
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
During the onboarding process for a new vendor, a security analyst obtains a copy of the vendor’s latest penetration test summary:
Performed by: Vendor Red Team –
Last performed: 14 days ago –
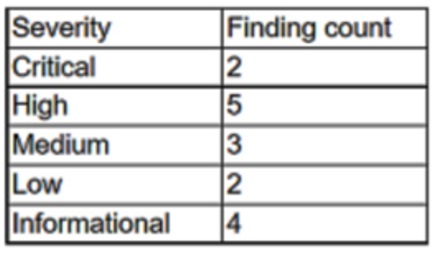
Which of the following recommendations should the analyst make first?
- A. Perform a more recent penetration test.
- B. Continue vendor onboarding.
- C. Disclose details regarding the findings.
- D. Have a neutral third party perform a penetration test.
A security analyst is reviewing malware files without running them. Which of the following analysis types is the security analyst using?
- A. Dynamic
- B. Sandbox
- C. Static
- D. Heuristic
A user’s computer is performing slower than the day before, and unexpected windows continually open and close. The user did not install any new programs, and after the user restarted the desktop, the issue was not resolved. Which of the following incident response actions should be taken next?
- A. Restart in safe mode and start a virus scan.
- B. Disconnect from the network and leave the PC turned on.
- C. Contain the device and implement a legal hold.
- D. Reformat and reimage the OS.
An analyst is reviewing email headers to determine if an email has been sent from a legitimate sender. The organization uses SPF to validate email origination. Which of the following most likely indicates an invalid originator?
- A. Received-SPF: neutral
- B. Received-SPF: none
- C. Received-SPF: softfail
- D. Received-SPF: error
Which of the following SCAP standards provides standardization for measuring and describing the severity of security-related software flaws?
- A. OVAL
- B. CVSS
- C. CVE
- D. CCE
A security analyst at an organization is reviewing vulnerability reports from a newly deployed vulnerability management platform. The organization is not receiving information about devices that rarely connect to the network. Which of the following will the analyst most likely do to obtain vulnerability information about these devices?
- A. Add administrator credentials to mobile devices.
- B. Utilize cloud-based agents.
- C. Deploy a VPC in front of a NAC.
- D. Implement MDM.
An analyst needs to provide recommendations based on the following vulnerability report:
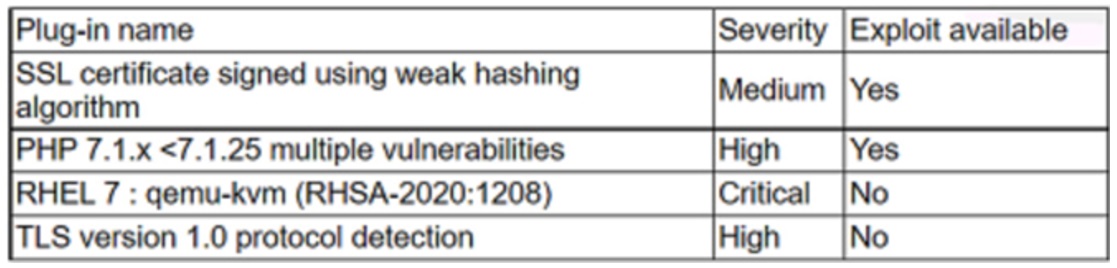
Which of the following vulnerabilities should the analyst recommend addressing first?
- A. SSL certificate signed using weak hashing algorithm
- B. TLS version 1.0 protocol detection
- C. PHP 7.1.x <7.1.25 multiple vulnerabilities
- D. RHEL 7 : qemu-kvm (RHSA-2020:1208)
Which of the following would best protect sensitive data if a device is stolen?
- A. Remote wipe of drive
- B. Self-encrypting drive
- C. Password-protected hard drive
- D. Bus encryption
Which of the following describes the difference between intentional and unintentional insider threats?
- A. Their access levels will be different.
- B. The risk factor will be the same.
- C. Their behavior will be different.
- D. The rate of occurrence will be the same.
During a packet capture review, a security analyst identifies the output below as suspicious:
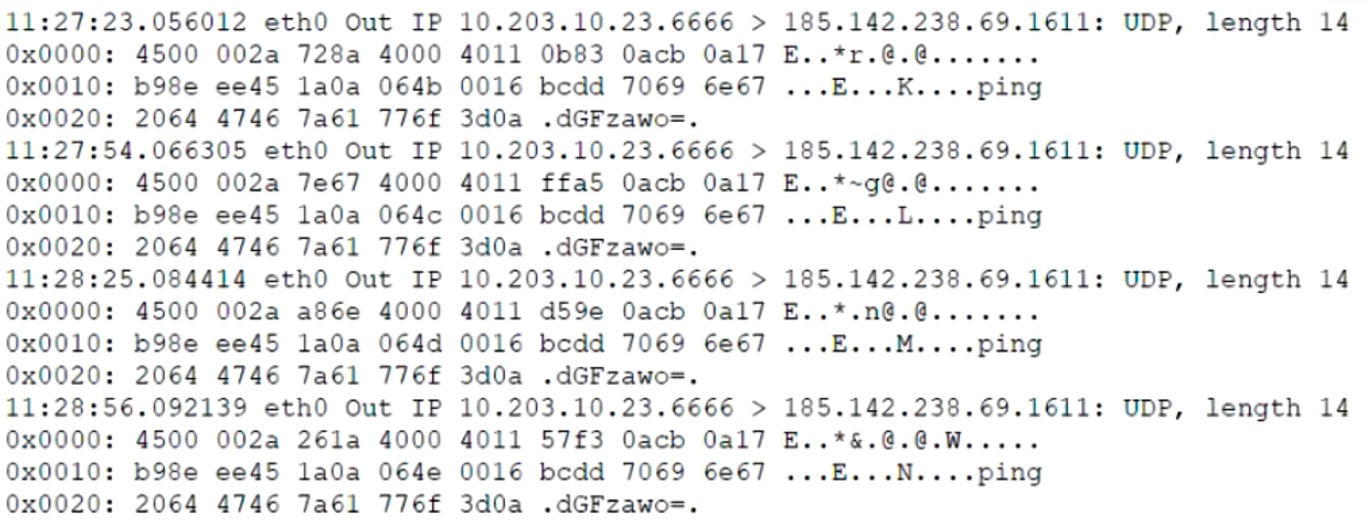
Which of the following best describes the type of activity the analyst has identified?
- A. Ping sweep
- B. Port scan
- C. DoS attack
- D. Beaconing
