
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
SIMULATION
–
An organization’s website was maliciously altered.
INSTRUCTIONS
–
Review information in each tab to select the source IP the analyst should be concerned about, the indicator of compromise, and the two appropriate corrective actions.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
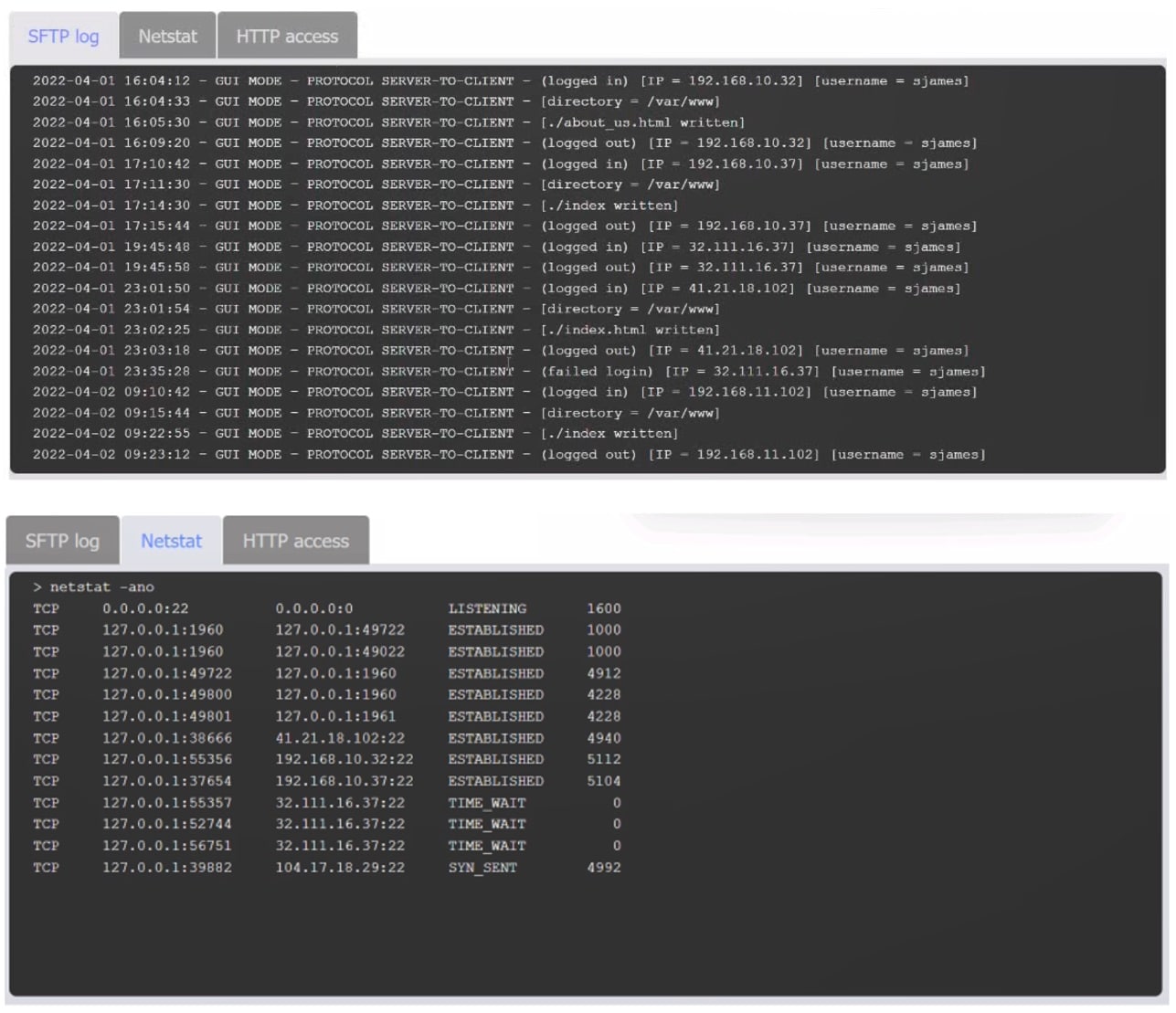
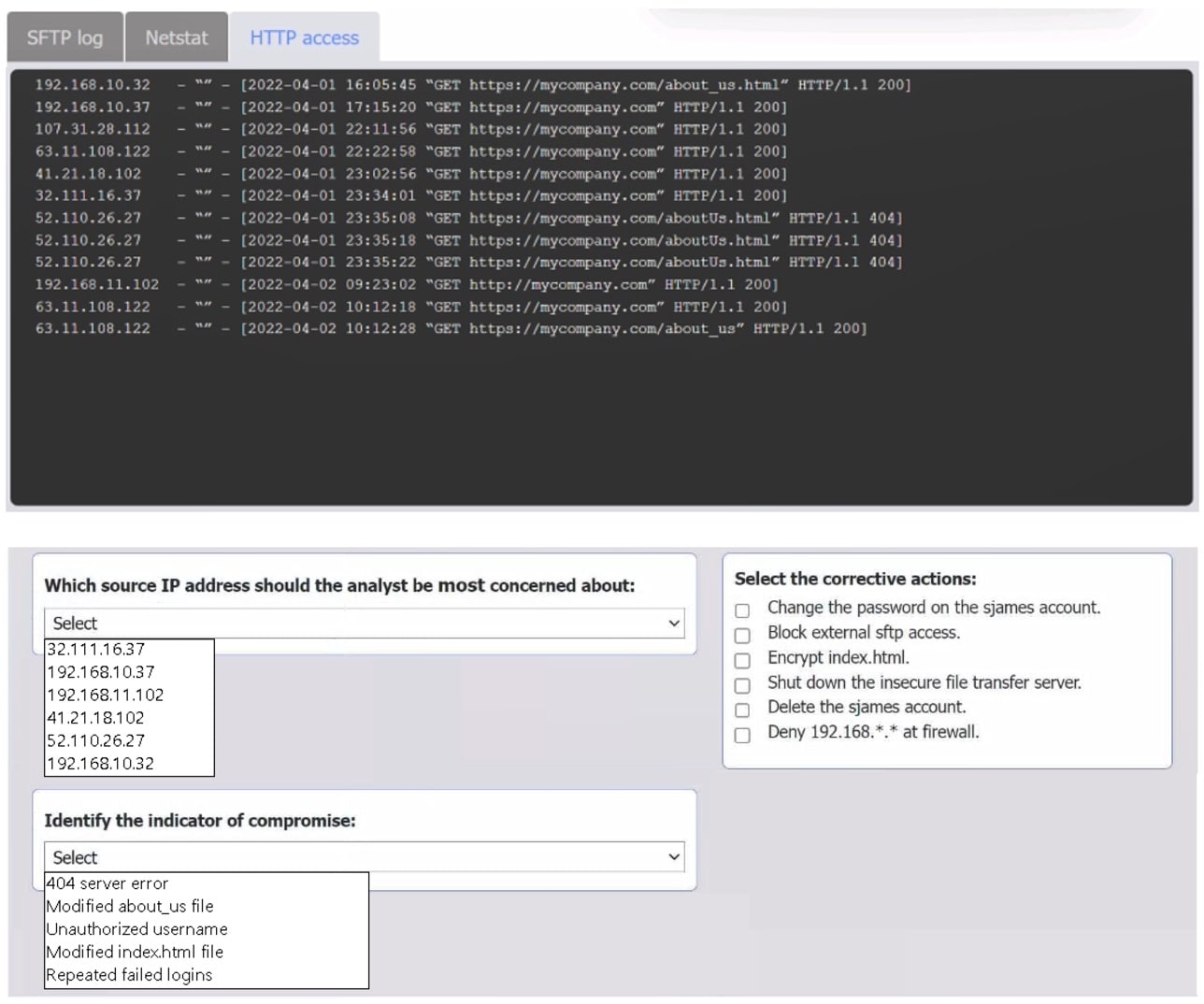
Answer:

SIMULATION
–
An organization has noticed large amounts of data are being sent out of its network. An analyst is identifying the cause of the data exfiltration.
