
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
When undertaking a cloud migration of multiple SaaS applications, an organization’s systems administrators struggled with the complexity of extending identity and access management to cloud-based assets. Which of the following service models would have reduced the complexity of this project?
- A. OpenID
- B. SASE
- C. ZTNA
- D. SWG
A security analyst is conducting traffic analysis following a potential web server breach. The analyst wants to investigate client-side server errors.
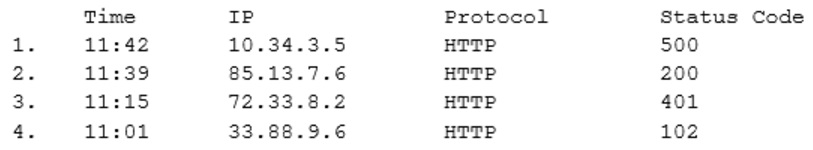
Which of the following lines of this query output should be investigated further?
- A. 1
- B. 2
- C. 3
- D. 4
Which of the following explains the importance of a timeline when providing an incident response report?
- A. The timeline contains a real-time record of an incident and provides information that helps to simplify a postmortem analysis.
- B. An incident timeline provides the necessary information to understand the actions taken to mitigate the threat or risk.
- C. The timeline provides all the information, in the form of a timetable, of the whole incident response process including actions taken.
- D. An incident timeline presents the list of commands executed by an attacker when the system was compromised, in the form of a timetable.
An email analysis system notifies a security analyst that the following message was quarantined and requires further review.
From: CEO@CompTIA.org<ceo_comptia@externalmail.com>
To: Purchasing@CompTIA.org<purchasing@comptia.org>
Subject: [EXTERNAL] Gift card purchase ASAP
Body:
