
Pass CompTIA Network+ N10-009 in Just 3 Days – Stress-Free, No Study Needed!
Have questions? Contact us directly on WhatsApp for quick support!
Question 3010Please leave a feedback on thisx
Which of the following best describes a group of devices that is used to lure unsuspecting attackers and to study the attackers’ activities?
A. Geofencing
B. Honeynet
C. Jumpbox
D. Screened subnet
Question 302
0
Please leave a feedback on thisx
A network engineer configures a new switch and connects it to an existing switch for expansion and redundancy. Users immediately lose connectivity to the network. The network engineer notes the following spanning tree information from both switches.
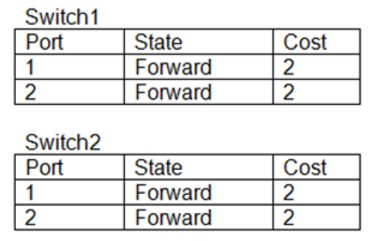
Which of the following best describes the issue?
- A. The port cost should not be equal.
- B. The ports should use link aggregation.
- C. A root bridge needs to be identified.
- D. The switch should be configured for RSTP.
Question 3030Please leave a feedback on thisx
Which of the following routing protocols is most commonly used to interconnect WANs?
A. IGP
B. EIGRP
C. BGP
D. OSPF
Question 304
0
Please leave a feedback on thisx
After installing a series of Cat 8 keystones, a data center architect notices higher than normal interference during tests. Which of the following steps should the architect take to troubleshoot the issue?
A. Check to see if the end connections were wrapped in copper tape before terminating.
B. Use passthrough modular crimping plugs instead of traditional crimping plugs.
C. Connect the RX/TX wires to different pins.
D. Run a speed test on a device that can only achieve 100Mbps speeds.
