
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
Which of the following in the digital forensics process is considered a critical activity that often includes a graphical representation of process and operating system events?
- A. Registry editing
- B. Network mapping
- C. Timeline analysis
- D. Write blocking
Which of the following best describes the importance of KPIs in an incident response exercise?
- A. To identify the personal performance of each analyst
- B. To describe how incidents were resolved
- C. To reveal what the team needs to prioritize
- D. To expose which tools should be used
An organization is conducting a pilot deployment of an e-commerce application. The application’s source code is not available. Which of the following strategies should an analyst recommend to evaluate the security of the software?
- A. Static testing
- B. Vulnerability testing
- C. Dynamic testing
- D. Penetration testing
A security team needs to demonstrate how prepared the team is in the event of a cyberattack. Which of the following would best demonstrate a real-world incident without impacting operations?
- A. Review lessons-learned documentation and create a playbook.
- B. Gather all internal incident response party members and perform a simulation.
- C. Deploy known malware and document the remediation process.
- D. Schedule a system recovery to the DR site for a few applications.
A SOC receives several alerts indicating user accounts are connecting to the company’s identity provider through non-secure communications. User credentials for accessing sensitive, business-critical systems could be exposed. Which of the following logs should the SOC use when determining malicious intent?
- A. DNS
- B. tcpdump
- C. Directory
- D. IDS
A vulnerability scan of a web server that is exposed to the internet was recently completed. A security analyst is reviewing the resulting vector strings:
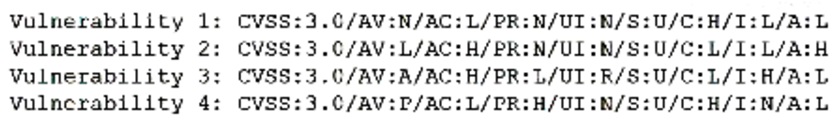
Which of the following vulnerabilities should be patched first?
- A. Vulnerability 1
- B. Vulnerability 2
- C. Vulnerability 3
- D. Vulnerability 4
Each time a vulnerability assessment team shares the regular report with other teams, inconsistencies regarding versions and patches in the existing infrastructure are discovered. Which of the following is the best solution to decrease the inconsistencies?
- A. Implementing credentialed scanning
- B. Changing from a passive to an active scanning approach
- C. Implementing a central place to manage IT assets
- D. Performing agentless scanning
An organization plans to use an advanced machine-learning tool as a central collection server. The tool will perform data aggregation and analysis. Which of the following should the organization implement?
- A. SIEM
- B. Firewalls
- C. Syslog server
- D. Flow analysis
A vulnerability analyst is writing a report documenting the newest, most critical vulnerabilities identified in the past month. Which of the following public MITRE repositories would be best to review?
- A. Cyber Threat Intelligence
- B. Common Vulnerabilities and Exposures
- C. Cyber Analytics Repository
- D. ATT&CK
A corporation wants to implement an agent-based endpoint solution to help:
• Flag various threats
• Review vulnerability feeds
• Aggregate data
• Provide real-time metrics by using scripting languages
Which of the following tools should the corporation implement to reach this goal?
- A. DLP
- B. Heuristics
- C. SOAR
- D. NAC