Please purchase gift cards to any major electronics store and reply with pictures of them to this email!
Which of the following actions should the security analyst take?</purchasing@comptia.org></ceo_comptia@externalmail.com>
- A. Release the email for delivery due to its importance.
- B. Immediately contact a purchasing agent to expedite.
- C. Delete the email and block the sender.
- D. Purchase the gift cards and submit an expense report
A security analyst is conducting a post-incident log analysis to determine which indicators can be used to detect further occurrences of a data exfiltration incident. The analyst determines backups were not performed during this time and reviews the following:
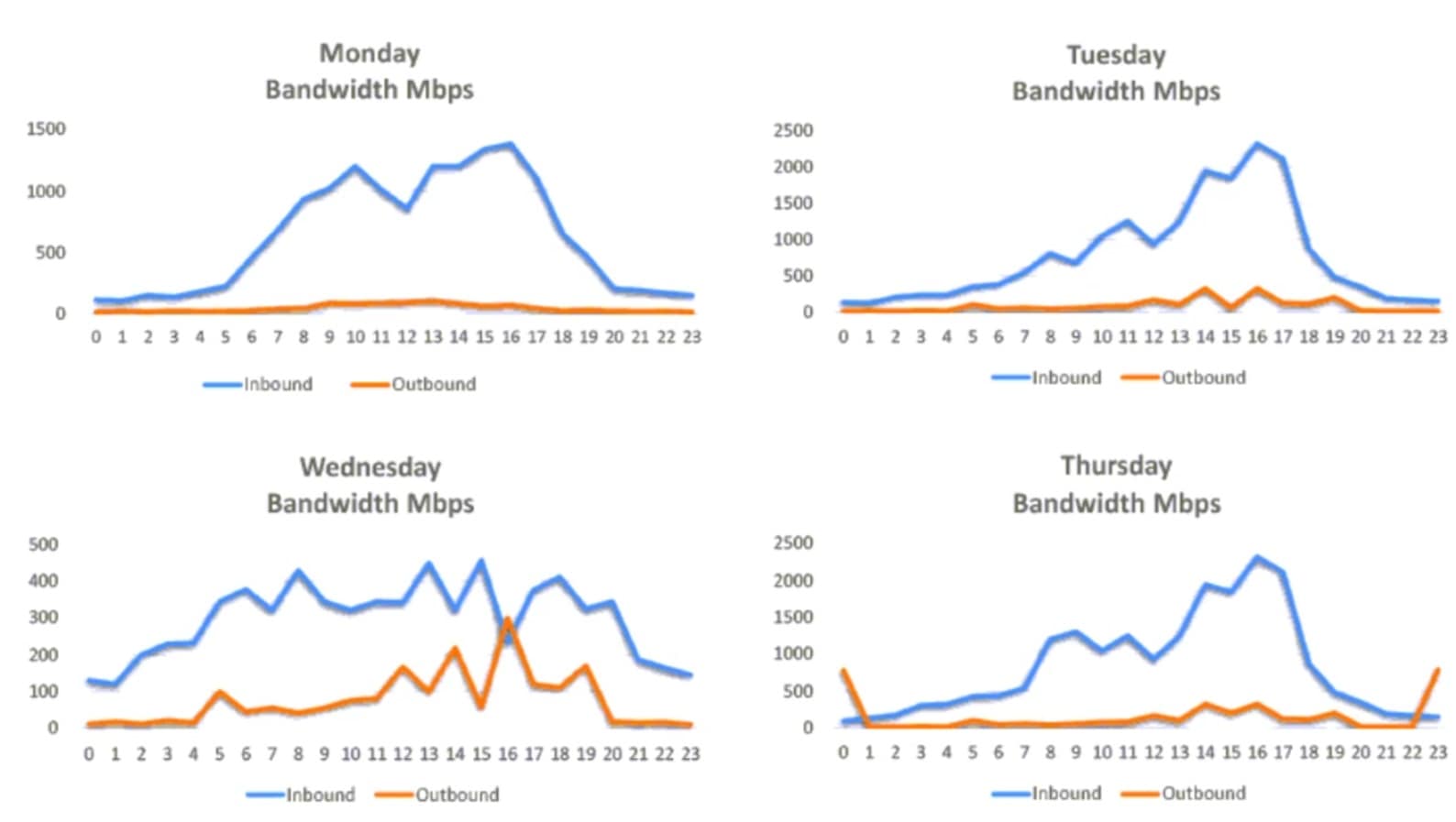
Which of the following should the analyst review to find out how the data was exfiltrated?
