
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A security analyst needs to identify an asset that should be remediated based on the following information:
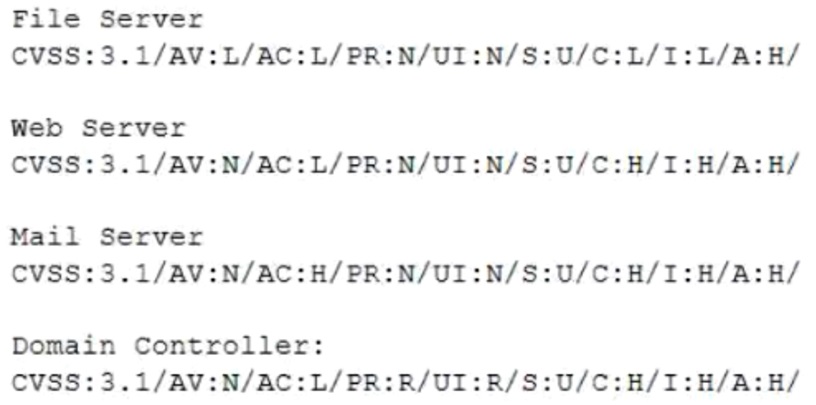
Which of the following assets should the analyst remediate first?
- A. Mail server
- B. Domain controller
- C. Web server
- D. File server
A security technician configured a NIDS to monitor network traffic. Which of the following is a condition in which harmless traffic is classified as a potential network attack?
- A. True positive
- B. True negative
- C. False positive
- D. False negative
Which of the following is the greatest security concern regarding ICS?
- A. The involved systems are generally hard to identify.
- B. The systems are configured for automatic updates, leading to device failure.
- C. The systems are oftentimes air gapped, leading to fileless malware attacks.
- D. Issues on the systems cannot be reversed without rebuilding the systems.
A cybersecurity analyst is setting up a security control that monitors network traffic and produces an active response to a security event. Which of the following tools is the analyst configuring?
- A. EDR
- B. IPS
- C. CASB
- D. WAF
Members of the sales team are using email to send sensitive client lists with contact information to their personal accounts. The company’s AUP and code of conduct prohibits this practice. Which of the following configuration changes would improve security and help prevent this from occurring?
- A. Configure the DLP transport rules to provide deep content analysis.
- B. Put employees’ personal email accounts on the mail server on a blocklist.
- C. Set up IPS to scan for outbound emails containing names and contact information.
- D. Use Group Policy to prevent users from copying and pasting information into emails.
- E. Move outbound emails containing names and contact information to a sandbox for further examination.
Which of the following are process improvements that can be realized by implementing a SOAR solution? (Choose two.)
- A. Minimize security attacks.
- B. Itemize tasks for approval.
- C. Reduce repetitive tasks.
- D. Minimize setup complexity.
- E. Define a security strategy.
- F. Generate reports and metrics.
During an investigation, an analyst discovers a server is vulnerable to an attack against an application that processes XML input. Which of the following controls must be in place to prevent such an attack?
- A. Filter all inputs, applying the allow list concept for each parameter from XML content.
- B. Enable an XML external entity and escape each parameter that is received through the XML file.
- C. Implement parameterized queries for each XML parser.
- D. Disable document type definitions completely using the proper method for each parser.
During an incident, an analyst works closely with specific team members. Which of the following best explains why communication is limited to specific team members?
- A. To determine when information can be released
- B. To provide rules and regulations on reporting requirements
- C. To prevent an inadvertent release of information
- D. To determine who can participate
Which of the following features is a key component of Zero Trust architecture?
- A. Single strong source of user identity
- B. Implementation of IT governance
- C. Business continuity plan
- D. Quality assurance
- E. Internal auditing process
During a risk assessment, a senior manager inquires about what the cost would be if a unique occurrence would impact the availability of a critical service. The service generates $1,000 in revenue for the organization. The impact of the attack would affect 20% of the server’s capacity to perform jobs. The organization expects that five out of twenty attacks would succeed during the year. Which of the following is the calculated single loss expectancy?
- A. $200
- B. $800
- C. $5,000
- D. $20,000
During an audit, several customer order forms were found to contain inconsistencies between the actual price of an item and the amount charged to the customer. Further investigation narrowed the cause of the issue to manipulation of the public-facing web form used by customers to order products. Which of the following would be the best way to locate this issue?
- A. Reduce the session timeout threshold.
- B. Deploy MFA for access to the web server.
- C. Implement input validation.
- D. Run a dynamic code analysis.
