
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
After reviewing the following vulnerability scanning report:

A security analyst performs the following test:
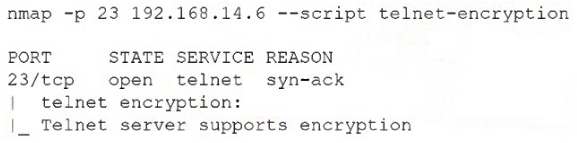
Which of the following would the security analyst conclude for this reported vulnerability?
- A. It is a false positive.
- B. A rescan is required.
- C. It is considered noise.
- D. Compensating controls exist.
An organization disabled unneeded services and placed a firewall in front of a business-critical legacy system. Which of the following best describes the actions taken by the organization?
- A. Exception
- B. Segmentation
- C. Risk transfer
- D. Compensating controls
A security consultant needs secure, remote access to a client environment. Which of the following should the security consultant most likely use to gain access?
- A. EAP
- B. DHCP
- C. IPSec
- D. NAT
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
- A. Software as a service
- B. Infrastructure as code
- C. Internet of Things
- D. Software-defined networking
After a security awareness training session, a user called the IT help desk and reported a suspicious call. The suspicious caller stated that the Chief Financial Officer wanted credit card information in order to close an invoice. Which of the following topics did the user recognize from the training?
- A. Insider threat
- B. Email phishing
- C. Social engineering
- D. Executive whaling
A security administrator is deploying a DLP solution to prevent the exfiltration of sensitive customer data. Which of the following should the administrator do first?
- A. Block access to cloud storage websites.
- B. Create a rule to block outgoing email attachments.
- C. Apply classifications to the data.
- D. Remove all user permissions from shares on the file server.
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
- A. Compromise
- B. Retention
- C. Analysis
- D. Transfer
- E. Inventory
A company is working with a vendor to perform a penetration test. Which of the following includes an estimate about the number of hours required to complete the engagement?
- A. SOW
- B. BPA
- C. SLA
- D. NDA
A Chief Information Security Officer (CISO) wants to explicitly raise awareness about the increase of ransomware-as-a-service in a report to the management team. Which of the following best describes the threat actor in the CISO’s report?
- A. Insider threat
- B. Hacktivist
- C. Nation-state
- D. Organized crime
Which of the following practices would be best to prevent an insider from introducing malicious code into a company’s development process?
- A. Code scanning for vulnerabilities
- B. Open-source component usage
- C. Quality assurance testing
- D. Peer review and approval
