
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A manufacturing company has joined the information sharing and analysis center for its sector. As a benefit, the company will receive structured IoC data contributed by other members. Which of the following best describes the utility of this data?
- A. Other members will have visibility into instances of positive IoC identification within the manufacturing company’s corporate network.
- B. The manufacturing company will have access to relevant malware samples from all other manufacturing sector members.
- C. Other members will automatically adjust their security postures to defend the manufacturing company’s processes.
- D. The manufacturing company can ingest the data and use tools to autogenerate security configurations for all of its infrastructure.
As part of a merger with another organization, a Chief Information Security Officer (CISO) is working with an assessor to perform a risk assessment focused on data privacy compliance. The CISO is primarily concerned with the potential legal liability and fines associated with data privacy. Based on the CISO’s concerns, the assessor will most likely focus on:
- A. qualitative probabilities.
- B. quantitative probabilities.
- C. qualitative magnitude.
- D. quantitative magnitude.
A security audit for unsecured network services was conducted, and the following output was generated:
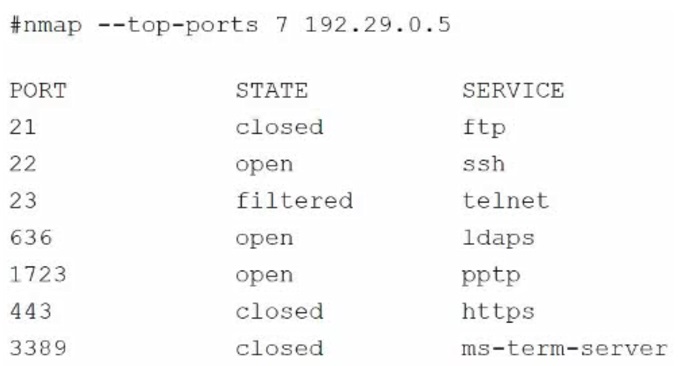
Which of the following services should the security team investigate further? (Choose two.)
- A. 21
- B. 22
- C. 23
- D. 636
- E. 1723
- F. 3389
A company is moving from the use of web servers hosted in an internal data center to a containerized cloud platform. An analyst has been asked to identify indicators of compromise in the containerized environment. Which of the following would best indicate a running container has been compromised?
- A. A container from an approved software image has drifted.
- B. An approved software orchestration container is running with root privileges.
- C. A container from an approved software image has stopped responding.
- D. A container from an approved software image fails to start.
An incident response team is assessing attack vectors of malware that is encrypting data with ransomware. There are no indications of a network-based intrusion. Which of the following is the most likely root cause of the incident?
- A. USB drop
- B. LFI
- C. Cross-site forgery
- D. SQL injection
A security analyst scanned an internal company subnet and discovered a host with the following Nmap output:
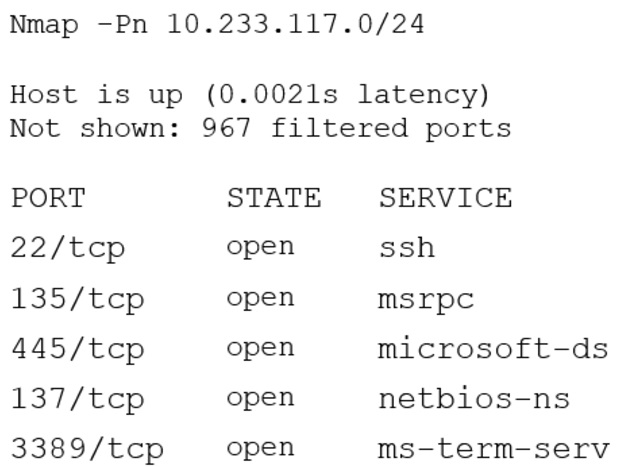
Based on the output of this Nmap scan, which of the following should the analyst investigate FIRST?
- A. Port 22
- B. Port 135
- C. Port 445
- D. Port 3389
A security analyst is investigating a malware infection that occurred on a Windows system. The system was not connected to a network and had no wireless capability. Company policy prohibits using portable media or mobile storage. The security analyst is trying to determine which user caused the malware to get onto the system. Which of the following registry keys would most likely have this information?
- A. HKEY_USERS\\Software\Microsoft\Windows\CurrentVersion\Run
- B. HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- C. HKEY_USERS\\Software\Microsoft\Windows\explorer\MountPoints2
- D. HKEY_USERS\\Software\Microsoft\Internet Explorer\Typed URLs
- E. HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\eventlog\System\iusb3hub
A company is launching a new application in its internal network, where internal customers can communicate with the service desk. The security team needs to ensure the application will be able to handle unexpected strings with anomalous formats without crashing. Which of the following processes is the most applicable for testing the application to find how it would behave in such a situation?
- A. Fuzzing
- B. Coding review
- C. Debugging
- D. Static analysis
A SOC analyst observes reconnaissance activity from an IP address. The activity follows a pattern of short bursts toward a low number of targets. An open-source review shows that the IP has a bad reputation. The perimeter firewall logs indicate the inbound traffic was allowed. The destination hosts are high-value assets with EDR agents installed. Which of the following is the best action for the SOC to take to protect against any further activity from the source IP?
- A. Add the IP address to the EDR deny list.
- B. Create a SIEM signature to trigger on any activity from the source IP subnet detected by the web proxy or firewalls for immediate notification.
- C. Implement a prevention policy for the IP on the WAF.
- D. Activate the scan signatures for the IP on the NGFWs.
A company’s internet-facing web application has been compromised several times due to identified design flaws. The company would like to minimize the risk of these incidents from reoccurring and has provided the developers with better security training. However, the company cannot allocate any more internal resources to the issue. Which of the following are the best options to help identify flaws within the system? (Choose two.)
- A. Deploying a WAF
- B. Performing a forensic analysis
- C. Contracting a penetration test
- D. Holding a tabletop exercise
- E. Creating a bug bounty program
- F. Implementing threat modeling
