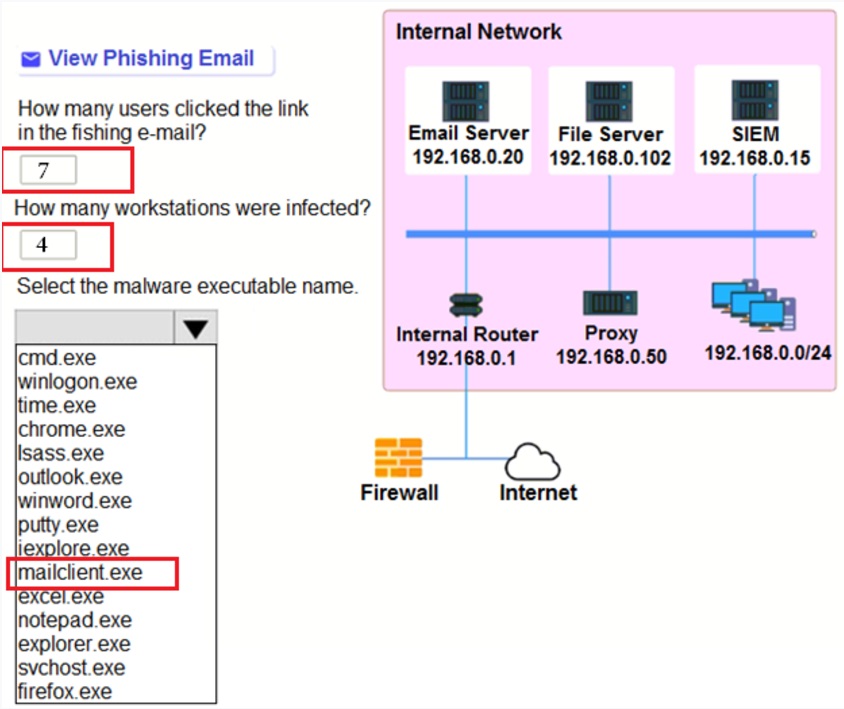
SIMULATION –
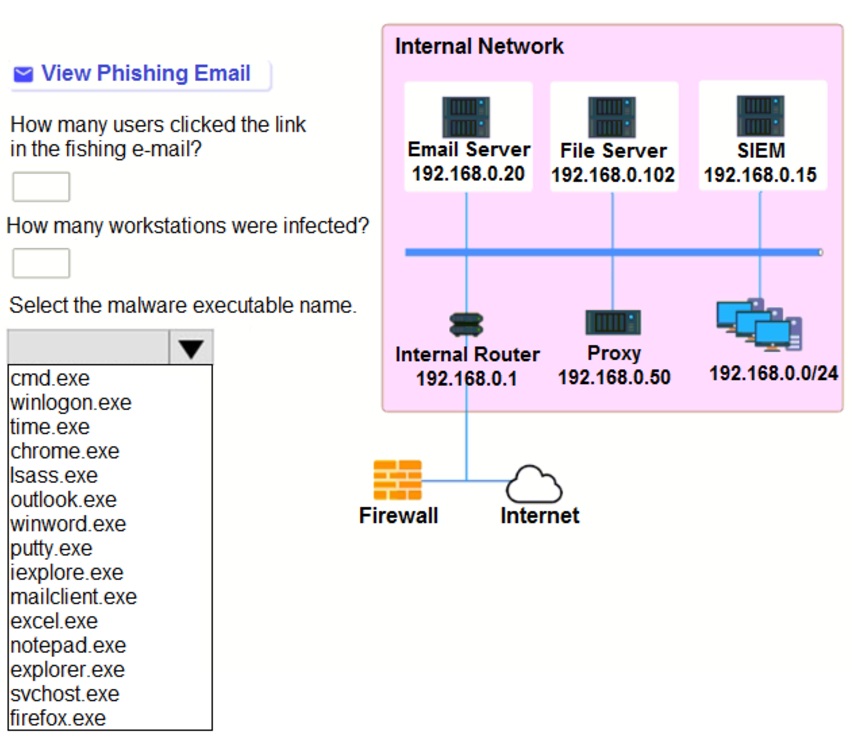
Approximately 100 employees at your company have received a phishing email. As a security analyst, you have been tasked with handling this situation.
INSTRUCTIONS –
Review the information provided and determine the following:
1. How many employees clicked on the link in the phishing email?
2. On how many workstations was the malware installed?
3. What is the executable file name of the malware?
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Answer:
An analyst reviews a recent government alert on new zero-day threats and finds the following CVE metrics for the most critical of the vulnerabilities:
CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H/E:U/RL:W/RC:R
Which of the following represents the exploit code maturity of this critical vulnerability?
- A. E:U
- B. S:C
- C. RC:R
- D. AV:N
- E. AC:L