- A. Monday’s logs
- B. Tuesday’s logs
- C. Wednesday’s logs
- D. Thursday’s logs
HOTSPOT
–
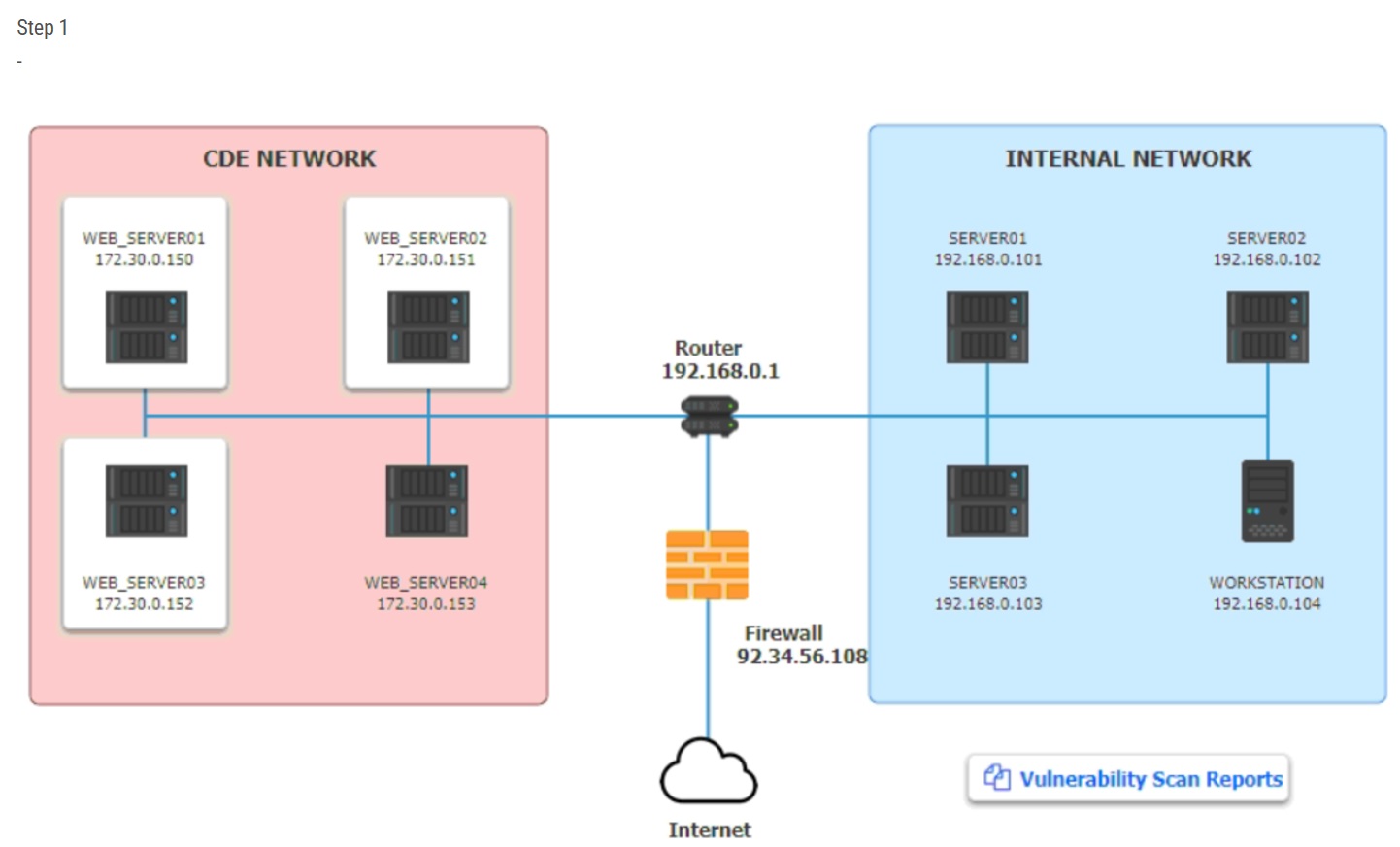
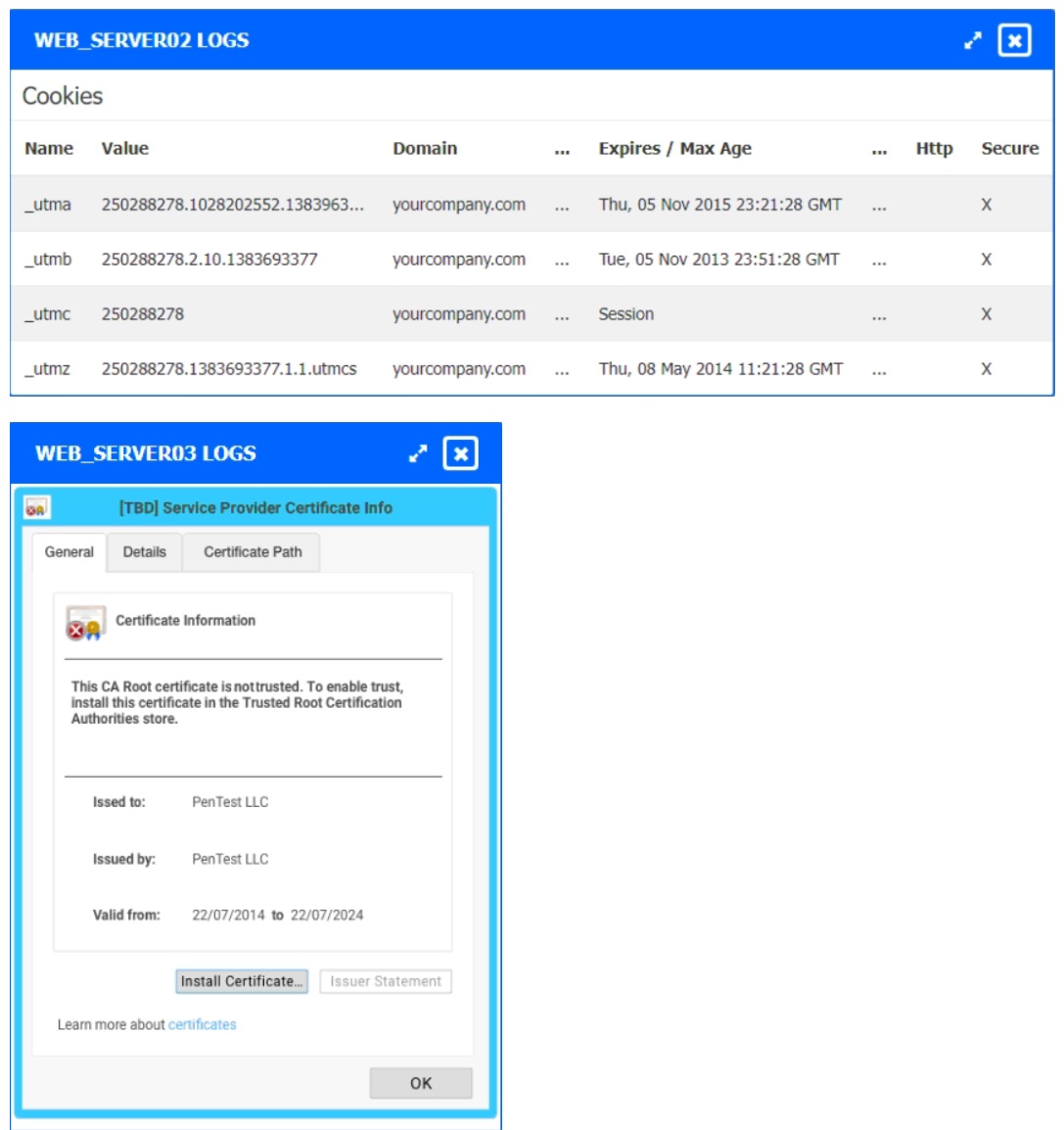
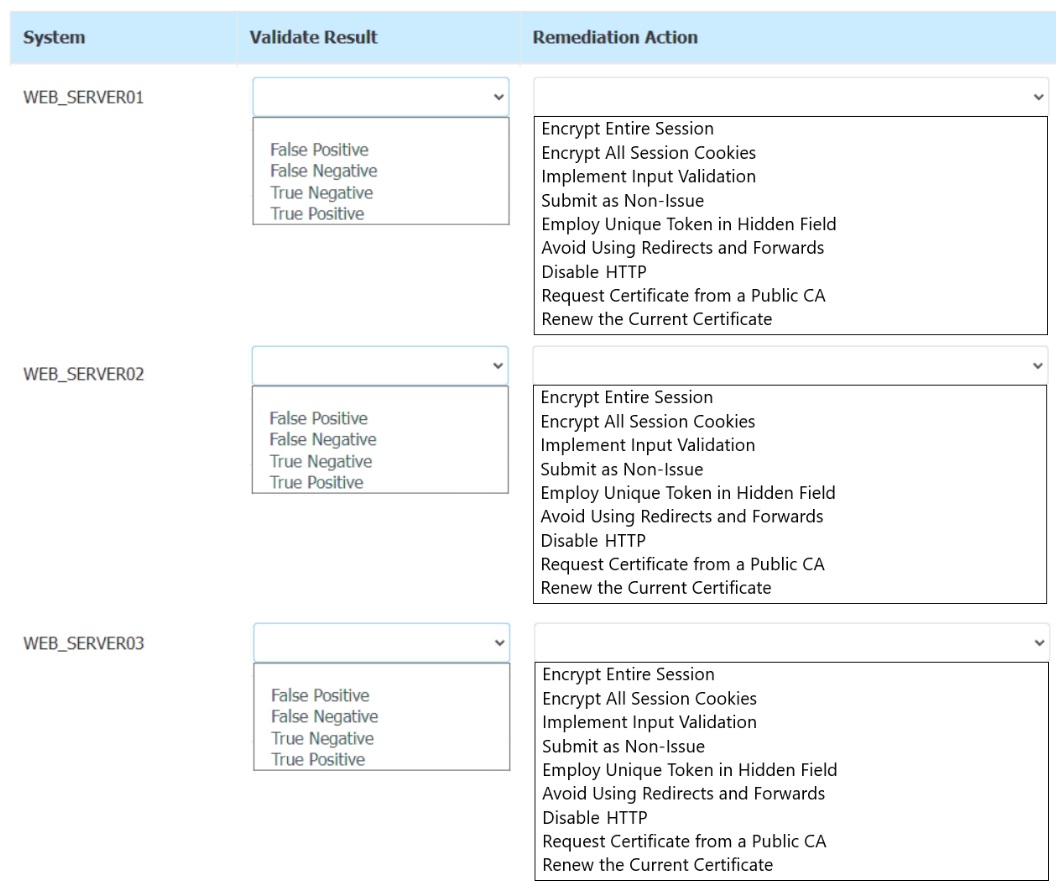
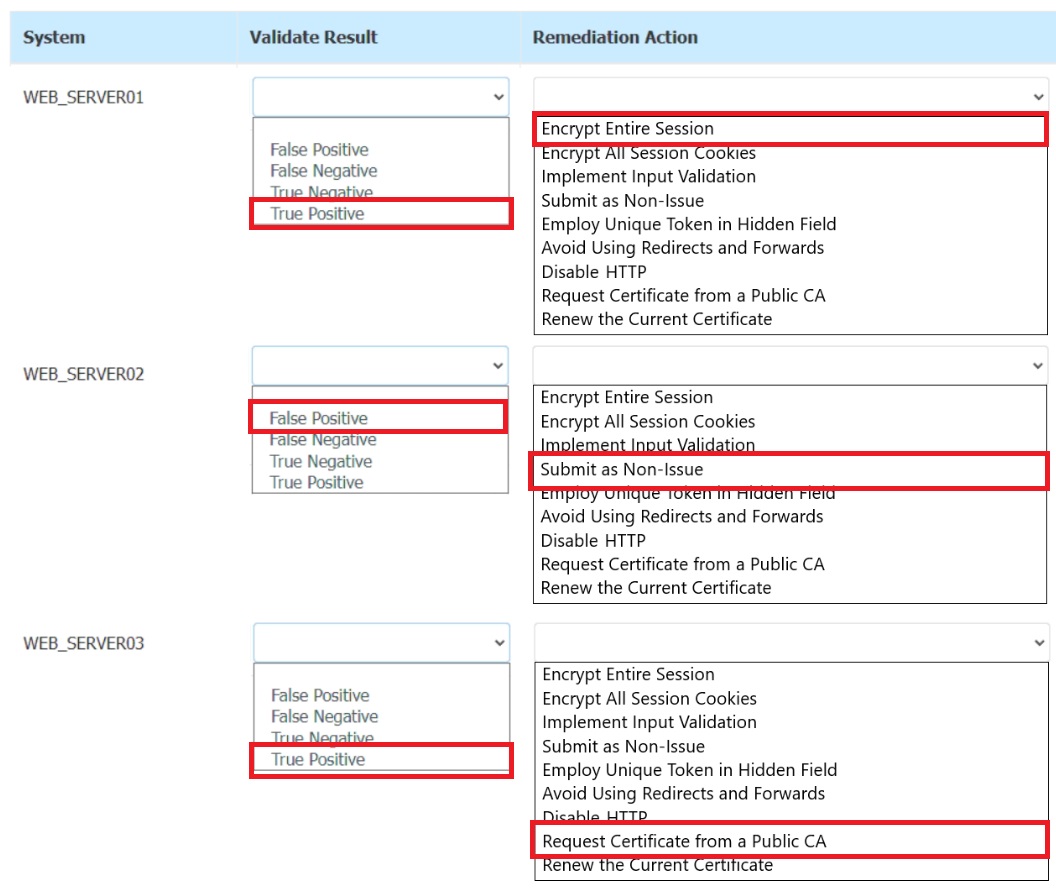
The developers recently deployed new code to three web servers. A daily automated external device scan report shows server vulnerabilities that are failing items according to PCI DSS.
If the vulnerability is not valid, the analyst must take the proper steps to get the scan clean.
If the vulnerability is valid, the analyst must remediate the finding.
After reviewing the information provided in the network diagram, select the STEP 2 tab
to complete the simulation by selecting the correct Validation Result and Remediation