INSTRUCTIONS
–
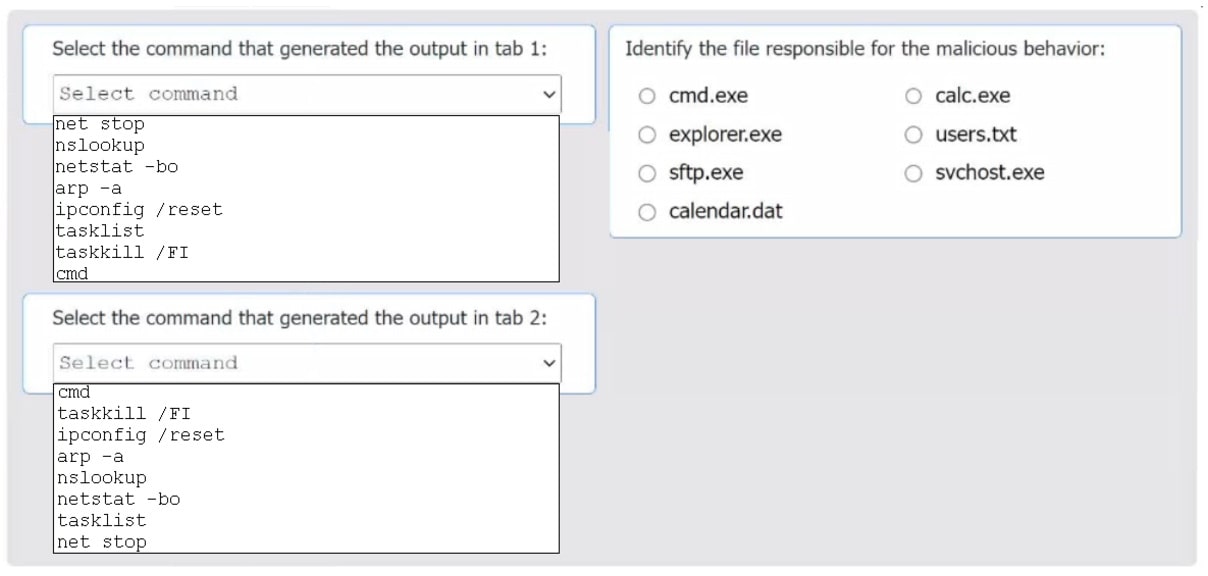
Select the command that generated the output in tabs 1 and 2.
Review the output text in all tabs and identify the file responsible for the malicious behavior.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
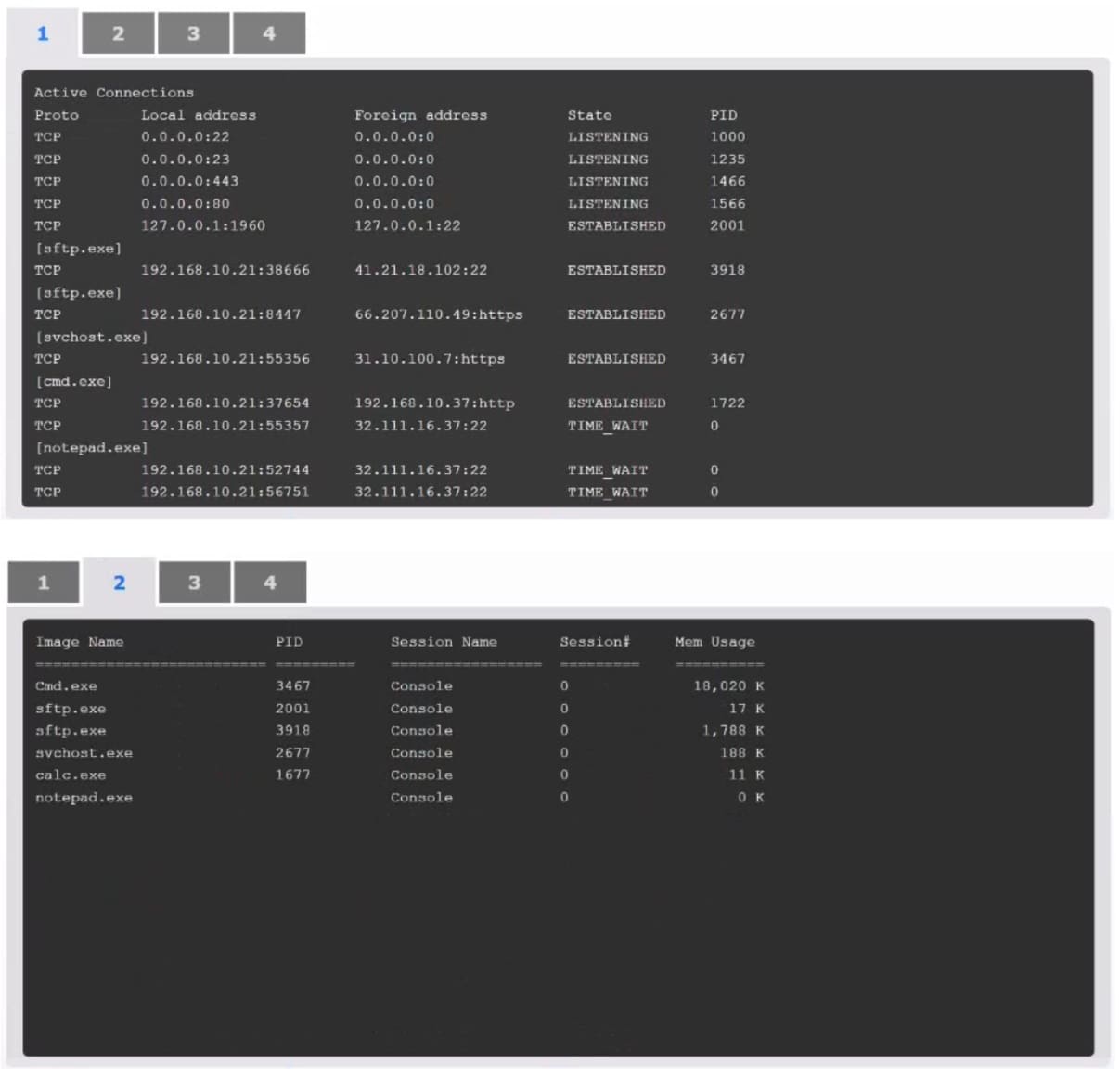
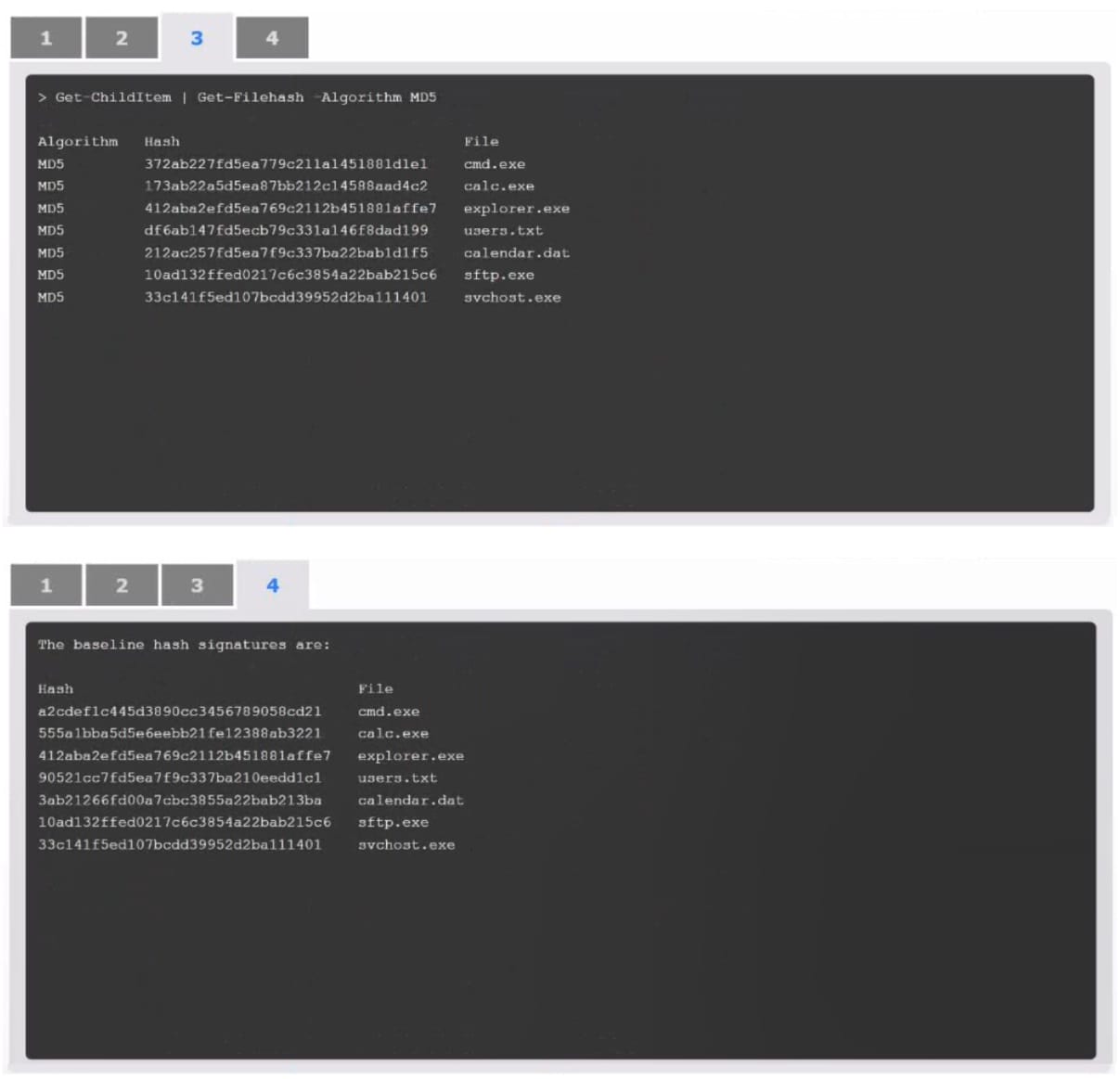
Answer:
An analyst is creating the final vulnerability report for one of the company’s customers. The customer asks for a scanning profile with a CVSS score of 7 or higher. The analyst has confirmed there is no finding for missing database patches, even if false positives have been eliminated by manual checks. Which of the following is the most probable reason for the missing scan result?
