
Pass CompTIA Security+ SY0-701 in Just 3 Days – Stress-Free!
Get your Security+ SY0-701 certification with 100% pass guarantee. Pay only after passing!
Click here to secure your guaranteed certification now!
Have questions? Contact us directly on WhatsApp for quick support!
Which of the following describes effective change management procedures?
- A. Approving the change after a successful deployment
- B. Having a backout plan when a patch fails
- C. Using a spreadsheet for tracking changes
- D. Using an automatic change control bypass for security updates
The CIRT is reviewing an incident that involved a human resources recruiter exfiltrating sensitive company data. The CIRT found that the recruiter was able to use HTTP over port 53 to upload documents to a web server. Which of the following security infrastructure devices could have identified and blocked this activity?
- A. WAF utilizing SSL decryption
- B. NGFW utilizing application inspection
- C. UTM utilizing a threat feed
- D. SD-WAN utilizing IPSec
An enterprise is working with a third party and needs to allow access between the internal networks of both parties for a secure file migration. The solution needs to ensure encryption is applied to all traffic that is traversing the networks. Which of the following solutions should most likely be implemented?
- A. EAP
- B. IPSec
- C. SD-WAN
- D. TLS
An administrator has identified and fingerprinted specific files that will generate an alert if an attempt is made to email these files outside of the organization. Which of the following best describes the tool the administrator is using?
- A. DLP
- B. SNMP traps
- C. SCAP
- D. IPS
A software developer released a new application and is distributing application files via the developer’s website. Which of the following should the developer post on the website to allow users to verify the integrity of the downloaded files?
- A. Hashes
- B. Certificates
- C. Algorithms
- D. Salting
An administrator finds that all user workstations and servers are displaying a message that is associated with files containing an extension of .ryk. Which of the following types of infections is present on the systems?
A. Virus
B. Trojan
C. Spyware
D. Ransomware
A systems administrator is advised that an external web server is not functioning property. The administrator reviews the following firewall logs containing traffic going to the web server:
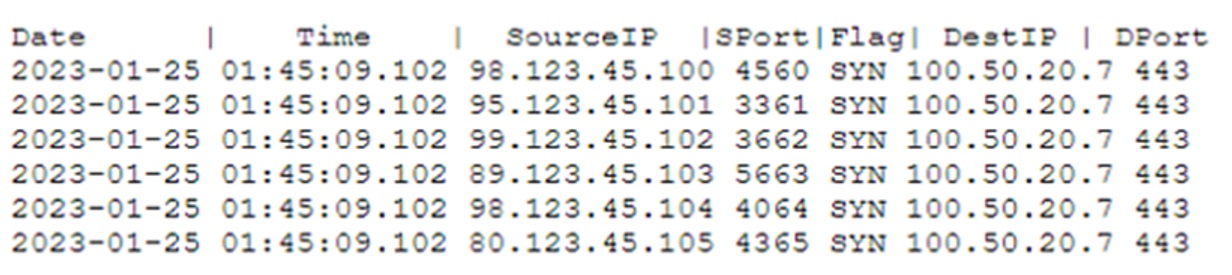
Which of the following attacks is likely occurring?
- A. DDoS
- B. Directory traversal
- C. Brute-force
- D. HTTPS downgrade
An organization would like to calculate the time needed to resolve a hardware issue with a server. Which of the following risk management processes describes this example?
- A.Recovery point objective
- B.Mean time between failures
- C.Recovery time objective
- D.Mean time to repair
A security engineer is installing an IPS to block signature-based attacks in the environment.
Which of the following modes will best accomplish this task?
- A. Monitor
- B. Sensor
- C. Audit
- D. Active
