
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Which of the following is the best way to secure an on-site data center against intrusion from an insider?
- A. Bollards
- B. Access badge
- C. Motion sensor
- D. Video surveillance
An engineer moved to another team and is unable to access the new team’s shared folders while still being able to access the shared folders from the former team. After opening a ticket, the engineer discovers that the account was never moved to the new group. Which of the following access controls is most likely causing the lack of access?
- A. Role-based
- B. Discretionary
- C. Time of day
- D. Least privilege
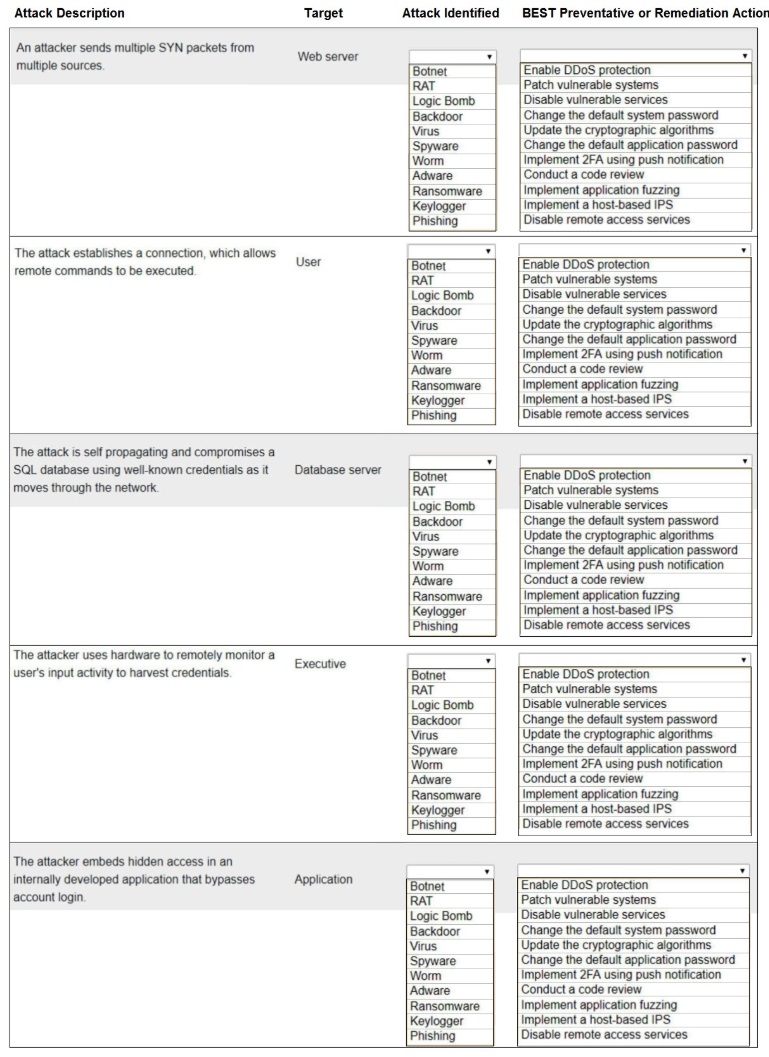
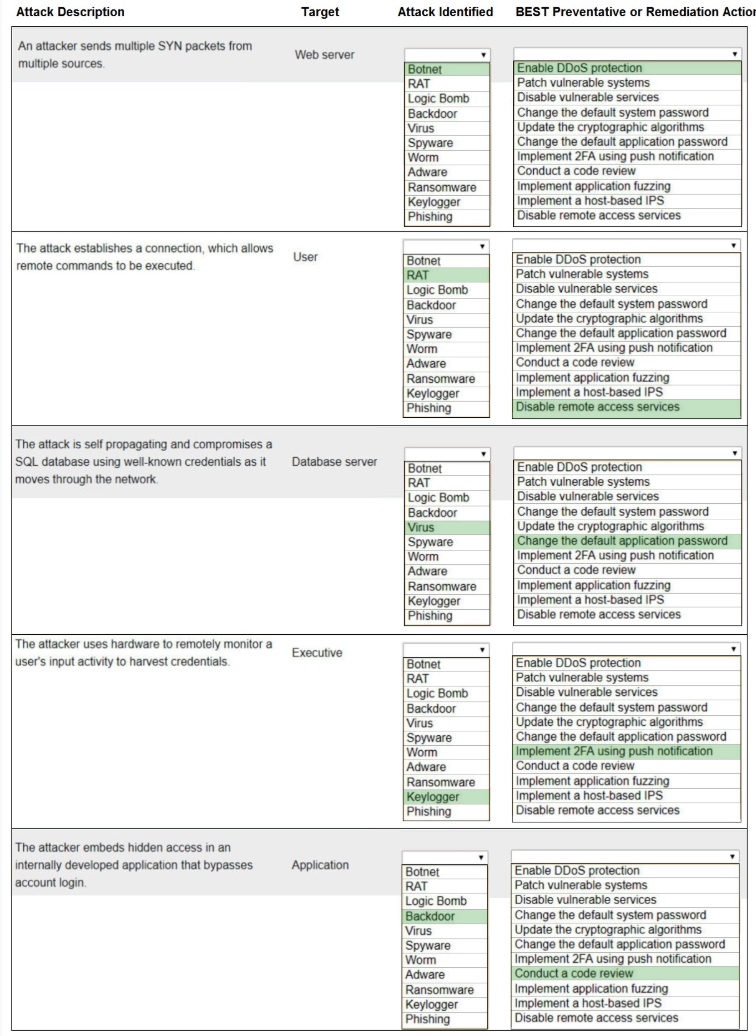
HOTSPOT –
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS –
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Hot Area:
A network administrator is working on a project to deploy a load balancer in the company’s cloud environment. Which of the following fundamental security requirements does this project fulfil?
- A. Privacy
- B. Integrity
- C. Confidentiality
- D. Availability
A systems administrator is changing the password policy within an enterprise environment and wants this update implemented on all systems as quickly as possible. Which of the following operating system security measures will the administrator most likely use?
- A. Deploying PowerShell scripts
- B. Pushing GPO update
- C. Enabling PAP
- D. Updating EDR profiles
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
- A. RPO
- B. ALE
- C. SLE
- D. RTO
- E. ARO
In order to strengthen a password and prevent a hacker from cracking it, a random string of 36 characters was added to the password. Which of the following best describes this technique?
- A. Key stretching
- B. Tokenization
- C. Data masking
- D. Salting
A technician is deploying a new security camera. Which of the following should the technician do?
- A. Configure the correct VLAN.
- B. Perform a vulnerability scan.
- C. Disable unnecessary ports.
- D. Conduct a site survey.
A company is experiencing a web services outage on the public network. The services are up and available but inaccessible. The network logs show a sudden increase in network traffic that is causing the outage. Which of the following attacks is the organization experiencing?
- A. ARP poisoning
- B. Brute force
- C. Buffer overflow
- D. DDoS
Which of the following threat actors is the most likely to be motivated by profit?
- A. Hacktivist
- B. Insider threat
- C. Organized crime
- D. Shadow IT
