
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst is reviewing the logs and notices the following entries:
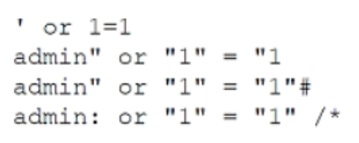
Which of the following most likely occurred?
- A. LDAP injection
- B. Clickjacking
- C. XSS
- D. SQLi
A security administrator has found indications of dictionary attacks against the company’s external-facing portal. Which of the following should be implemented to best mitigate the password attacks?
- A. Multifactor authentication
- B. Password complexity
- C. Web application firewall
- D. Lockout policy
The security team reviews a web server for XSS and runs the following Nmap scan:
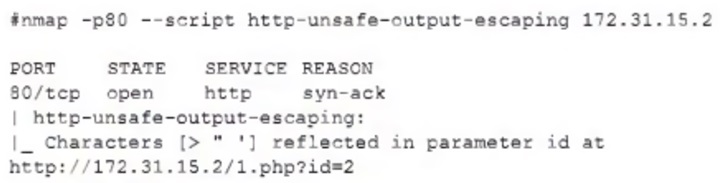
Which of the following most accurately describes the result of the scan?
- A. An output of characters > and ” as the parameters used in the attempt
- B. The vulnerable parameter ID http://172.31.15.2/1.php?id=2 and unfiltered characters returned
- C. The vulnerable parameter and unfiltered or encoded characters passed > and ” as unsafe
- D. The vulnerable parameter id=2 with a SQL injection attempt
A security analyst has identified outgoing network traffic leaving the enterprise at odd times. The traffic appears to pivot across network segments and target domain servers. The traffic is then routed to a geographic location to which the company has no association. Which of the following best describes this type of threat?
- A. Hacktivist
- B. Zombie
- C. Insider threat
- D. Nation-state actor
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IoC list for monitoring. Which of the following is the best suggestion for improving monitoring capabilities?
- A. Update the IPS and IDS with the latest rule sets from the provider.
- B. Create an automated script to update the IPS and IDS rule sets.
- C. Use an automated subscription to select threat feeds for IDS.
- D. Implement an automated malware solution on the IPS.
A large company wants to address frequent outages on critical systems with a secure configurations program. The Chief Information Security Officer (CISO) has asked the analysts to conduct research and make recommendations for a cost-effective solution with the least amount of disruption to the business. Which of the following would be the best way to achieve these goals?
- A. Adopt the CIS security controls as a framework, apply configurations to all assets, and then notify asset owners of the change.
- B. Coordinate with asset owners to assess the impact of the CIS critical security controls, perform testing, and then implement across the enterprise.
- C. Recommend multiple security controls depending on business unit needs, and then apply configurations according to the organization’s risk tolerance.
- D. Ask asset owners which configurations they would like, compile the responses, and then present all options to the CISO for approval to implement.
A monthly job to install approved vendor software updates and hot fixes recently stopped working. The security team performed a vulnerability scan, which identified several hosts as having some critical OS vulnerabilities, as referenced in the common vulnerabilities and exposures (CVE) database. Which of the following should the security team do next to resolve the critical findings in the most effective manner? (Choose two.)
- A. Patch the required hosts with the correct updates and hot fixes, and rescan them for vulnerabilities.
- B. Remove the servers reported to have high and medium vulnerabilities.
- C. Tag the computers with critical findings as a business risk acceptance.
- D. Manually patch the computers on the network, as recommended on the CVE website.
- E. Harden the hosts on the network, as recommended by the NIST framework.
- F. Resolve the monthly job issues and test them before applying them to the production network.
A consumer credit card database was compromised, and multiple representatives are unable to review the appropriate customer information. Which of the following should the cybersecurity analyst do first?
- A. Start the containment effort.
- B. Confirm the incident.
- C. Notify local law enforcement officials.
- D. Inform the senior management team.
An end user forwarded an email with a file attachment to the SOC for review. The SOC analysts think the file was specially crafted for the target. Which of the following investigative actions would best determine if the attachment was malicious?
- A. Review the file in Virus Total to determine if the domain is associated with any phishing.
- B. Review the email header to analyze the DKIM, DMARC, and SPF values.
- C. Review the source IP address in AbuseIPDB.
- D. Review the attachment’s behavior in a sandbox environment while running Wireshark.
Which of the following is instituting a security policy that users must lock their systems when stepping away from their desks an example of?
- A. Configuration management
- B. Compensating control
- C. Awareness, education, and training
- D. Administrative control
