
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
The SOC receives a number of complaints regarding a recent uptick in desktop error messages that are associated with workstation access to an internal web application. An analyst, identifying a recently modified XML file on the web server, retrieves a copy of this file for review, which contains the following code:
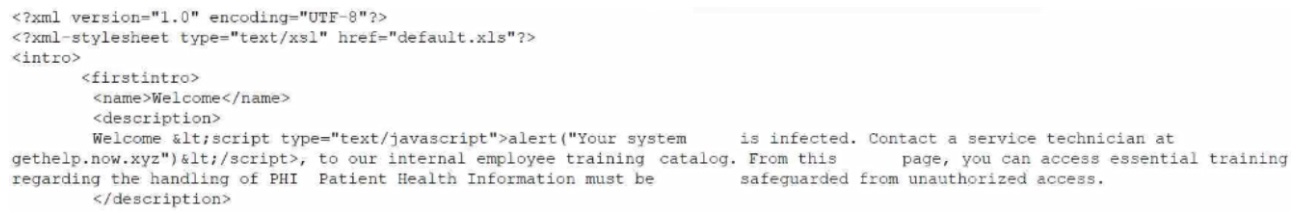
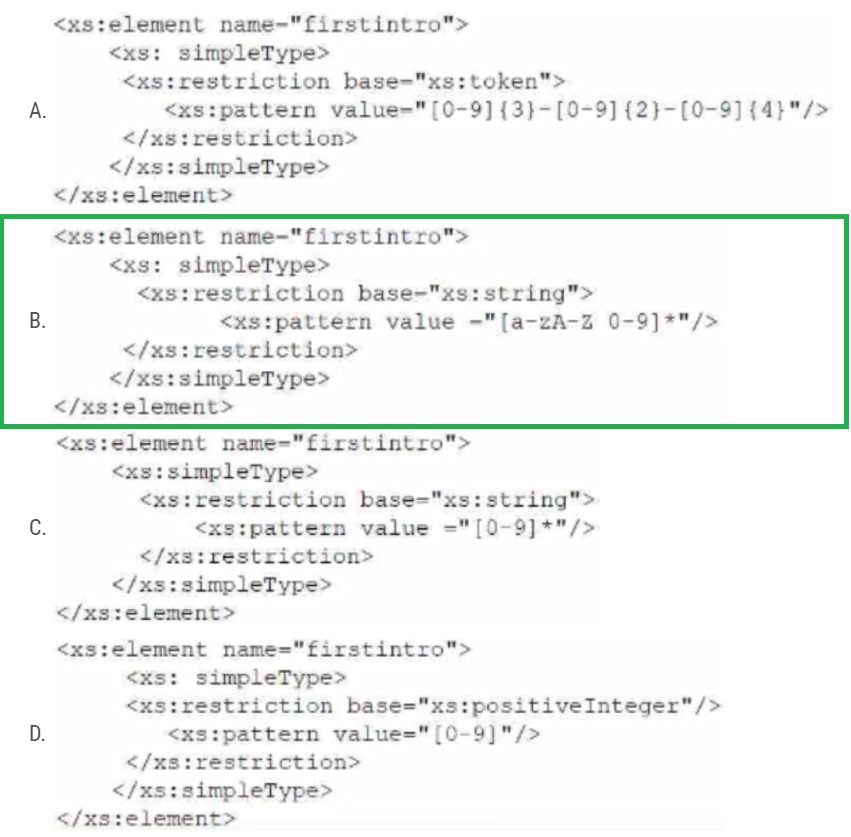
Which of the following XML schema constraints would stop these desktop error messages from appearing?
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network. Which of the following technologies should the analyst recommend?
- A. UEBA
- B. DLP
- C. NAC
- D. EDR
A security analyst needs to identify services in a small, critical infrastructure ICS network. Many components in the network are likely to break if they receive malformed or unusually large requests. Which of the following is the safest method to use when identifying service versions?
- A. Use nmap -sV to identify all assets on the network.
- B. Use Burp Suite to conduct service identification.
- C. Use nc to manually perform banner grabbing.
- D. Use Nessus with restricted concurrent connections.
A web application has a function to retrieve content from an internal URL to identify CSRF attacks in the logs. The security analyst is building a regular expression that will filter out the correctly formatted requests. The target URL is https://10.1.2.3/api, and the receiving API only accepts GET requests and uses a single integer argument named “id.” Which of the following regular expressions should the analyst use to achieve the objective?
- A. ^(?!https://10\.1\.2\.3/api\?id=[0-9]+)
- B. ^https://10\.1\.2\.3/api\?id=\d+
- C. (?:^https://10\.1\.2\.3/api\?id=[0-9]+)
- D. ^https://10\.1\.2\.3/api\?id=[0-9]+$
A security analyst needs to identify a computer based on the following requirements to be mitigated:
• The attack method is network based with low complexity.
• No privileges or user action is needed.
• The confidentiality and availability level is high with a low integrity level.
Given the following CVSS 3.1 output:
Computer1 –
CVSS3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:L/A:H
Computer2 –
CVSS3.1/AV:L/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer3 –
CVSS3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:L/A:H
Computer4 –
CVSS3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
Which of the following machines should the analyst mitigate?
- A. Computer1
- B. Computer2
- C. Computer3
- D. Computer4
An analyst would like to start automatically ingesting IoCs into the EDR tool. Which of the following sources would be the most cost effective for the analyst to use?
- A. Government bulletins
- B. Social media
- C. Dark web
- D. Blogs
A security operations manager wants to build out an internal threat-hunting capability. Which of the following should be the first priority when creating a threat-hunting program?
- A. Establishing a hypothesis about which threats are targeting which systems
- B. Profiling common threat actors and activities to create a list of IOCs
- C. Ensuring logs are sent to a centralized location with search and filtering capabilities
- D. Identifying critical assets that will be used to establish targets for threat-hunting activities
During normal security monitoring activities, the following activity was observed:
cd C:\Users\Documents\HR\Employees
takeown/f .*
SUCCESS:
Which of the following best describes the potentially malicious activity observed?
- A. Registry changes or anomalies
- B. Data exfiltration
- C. Unauthorized privileges
- D. File configuration changes
A company has a popular shopping cart website hosted geographically diverse locations. The company has started hosting static content on a content delivery network (CDN) to improve performance. The CDN provider has reported the company is occasionally sending attack traffic to other CDN-hosted targets.
Which of the following has MOST likely occurred?
- A. The CDN provider has mistakenly performed a GeoIP mapping to the company.
- B. The CDN provider has misclassified the network traffic as hostile.
- C. A vulnerability scan has tuned to exclude web assets hosted by the CDN.
- D. The company has been breached, and customer PII is being exfiltrated to the CDN.
Which of the following best describes the process by which code is developed, tested, and deployed in small batches?
- A. Agile
- B. Waterfall
- C. SDLC
- D. Dynamic code analysis
