
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst at a technology solutions firm has uncovered the same vulnerabilities on a vulnerability scan for a long period of time. The vulnerabilities are on systems that are dedicated to the firm’s largest client. Which of the following is MOST likely inhibiting the remediation efforts?
- A. The parties have an MOU between them that could prevent shutting down the systems
- B. There is a potential disruption of the vendor-client relationship
- C. Patches for the vulnerabilities have not been fully tested by the software vendor
- D. There is an SLA with the client that allows very little downtime
Which of the following will most likely cause severe issues with authentication and logging?
- A. Virtualization
- B. Multifactor authentication
- C. Federation
- D. Time synchronization
Several critical bugs were identified during a vulnerability scan. The SLA risk requirement is that all critical vulnerabilities should be patched within 24 hours. After sending a notification to the asset owners, the patch cannot be deployed due to planned, routine system upgrades. Which of the following is the best method to remediate the bugs?
- A. Reschedule the upgrade and deploy the patch.
- B. Request an exception to exclude the patch from installation.
- C. Update the risk register and request a change to the SLA.
- D. Notify the incident response team and rerun the vulnerability scan.
A systems administrator believes a user’s workstation has been compromised. The workstation’s performance has been lagging significantly for the past several hours. The administrator runs the task list /v command and receives the following output:
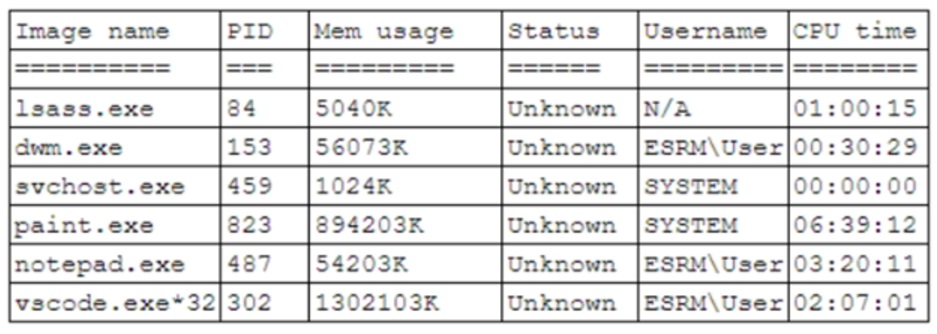
Which of the following should a security analyst recognize as an indicator of compromise?
- A. dwm.exe being executed under the user context
- B. The high memory usage of vscode.exe*32
- C. The abnormal behavior of paint.exe
- D. svchost.exe being executed as SYSTEM
Which of the following BEST describes HSM?
- A. A computing device that manages cryptography, decrypts traffic, and maintains library calls
- B. A computing device that manages digital keys, performs encryption/decryption functions, and maintains other cryptographic functions
- C. A computing device that manages physical keys, encrypts devices, and creates strong cryptographic functions
- D. A computing device that manages algorithms, performs entropy functions, and maintains digital signatures
A Chief Information Security Officer wants to lock down the users’ ability to change applications that are installed on their Windows systems. Which of the following is the best enterprise-level solution?
- A. HIPS
- B. GPO
- C. Registry
- D. DLP
An employee received a phishing email that contained malware targeting the company. Which of the following is the best way for a security analyst to get more details about the malware and avoid disclosing information?
- A. Upload the malware to the VirusTotal website.
- B. Share the malware with the EDR provider.
- C. Hire an external consultant to perform the analysis.
- D. Use a local sandbox in a microsegmented environment.
A Chief Finance Officer receives an email from someone who is possibly impersonating the company’s Chief Executive Officer and requesting a financial operation. Which of the following should an analyst use to verify whether the email is an impersonation attempt?
- A. PKI
- B. MFA
- C. SMTP
- D. DKIM
A developer wrote a script to make names and other PII data unidentifiable before loading a database export into the testing system. Which of the following describes the type of control that is being used?
- A. Data encoding
- B. Data masking
- C. Data loss prevention
- D. Data classification
A security analyst is investigating a compromised Linux server. The analyst issues the ps command and receives the following output:
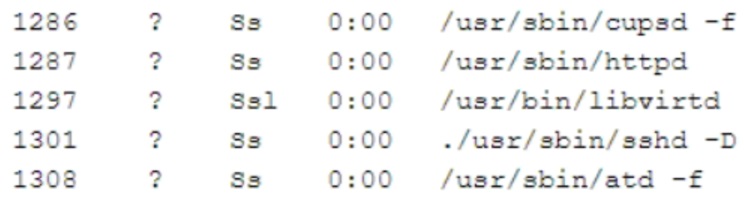
Which of the following commands should the administrator run NEXT to further analyze the compromised system?
- A. strace /proc/1301
- B. rpm -V openssh-server
- C. /bin/ls -1 /proc/1301/exe
- D. kill -9 1301
