
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Which of the following describes a security alerting and monitoring tool that collects system, application, and network logs from multiple sources in a centralized system?
- A. SIEM
- B. DLP
- C. IDS
- D. SNMP
A network manager wants to protect the company’s VPN by implementing multifactor authentication that uses:
Something you know –
Something you have –
Something you are –
Which of the following would accomplish the manager’s goal?
- A. Domain name, PKI, GeoIP lookup
- B. VPN IP address, company ID, facial structure
- C. Password, authentication token, thumbprint
- D. Company URL, TLS certificate, home address
Which of the following would be the best way to handle a critical business application that is running on a legacy server?
- A. Segmentation
- B. Isolation
- C. Hardening
- D. Decommissioning
Which of the following vulnerabilities is exploited when an attacker overwrites a register with a malicious address?
- A. VM escape
- B. SQL injection
- C. Buffer overflow
- D. Race condition
After a company was compromised, customers initiated a lawsuit. The company’s attorneys have requested that the security team initiate a legal hold in response to the lawsuit. Which of the following describes the action the security team will most likely be required to take?
- A. Retain the emails between the security team and affected customers for 30 days.
- B. Retain any communications related to the security breach until further notice.
- C. Retain any communications between security members during the breach response.
- D. Retain all emails from the company to affected customers for an indefinite period of time.
Which of the following describes the process of concealing code or text inside a graphical image?
- A. Symmetric encryption
- B. Hashing
- C. Data masking
- D. Steganography
An employee receives a text message from an unknown number claiming to be the company’s Chief Executive Officer and asking the employee to purchase several gift cards. Which of the following types of attacks does this describe?
- A. Vishing
- B. Smishing
- C. Pretexting
- D. Phishing
Which of the following risk management strategies should an enterprise adopt first if a legacy application is critical to business operations and there are preventative controls that are not yet implemented?
- A. Mitigate
- B. Accept
- C. Transfer
- D. Avoid
Security analysts are conducting an investigation of an attack that occurred inside the organization’s network. An attacker was able to collect network traffic between workstations throughout the network. The analysts review the following logs:
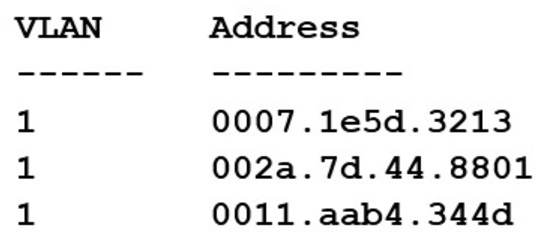
The Layer 2 address table has hundreds of entries similar to the ones above. Which of the following attacks has MOST likely occurred?
- A. SQL injection
- B. DNS spoofing
- C. MAC flooding
- D. ARP poisoning
The local administrator account for a company’s VPN appliance was unexpectedly used to log in to the remote management interface. Which of the following would have most likely prevented this from happening?
- A. Using least privilege
- B. Changing the default password
- C. Assigning individual user IDs
- D. Reviewing logs more frequently