Action for each server listed using the drop-down options.
INSTRUCTIONS
–
STEP 1: Review the information provided in the network diagram.
STEP 2: Given the scenario, determine which remediation action is required to address the
vulnerability.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Step 1
–
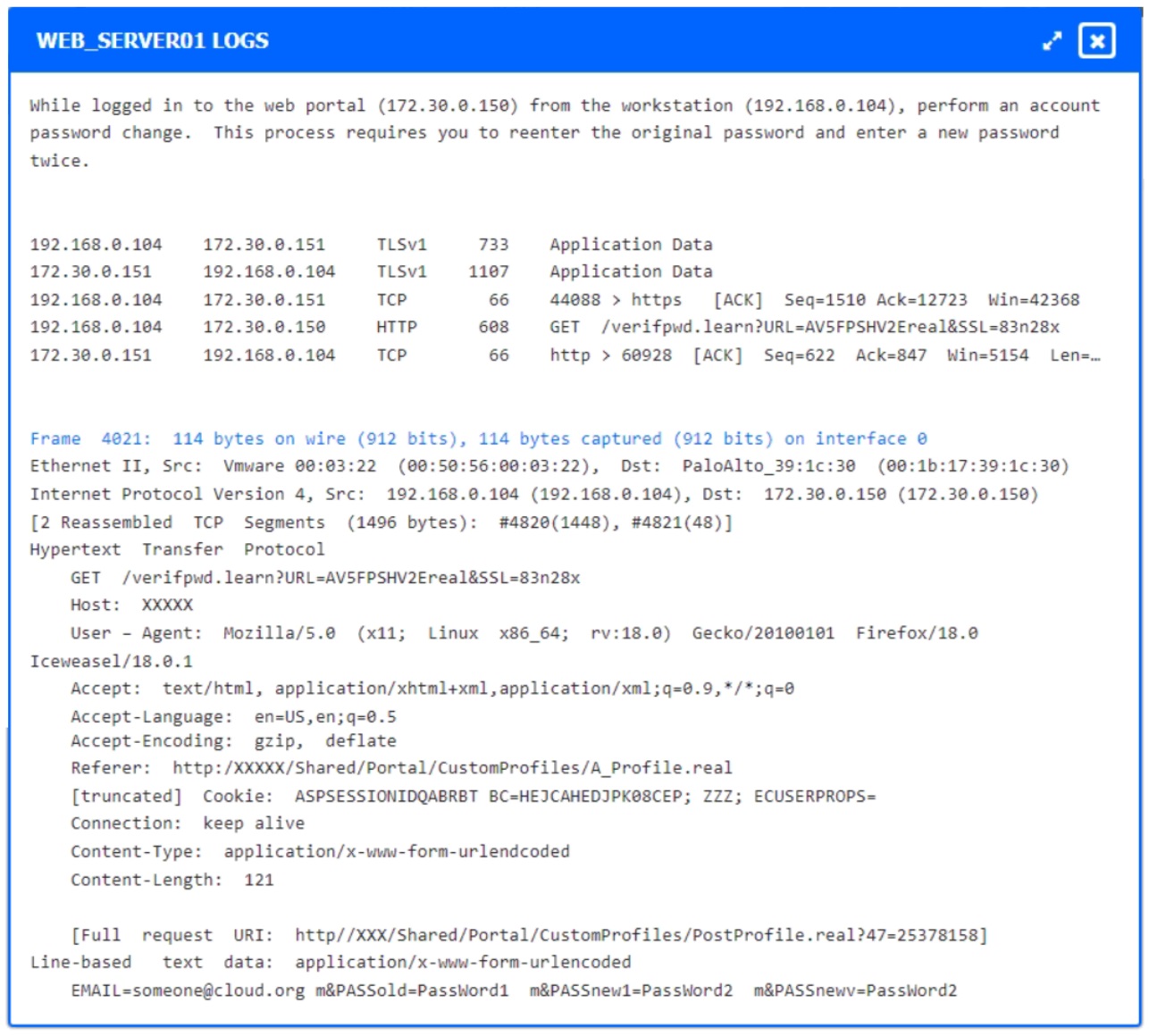
Step 2:
Answer:
Which of the following characteristics ensures the security of an automated information system is the most effective and economical?
- A. Originally designed to provide necessary security
- B. Subjected to intense security testing
- C. Customized to meet specific security threats
- D. Optimized prior to the addition of security
A network attack that is exploiting a vulnerability in the SNMP is detected. Which of the following should the cybersecurity analyst do FIRST?
