
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A new prototype for a company’s flagship product was leaked on the internet. As a result, the management team has locked out all USB dives. Optical drive writers are not present on company computers. The sales team has been granted an exception to share sales presentation files with third parties. Which of the following would allow the IT team to determine which devices are USB enabled?
- A. Asset tagging
- B. Device encryption
- C. Data loss prevention
- D. SIEM logs
A security officer needs to find a solution to the current data privacy and protection gap found in the last security assessment. Which of the following is the most cost-effective solution?
- A. Require users to sign NDAs.
- B. Create a data minimization plan.
- C. Add access control requirements.
- D. Implement a data loss prevention solution.
A development team recently released a new version of a public-facing website for testing prior to production. The development team is soliciting the help of various teams to validate the functionality of the website due to its high visibility. Which of the following activities best describes the process the development team is initiating?
- A. Static analysis
- B. Stress testing
- C. Code review
- D. User acceptance testing
A cybersecurity analyst is concerned about attacks that use advanced evasion techniques. Which of the following would best mitigate such attacks?
- A. Keeping IPS rules up to date
- B. Installing a proxy server
- C. Applying network segmentation
- D. Updating the antivirus software
Which of the following is most appropriate to use with SOAR when the security team would like to automate actions across different vendor platforms?
- A. STIX/TAXII
- B. APIs
- C. Data enrichment
- D. Threat feed
Thousands of computers were compromised in a breach, but the vulnerability that caused the compromise was detected on only three computers during the latest vulnerability scan. An analyst conducts an after action review to determine why the vulnerability was not detected on more computers. The analyst recreates the following configuration that was used to scan the network:
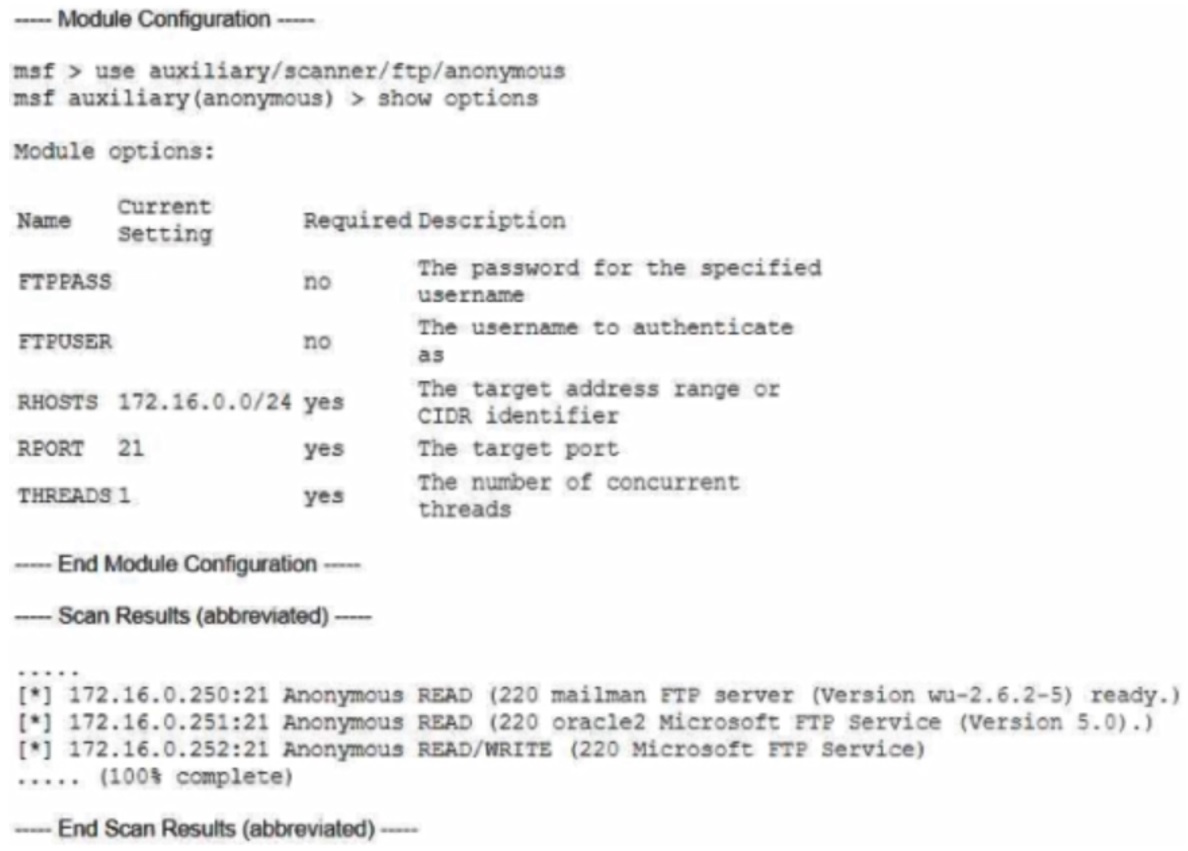
Which of the following best explains the reason the vulnerability was found only on three computers?
- A. Incorrect remote port specified
- B. Lack of concurrent threads dedicated
- C. Use of a credentialed vulnerability scan
- D. Configuring an incorrect subnet mask
A security analyst needs to develop a solution to protect a high-value asset from an exploit like a recent zero-day attack. Which of the following best describes this risk management strategy?
- A. Avoid
- B. Transfer
- C. Accept
- D. Mitigate
An organization identifies a method to detect unexpected behavior, crashes, or resource leaks in a system by feeding invalid, unexpected, or random data to stress the application. Which of the following best describes this testing methodology?
- A. Reverse engineering
- B. Static
- C. Fuzzing
- D. Debugging
A security technician is testing a solution that will prevent outside entities from spoofing the company’s email domain, which is comptia.org. The testing is successful, and the security technician is prepared to fully implement the solution. Which of the following actions should the technician take to accomplish this task?
- A. Add TXT @ “v=spfl mx include:_spf.comptia.org -all” to the DNS record.
- B. Add TXT @ “v=spfl mx include:_spf.comptia.org -all” to the email server.
- C. Add TXT @ “v=spfl mx include:_spf.comptia.org +all” to the domain controller.
- D. Add TXT @ “v=spfl mx include:_spf.comptia.org +all” to the web server.
A security analyst recently observed evidence of an attack against a company’s web server. The analyst investigated the issue but was unable to find an exploit that adequately explained the observations. Which of the following is the most likely cause of this issue?
- A. The security analyst needs updated forensic analysis tools.
- B. The security analyst needs more training on threat hunting and research.
- C. The security analyst has potentially found a zero-day vulnerability that has been exploited.
- D. The security analyst has encountered a polymorphic piece of malware.