- A. The server was offline at the moment of the scan.
- B. The system was not patched appropriately before the scan.
- C. The scan finding does not match the requirement.
- D. The output of the scan is corrupted.
A security analyst found the following entry in a server log:

The analyst executed netstat and received the following output:
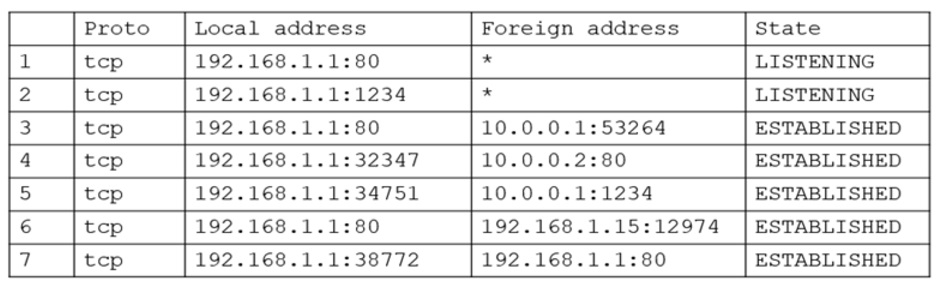
Which of the following lines in the output confirms this was successfully executed by the server?
- A. 1
- B. 2
- C. 3
- D. 4
- E. 5
- F. 6
- G. 7
Which of the following weaknesses associated with common SCADA systems are the MOST critical for organizations to address architecturally within their networks? (Choose two.)
- A. Boot processes that are neither measured nor attested
- B. Legacy and unpatchable systems software
- C. Unnecessary open ports and protocols
- D. No OS kernel mandatory access controls
- E. Unauthenticated commands
- F. Insecure filesystem permissions
An analyst receives alerts that state the following traffic was identified on the perimeter network firewall:
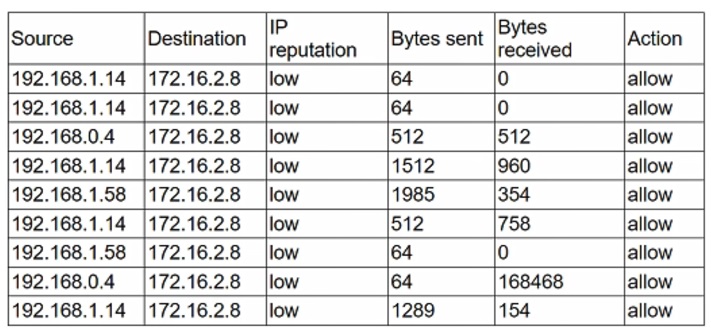
Which of the following best describes the indicator of compromise that triggered the alerts?
- A. Anomalous activity
- B. Bandwidth saturation
- C. Cryptomining
- D. Denial of service
A newly hired security manager in a SOC wants to improve efficiency by automating routine tasks. Which of the following SOC tasks is most suitable for automation?
- A. Conducting security assessments and audits of IT systems
- B. Investigating security incidents and determining the root causes
- C. Reviewing logs and alerts to identify security threats and anomalies
- D. Generating incident reports and notifying the appropriate stakeholders
During an investigation, an analyst discovers the following rule in an executive’s email client:
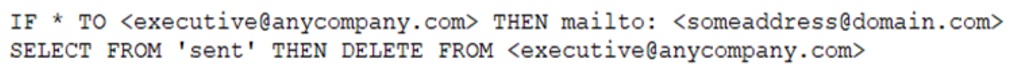
The executive is not aware of this rule. Which of the following should the analyst do first to evaluate the potential impact of this security incident?
- A. Check the server logs to evaluate which emails were sent to <someaddress@domain.com>.</someaddress@domain.com>
- B. Use the SIEM to correlate logging events from the email server and the domain server.
- C. Remove the rule from the email client and change the password.
- D. Recommend that the management team implement SPF and DKIM.
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
- A. CIP
- B. DHCP
- C. SSH
- D. Modbus
A system that provides the user interface for a critical server has potentially been corrupted by malware. Which of the following is the best recommendation to ensure business continuity?
- A. System isolation
- B. Reimaging
- C. Malware removal
- D. Vulnerability scanning
