
Pass CompTIA Network+ N10-009 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
Which of the following attacks can cause users who are attempting to access a company website to be directed to an entirely different website?
- A. DNS poisoning
- B. Denial-of-service
- C. Social engineering
- D. ARP spoofing
As part of an attack, a threat actor purposefully overflows the content-addressable memory (CAM) table on a switch. Which of the following types of attacks is this scenario an example of?
- A. ARP spoofing
- B. Evil twin
- C. MAC flooding
- D. DNS poisoning
A company’s office has publicly accessible meeting rooms equipped with network ports. A recent audit revealed that visitors were able to access the corporate network by plugging personal laptops into open network ports. Which of the following should the company implement to prevent this in the future?
- A. URL filters
- B. VPN
- C. ACLs
- D. NAC
A user notifies a network administrator about losing access to a remote file server. The network administrator is able to ping the server and verifies the current firewall rules do not block access to the network fileshare. Which of the following tools would help identify which ports are open on the remote file server?
- A. dig
- B. nmap
- C. tracert
- D. nslookup
Which of the following technologies is the best choice to listen for requests and distribute user traffic across web servers?
- A. Router
- B. Switch
- C. Firewall
- D. Load balancer
A company is hosting a secure server that requires all connections to the server to be encrypted. A junior administrator needs to harden the web server. The following ports on the web server are open:
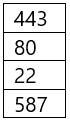
Which of the following ports should be disabled?
- A. 22
- B. 80
- C. 443
- D. 587
Which of the following is the next step to take after successfully testing a root cause theory?
- A. Determine resolution steps.
- B. Duplicate the problem in a lab.
- C. Present the theory for approval.
- D. Implement the solution to the problem.
A network administrator is configuring a new switch and wants to ensure that only assigned devices can connect to the switch. Which of the following should the administrator do?
- A. Configure ACLs.
- B. Implement a captive portal.
- C. Enable port security.
- D. Disable unnecessary services.
A customer needs six usable IP addresses. Which of the following best meets this requirement?
- A. 255.255.255.128
- B. 255.255.255.192
- C. 255.255.255.224
- D. 255.255.255.240
A user reports having intermittent connectivity issues to the company network. The network configuration for the user reveals the following:
IP address: 192.168.1.10 –
Subnet mask: 255.255.255.0 –
Default gateway: 192.168.1.254 –
The network switch shows the following ARP table:
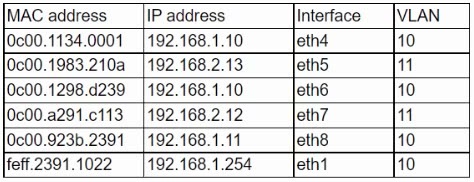
Which of the following is the most likely cause of the user’s connection issues?
- A. A port with incorrect VLAN assigned
- B. A switch with spanning tree conflict
- C. Another PC with manually configured IP
- D. A router with overlapping route tables