- A. Apply the required patches to remediate the vulnerability
- B. Escalate the incident to the senior management team for guidance
- C. Disable all privileged user accounts on the network
- D. Temporarily block the attacking IP address
An analyst is reviewing the following output as part of an incident:
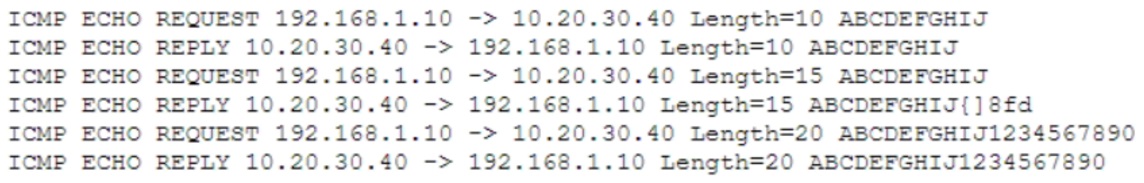
Which of the following is MOST likely happening?
- A. The hosts are part of a reflective denial-of-service attack
- B. Information is leaking from the memory of host 10.20.30.40
- C. Sensitive data is being exfiltrated by host 192.168.1.10
- D. Host 192.168.1.10 is performing firewall port knocking
Which of the following attributes is part of the Diamond Model of Intrusion Analysis?
- A. Delivery
- B. Weaponization
- C. Command and control
- D. Capability
